Apple, Facebook, others defy authorities, increasingly notify users of secret data demands after Snowden revelations
Fueling the shift is the industry’s eagerness to distance itself from the government after last year’s disclosures about National Security Agency surveillance of online services. Apple, Microsoft, Facebook and Google all are updating their policies to expand routine notification of users about government data seizures, unless specifically gagged by a judge or other legal authority, officials at all four companies said. Yahoo announced similar changes in July. As this position becomes uniform across the industry, U.S. tech companies will ignore the instructions stamped on the fronts of subpoenas urging them not to alert subjects about data requests, industry lawyers say. Companies that already routinely notify users have found that investigators often drop data demands to avoid having suspects learn of inquiries. “It serves to chill the unbridled, cost-free collection of data,” said Albert Gidari Jr., a partner at Perkins Coie who represents several technology companies.
How to Import Web Data into Google Docs with ImportHTML
This video tutorial explains how you can import web data – like HTML tables and lists – from external web pages into your Google Docs sheets with a simple formula. You have been using Google Docs to create basic documents and spreadsheets but did you know that Google’s cloud-based Office suite can do even more. For instance, you can directly import data from web pages and edit it inside Google Docs.
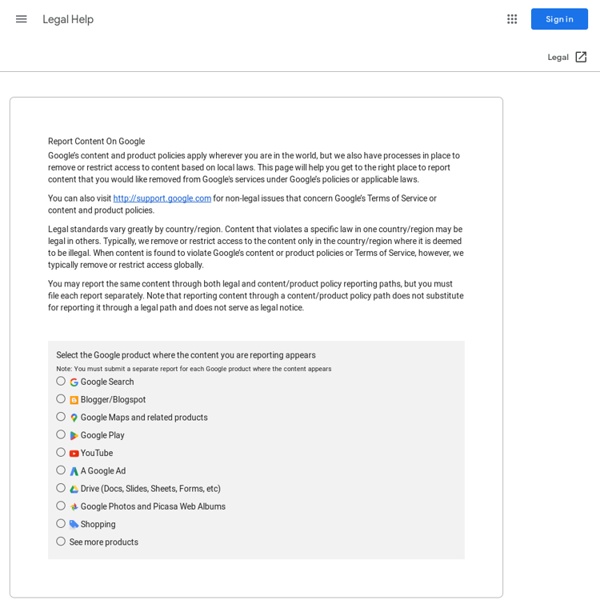
Legal Help
This page will help you get to the right place to report content that you would like removed from Google's services under applicable laws. Providing us with complete information will help us investigate your inquiry. If you have non-legal issues that concern Google's Terms of Service or Product Policies, please visit We ask that you submit a separate notice for each Google service where the content appears.
Online Privacy FAQ
Copyright © 2007 - 2014Privacy Rights Clearinghouse This FAQ is an addendum to our Fact Sheet 18 on Internet privacy.www.privacyrights.org/fs/fs18-cyb.htm It provides answers to questions that we are often asked by individuals who contact us concerning online privacy and safety. 1.
Google Apps Scripts Collection - The Best Google Scripts
Google Scripts offer programmatic access to most Google products including Gmail, Google Docs, Google Drive, Analytics, Google Contacts, Calendar, Maps and Google Analytics. The Google scripts are written in regular JavaScript language and they are hosted on Google’s servers. Here’s an always-updated collection of Google Scripts that will help you do more with your favorite Google products. And you don’t have to be programmer to use any of these scripts. Hire Google Apps Script Developer
THE BEST HACKING TOOLS AnonHQ
We at the Anonymous Headquarters have jotted down a list of tools that one requires for penetration testing, along with other hacking resources that are put together by some truly best programs in existence today. These tools can simplify many of the challenging jobs which require our immense time and constant coding – with these and more software available they take our painstaking tasks and make it easy. So, without further waiting, let us start off with list:- The Social-Engineer Toolkit Also highlighted on Mr. Robot, TrustedSec’s Social-Engineer Toolkit is definitely a state-of-the-art platform for replicating several varieties of social engineering strikes such as phishing attacks, credential harvestings plus a lot more.
OK Glass, RIP Privacy: The Democratization Of Surveillance
How’s this for synchronicity: Google Glass started shipping on the same week that CISPA passed the House, 3DRobotics unveiled their new site, and 4chan and Reddit pored over surveillance photos trying to crowdsource the identity of the Boston bombers. Cameras on phones. Cameras on drones.
You can now download your entire Google Search history
"Oh brilliant, now I can download my entire Google search history as one easy-to-read document," said no-one in the world, ever. Google has enabled a feature allowing users to collate every single desperate thing that they've ever searched for on a lonely Friday night, whether it's "is [insert ex-partner's name] married", "jellyfish porn" or "how big does a genital wart have to become before you call 999?". If, for some inexplicable reason, you would like to archive every last miserable shot in the dark you've fired out into the WWW, head over to the Google Account History page, where there is now the option to download a copy of your data and create an archive. Before users can download their search history, Google cautions them to read its warnings carefully because "it's not the usual yada yada". That's because your online archive doesn't just include embarassing search results – it can also include sensitive data and personal information.
Track Who’s Tracking You With Mozilla Collusion
LONG BEACH, Calif. — Mozilla CEO Gary Kovacs took the TED stage Tuesday morning to introduce Collusion, a Firefox browser add-on that lets you track who’s tracking you across the web for behavioral targeting purposes. Describing the medium as “an area of consumer protection that’s almost entirely naked,” Kovacs argued that the price we’re now being asked to pay for connectivenss is our privacy, and in turn, it’s “now time for us to watch the watchers.” Collusion looks to offer more transparency to users by creating a visualization of how your data is being spread to different companies as you navigate the web.