

Web Resources for Computer Networks, 5. Special thanks go to Andy Dornan for his help with this page.

CS_238, Data Communications and Computer Networks. Table of Contents. BOOKS BY WILLIAM STALLINGS. All my books and other Pearson books available via this Web site at a greater discount than online bookstores.

Go to discount book purchase. Useful Web Sites. Material Search Results. Computer Networking: Principles, Protocols, and Practice.
MAC Address Table. Tech TopX: Enterprise Networking 101 - Network Fabrics and Topology. Virtual LAN (VLAN) Virtual LAN. A virtual LAN (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer (OSI layer 2).[1][2] LAN is the abbreviation for local area network and in this context virtual refers to a physical object recreated and altered by additional logic.
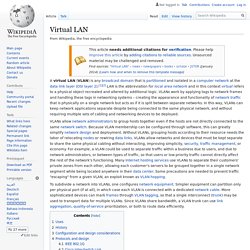
VLANs work by applying tags to network frames and handling these tags in networking systems – creating the appearance and functionality of network traffic that is physically on a single network but acts as if it is split between separate networks. In this way, VLANs can keep network applications separate despite being connected to the same physical network, and without requiring multiple sets of cabling and networking devices to be deployed. Uses[edit] In a network utilizing broadcasts for service discovery, address assignment and resolution and other services, as the number of peers on a network grows, the frequency of broadcasts also increases. History[edit]
Network Plus Certification. This wikibook discusses the information necessary to obtain the CompTIA Network+ certification.
Category:Network protocols. Firewall (computing) Fortinet. Systems Approach - Blog. For almost as long as there have been packet-switched networks, there have been ideas about how to virtualize them.
For example, there were early debates in the networking community about the merits of "virtual circuits" versus connectionless networks. But the concept of network virtualization has become more widespread in recent years, helped along by the rise of SDN as an enabling technology. Virtualization has a robust history in computer science, but there remains some confusion about precisely what the term means. Arguably this is due in part to confusion caused by colloquial usage of "virtual" as a synonym for "almost", among many other uses.Virtual memory provides an easy example to help understand what virtualization means in computing.
Internet-related lists. Computer Networks (CIS 345) Releases · SystemsApproach/book. Computer Networks: A Systems Approach — Computer Networks: A Systems Approach Version 6.2-dev documentation. Index — An Introduction to Computer Networks. Monirul Hoque. Sunny Classroom. Class B ID - Subnetting a A subnet is a logical subdivision of an IP network.
The process of dividing a network into two or more networks is called subnetting. In this video, I will use an example to demonstrate a simple way of subnetting. Some background links Example used in the video: One day your supervisor walks to you, saying: “here is the network ID 192.168.4.0/24, please create three separate networks or subnets for a coffee shop: Sunny Cafe.” Rick Graziani - Cabrillo College. Cabrillo College Office Hours Web Advisor Computer Networking Program Rick's Networking Links Non-Cabrillo Instructors/Students: My materials are now available without a username or password.
IPv6 Fundamentals: Second Edition (Book) By Rick Graziani, Published June 2017, Cisco Press IPv6 Fundamentals: A Straightforward Approach to Understanding IPv6 (Video Series) By Rick Graziani, Published Jan 15, 2015, Cisco Press. Rick Graziani.
Networking questions and exams. Computer Networking : Principles, Protocols and Practice. W. Richard Stevens' Home Page. W.

Richard Stevens' Home Page Books by Richard Stevens (reverse chronological) Papers by Richard Stevens (reverse chronological) Papers of Others (alphabetical) Some of the following are papers that I have referenced in my books, often Usenet postings, that are not easily obtainable. Typesetting This section contains some notes on how I write books. Miscellaneous Source Code This used to be a tar file containing the Posix.1g getaddrinfo() function that supports both IPv4 and IPv6.
IP Multicasting Information IP multicast API information. Biography. Keith W. Ross. Keith Ross is the Dean of Engineering and Computer Science at NYU Shanghai and the Leonard J.

Shustek Chair Professor of Computer Science at NYU. He also holds an affiliated appointment with the Department of Computer Science at the Courant Institute of Mathematical Sciences and with the Center for Data Science at NYU. Previously he was a professor at University of Pennsylvania (13 years) and a professor at Eurecom Institute (5 years). He was the Department Head of the CSE Department at NYU from 2008 to 2013, and he joined NYU Shanghai in 2013. Jim Kurose: homepage. With Keith Ross, I am the co-author of the textbook, Computer Networking: a Top Down Approach (Pearson), now in its 7th edition.

Since the publication of the first edition 16 years ago, the book has been adopted at many hundreds of colleges and universities, translated into 14 languages, and used by more than half a million students and practitioners worldwide. We’ve been overwhelmed by the positive response. Our publisher's page for the 7th edition of our book is here; the Amazon page is here (7th edition; 6th edition).
There are a number of resources that we make freely available to the community (students, teachers, and readers): Powerpoint slides. Computer Networks and Internet Protocol. Introduction to EECS II: Digital Communication Systems.
Juniper Networks. Dual-homed. An example of dual-homed devices are enthusiast computing motherboards that incorporate dual Ethernet network interface cards. Usage[edit] In Ethernet LANs, dual-homing is a network topology whereby a networked device is built with more than one network interface.
Each interface or port is connected to the network, but only one connection is active at a time. The other connection is activated only if the primary connection fails. Traffic is quickly rerouted to the backup connection in the event of link failure. In firewalls[edit] Classless Inter-Domain Routing. A method for IP address allocation and routing IP addresses are described as consisting of two groups of bits in the address: the most significant bits are the network prefix, which identifies a whole network or subnet, and the least significant set forms the host identifier, which specifies a particular interface of a host on that network. This division is used as the basis of traffic routing between IP networks and for address allocation policies. Whereas classful network design for IPv4 sized the network prefix as one or more 8-bit groups, resulting in the blocks of Class A, B, or C addresses, Classless Inter-Domain Routing allocates address space to Internet service providers and end users on any address-bit boundary.
In IPv6, however, the interface identifier has a fixed size of 64 bits by convention, and smaller subnets are never allocated to end users. CIDR encompasses several concepts. Background[edit] CIDR notation[edit] Palo Alto Networks Live Community.
CosmoLearning Computer Science. CosmoLearning Computer Science. An Introduction to Computer Networks. Data Communication Networks. Beauty and Joy of Computing. In this course, you will create programs using the snap programming language, you will learn some of the most powerful ideas of computer science, you will be creative, and you will discuss the social implications of computing, thinking deeply about how you can be personally active in promoting the benefits and reducing the possible harms. These are the minimum specifications for running Snap! Units 1-6 cover all of the AP CSP curriculum framework. You are ready for the exam. Units 7 and 8 focus on recursion, a beautiful and powerful CS idea that goes beyond the AP CSP Framework and exam. These units are perfect to enjoy after the exam. Introduction to Computer Applications and Concepts. Introduction One of the fastest growing technology areas is that of telecommunications (often referred to as telecoms).
Organizations have realized that stand-alone computers present many problems: fragmentation of data, lack of control, insufficient integration and limited opportunity for teamwork. One of the major trends over the last decade has been the move not only to have a personal computer on the desk of virtually every knowledge worker, but to have that computer linked to the other computers in the organization. Computer and Network Surveillance. Open Access publishing movement started in early 2000s, when the academic leaders from around the world participated in the formation of the Budapest Initiative. They developed recommendations for Open Access publishing process “which has worked for the past decade to provide the public with unrestricted, free access to scholarly research—much of which is publicly funded. Effective Planning and Analysis of Huawei and Cisco Routers for MPLS Network Design Using Fast Reroute Protection.
1. The Internet. ONS 15454 Reference Manual, Release 4.6 - Chapter 11, SONET Topologies [Cisco ONS 15454 Series Multiservice Provisioning Platforms] SONET Topologies This chapter explains Cisco ONS 15454 SONET topologies. Transmission time. Packet transmission time = Packet size / Bit rate.
Computer Science and Engineering - Computer Networks. Junos vs IOS. Cisco. Network search (whois, ip etc.) Networking tools. TCP/IP Definitions. By Candace Leiden, Marshall Wilensky. Network Troubleshooting Tools. By Glen E. Clarke, Edward Tetz, Timothy Warner The following is a listing of some common troubleshooting tools you should be familiar with for the A+ Exams. Autonomous system (Internet) Generic Routing Encapsulation. Example uses[edit] In conjunction with PPTP to create VPNs.In conjunction with IPsec VPNs to allow passing of routing information between connected networks.In mobility protocols.In A8/A10 interfaces to encapsulate IP data to/from Packet Control Function (PCF).Linux and BSD can establish ad-hoc IP over GRE tunnels which are interoperable with Cisco equipment.Distributed denial of service (DDoS) protected appliance to an unprotected endpoint.
Connected: An Internet Encyclopedia. Lecture - Networking. The Next WiFi Rockstar by NSA Show. EtherealMind - Software Defined Networking, Data Centre and Infrastructure. Tech search engines. Physical Layer. Computer networking - Vocabulary List. Local area network (LAN) Cisco Security Appliance Command Line Configuration Guide, Version 8.0 - Glossary [Cisco ASA 5500-X Series Next-Generation Firewalls] Security association. An instance of security policy and keying material applied to a data flow. SAs are established in pairs by IPSec peers during both phases of IPSec. SAs specify the encryption algorithms and other security parameters used to create a secure tunnel. Welcome to Network World.com.
How to Configure a Cisco Vpn: 8 Steps. Network emulation. Network Layer. Network simulation. Computer Network and Communications. Switches, Routers, Bridges and LANs. ICTs: device to device communication. This unit looks at communication systems where devices are the main players, passing information to and from each other and possibly acting on that information to produce some kind of outcome. In these interactions, people may not be involved at all, or may have roles that are limited only to the initial setting of schedule (such as when certain tasks should be performed) and parameters (such as particular conditions that should be satisfied before a task is performed). Some people may see this as liberating – relieving humans from the tedious tasks of everyday living. Some may see it as threatening – taking control away from humans and placing it with the computers and machines. How do devices ‘talk’ to each other? Digital communications - OpenLearn - Open University - T305_1. Articles.
Netstat. Using the ping command. Linktionary Major Topics Index. IPv6. IPv4. Differentiated services. Explicit Congestion Notification. CS402: Computer Communications and Networks. Computer Networking: Principles, Protocols, and Practice (Release 0.25) Welcome to The TCP/IP Guide!
List of TCP and UDP port numbers. Application layer protocols. Computer Sc - Internet Technologies. Computer Science and Engineering - Computer Networks.