

Run Your Own Email Server on CentOS 8/RHEL 8 - Postfix SMTP Server. Why run your own email server?
Perhaps you have a website, which needs to send emails to users, or maybe you want to store your emails on your own server to protect your privacy. However, building your own email server from scratch can be a pain in the butt because there are so many software components you need to install and configure properly. Run Your Own Email Server on CentOS 8/RHEL 8 - Postfix SMTP Server. Online regex tester and debugger: PHP, PCRE, Python, Golang and JavaScript. Git on the commandline — Don't be afraid to commit 0.3 documentation. So far we’ve done all our Git work using the GitHub website, but that’s usually not the most appropriate way to work.
You’ll find that most of your Git-related operations can and need to be done on the commandline. Install/set up Git¶ sudo apt-get install git # for Debian/Ubuntu usersbrew install git # for Mac OS X users with Homebrew installed There are other ways of installing Git; you can even get a graphical Git application, that will include the commandline tools. NSX-T Command-Line Interface Reference. Copyright © 2014-2018 VMware, Inc.

All rights reserved. Copyright and trademark information. NSX-T Data Center 2.3.0 About This Book The NSX-T Command-Line Interface Reference describes how to use the NSX-T Command-Line Interface (CLI) and includes examples and command overviews. Gdb Debugging Full Example (Tutorial): ncurses. I'm a little frustrated with finding "gdb examples" online that show the commands but not their output. gdb is the GNU Debugger, the standard debugger on Linux.
I was reminded of the lack of example output when watching the Give me 15 minutes and I'll change your view of GDB talk by Greg Law at CppCon 2015, which, thankfully, includes output! It's well worth the 15 minutes.
Allow `allow_local_requests_from_hooks_and_services` to be set via API (#55605) · Issues · GitLab.org / GitLab Community Edition. Help! Linux ate my RAM! LinuxCommand.org: tput. While our command line environment is certainly powerful, it can be be somewhat lacking when it comes to visual appeal.
Our terminals cannot create the rich environment of the graphical user interface, but it doesn't mean we are doomed to always look at plain characters on a plain background. In this adventure, we will look at tput, a command used to manipulate our terminal. With it, we can change the color of text, apply effects, and generally brighten things up. More importantly, we can use tput to improve the human factors of our scripts.
For example, we can use color and text effects to better present information to our users. Availability tput is part of the ncurses package and is supplied with most Linux distributions. What It Does/How It Works Long ago, when computers were centralized, interactive computer users communicated with remote systems by using a physical terminal or a terminal emulator program running on some other system.
Kubernetes. Apiman Open Source API Management. In this section, we’ll also take a very hands-on look at apiman.
In about 10 minutes, we’ll get apiman installed and running, define an API policy, create and publish an API, register an application, and watch apiman enforce that policy. Let’s start by installing the prerequisite software packages that we will need. To download apiman, open a browser and navigate to The phrase “running an apiman server” is a bit misleading, as apiman itself is not a server. apiman is distributed in multiple forms. Ch14 : Linux Firewalls Using iptables. Network security is a primary consideration in any decision to host a website as the threats are becoming more widespread and persistent every day.
One means of providing additional protection is to invest in a firewall. Though prices are always falling, in some cases you may be able to create a comparable unit using the Linux iptables package on an existing server for little or no additional expenditure. This chapter shows how to convert a Linux server into: Explainshell.com - iptables -A. Java Keytool Essentials: Working with Java Keystores. Introduction Java Keytool is a key and certificate management tool that is used to manipulate Java Keystores, and is included with Java.

The Most Common Java Keytool Keystore Commands. Anatomy of SSSD user lookup – jhrozek. This blog post describes how a user lookup request is handled in SSSD.
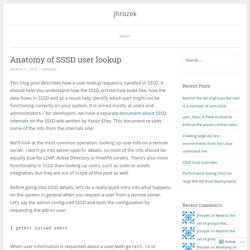
It should help you understand how the SSSD architecture looks like, how the data flows in SSSD and as a result help identify which part might not be functioning correctly on your system. It is aimed mostly at users and administrators – for developers, we have a separate document about SSSD internals on the SSSD wiki written by Yassir Elley. This document re-uses some of the info from the internals one. We’ll look at the most common operation, looking up user info on a remote server. I won’t go into server-specific details, so most of the info should be equally true for LDAP, Active Directory or FreeIPA servers. A tcpdump Tutorial and Primer with Examples. Small getopts tutorial. Description When you want to parse command line arguments in a professional way, getopts is the tool of choice.
Unlike its older brother getopt (note the missing s!) , it's a shell builtin command. The advantages are: Processing messages stuck in the disk queue files of syslog-ng Premium Edition. Problem When you change the configuration of a syslog-ng PE host that uses disk-based buffering (also called dis queue), syslog-ng PE may start new disk buffer files for the destinations that you have changed. In such case, syslog-ng PE abandons the old disk queue files. If there were unsent log messages in the disk queue files, these messages remain in the disk queue files, and will not be sent to the destinations. SSL Certificates HOWTO. Set Operations in the Unix Shell Simplified - good coders code, great coders reuse. Remember my article on Set Operations in the Unix Shell? I implemented 14 various set operations by using common Unix utilities such as diff, comm, head, tail, grep, wc and others. I decided to create a simpler version of that post that just lists the operations.
I also created a .txt cheat-sheet version of it and to make things more interesting I added an Awk implementation of each set op. If you want a detailed explanations of each operation, go to the original article. Download .txt right away: set operations in unix shell (.txt) Download path: Understanding the Top command on Linux. 15 simple TOP command examples on Linux to monitor processes. Linux TOP command One of the most basic command to monitor processes on Linux is the top command. As the name suggests, it shows the top processes based on certain criterias like cpu usage or memory usage. The processes are listed out in a list with multiple columns for details like process name, pid, user, cpu usage, memory usage. MichielDerhaeg/build-linux: A short tutorial about building Linux based operating systems. Advanced Bash-Scripting Guide. An in-depth exploration of the art of shell scripting Mendel Cooper 10 Mar 2014.
Sort Files Like A Master With The Linux Sort Command (Bash) If you do your development work in Linux, there are certain commands that you owe it to yourself to master fully. There are a number of these with the main ones being grep, find and sort. Bash:tip_colors_and_formatting - FLOZz' MISC. The ANSI/VT100 terminals and terminal emulators are not just able to display black and white text ; they can display colors and formatted texts thanks to escape sequences.
Those sequences are composed of the Escape character (often represented by “^[” or “<Esc>”) followed by some other characters: “<Esc>[FormatCodem”. In Bash, the <Esc> character can be obtained with the following syntaxes: \e \033 \x1B Examples: NOTE¹: The -e option of the echo command enable the parsing of the escape sequences.
NOTE²: The “\e[0m” sequence removes all attributes (formatting and colors). Manipulating Strings. Extracts substring from $string at $position. If the $string parameter is "*" or "@", then this extracts the positional parameters, starting at $position. Extracts $length characters of substring from $string at $position. Manipulating Strings. MichielDerhaeg/build-linux. Linux PAM Easy Guide - Like Geeks. Regular Expressions. HOWTO_Troubleshoot_SUDO – SSSD. Check if configuration of sudo and SSSD cooperation is correct ¶ To check whether the basic configuration of sudo and SSSD is correct, check /etc/nsswitch.conf and /etc/sssd/sssd.conf files. /etc/nsswitch.conf must say that sss module is used for sudo service.
Parameter expansion. Lesson 8: Expansion. Screen. Introduction to if. 7.1.1. General At times you need to specify different courses of action to be taken in a shell script, depending on the success or failure of a command. The if construction allows you to specify such conditions. Aide-mémoire des commandes Linux. Sed - An Introduction and Tutorial.
How to Extend/Reduce LVM's (Logical Volume Management) in Linux - Part II. Linux/Documentation at master · torvalds/linux. Linux/vm.txt at master · torvalds/linux. Introduction to Linux.