

Batching Linux syscalls. Compilers often inline functions to save the overhead of saving and restoring registers and stack as well as the jump into the function and its associated likely page fault.
Function call overhead is nothing compared to syscalls (cost estimates range from 20x to 100x that of a simple function call). That is every single time any syscall is made because much more data/registers/etc... need to be saved for a user to kernel mode switch. You can't just not use them, but perhaps there is a partial solution. Often multiple syscalls need to be made together and are separate from other code (open+read/write+close or dealing with sockets). It stands to reason the that it could be a big win to take care of as many syscalls as possible during a single user-kernel mode switch. I'm thinking of something akin to socketcall except taking 3 arguments: an array for return values, an array for the syscalls number and args and a flags arg to do things like set it to return on the first error.
How System Calls Work on Linux/i86. The HyperNews Linux KHG Discussion Pages This section covers first the mechanisms provided by the 386 for handling system calls, and then shows how Linux uses those mechanisms.
This is not a reference to the individual system calls: There are very many of them, new ones are added occasionally, and they are documented in man pages that should be on your Linux system. What Does the 386 Provide? The 386 recognizes two event classes: exceptions and interrupts. Both cause a forced context switch to new a procedure or task. Two sources of interrupts are recognized by the 386: Maskable interrupts and Nonmaskable interrupts. Each interrupt or exception has a number, which is referred to by the 386 literature as the vector.
The priority of simultaneous interrupts and exceptions is: How Linux Uses Interrupts and Exceptions. Kernel command using Linux system calls. A system call is an interface between a user-space application and a service that the kernel provides.

Because the service is provided in the kernel, a direct call cannot be performed; instead, you must use a process of crossing the user-space/kernel boundary. The way you do this differs based on the particular architecture. For this reason, I'll stick to the most common architecture, i386. In this article, I explore the Linux SCI, demonstrate adding a system call to the 2.6.17 and prior 2.6 kernels, and then use this function from user-space. I also investigate some of the functions that you'll find useful for system call development and alternatives to system calls. The SCI The implementation of system calls in Linux is varied based on the architecture, but it can also differ within a given architecture. You needn't fully understand the internals of the SCI to amend it, so I explore a simple version of the system call process (see Figure 1).
Figure 1. Figure 2. Back to top Listing 1. The Linux kernel: System Calls. NextPreviousContents 4.

Adding A System Call. 1.

About This Document This document explains a way to add a system call to linux kernel. A system call is the standard way an OS service is exported to a user program. For example, to provide users a new semaphore like synchronization method, some system calls need to be provided to access it. Likewise, a system call may be used to give users access to internal information of a file system such as superblock or inodes. 2. A system call cannot be called directly from a user process. .data ENTRY(sys_call_table) .long SYMBOL_NAME(sys_ni_call) /* 0 */ .long SYMBOL_NAME(sys_exit) .long SYMBOL_NAME(sys_fork) ... .long SYMBOL_NAME(sys_vfork) /* 190 */ After the "sys_vfork" line, add your entries for your new system calls, with the words "sys_" prepended. .long SYMBOL_NAME(sys_myservice) /* 191 */
System call. A high-level overview of the Linux kernel's system call interface, which handles communication between its various components and the userspace In most systems, system calls are possible to be made only from userspace processes, while in some systems, OS/360 and successors for example, privileged system code also issues system calls.[1] Privileges[edit] However, many normal applications obviously need access to these components, so system calls are made available by the operating system to provide well defined, safe implementations for such operations.
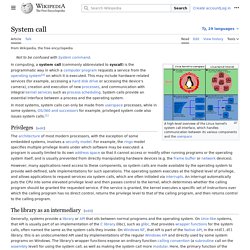
The operating system executes at the highest level of privilege, and allows applications to request services via system calls, which are often initiated via interrupts. An interrupt automatically puts the CPU into some elevated privilege level, and then passes control to the kernel, which determines whether the calling program should be granted the requested service. The library as an intermediary[edit] Examples and tools[edit] See also[edit] Kernel Hacking Lesson #7: Understanding System Calls. By now, you're probably looking around at device driver code and wondering, "How does the function foo_read() get called?

" Or perhaps you're wondering, "When I type cat /proc/cpuinfo, how does the cpuinfo() function get called? " Once the kernel has finished booting, the control flow changes from a comparatively straightforward "Which function is called next? " to being dependent on system calls, exceptions, and interrupts. Today, we'll talk about system calls. Syscalls(2) - Linux manual page.