

Virtual private cloud. Sales process. A sales process is an approach to selling a product or service.
The sales process has been approached from the point of view of an engineering discipline (see sales process engineering).[1] Rationale[edit] Reasons for having a well-thought-out sales process include seller and buyer risk management, standardized customer interaction during sales, and scalable revenue generation. Preboot Execution Environment. Un article de Wikipédia, l'encyclopédie libre.
L'image ainsi récupérée peut être le système d'exploitation brut ou bien le système d'exploitation personnalisé avec des composantes logicielles (suite bureautique, utilitaires, packs de sécurité, scripts, etc.). Libvirt. Troll (Internet) Un article de Wikipédia, l'encyclopédie libre.
En argot Internet, un troll est un internaute qui laisse des messages (par exemple sur un forum) dont le caractère est susceptible de provoquer des polémiques, ou auquel on ne veut pas répondre et qu'on tente de discréditer en le nommant ainsi. Debconf (software package) Debconf is a software utility for performing system-wide configuration tasks on Unix-like operating systems.
It is developed for the Debian GNU/Linux distribution, and is closely integrated with Debian's package management system, dpkg. When packages are being installed, debconf asks the user questions which determine the contents of the system-wide configuration files associated with that package. After package installation, it is possible to go back and change the configuration of a package by using the dpkg-reconfigure program, or another program such as Synaptic.
Debconf does not physically configure any packages, but asks the user certain configuration questions stored in the .templates file, under the direction of the package's maintainer scripts (.config, .postinst, etc.). Jump up ^ The GNOME Journal: Simplified Package Management in Ubuntu Hoary. The Mythical Man-Month. The Mythical Man-Month: Essays on Software Engineering is a book on software engineering and project management by Fred Brooks, whose central theme is that "adding manpower to a late software project makes it later".
This idea is known as Brooks' law, and is presented along with the second-system effect and advocacy of prototyping. Brooks' observations are based on his experiences at IBM while managing the development of OS/360. He had added more programmers to a project falling behind schedule, a decision that he would later conclude had, counter-intuitively, delayed the project even further. He also made the mistake of asserting that one project — writing an ALGOL compiler — would require six months, regardless of the number of workers involved (it required longer). Chef puppet vagrant ansible. SugarSync. The program automatically refreshes its sync by constantly monitoring changes to files—additions, deletions, edits—and syncs these changes with any other linked devices as well as the SugarSync servers.[1] Originally offering a free 5GB plan and several paid plans, the company transitioned to a paid-only model on February 8th, 2014.
Hypervisor. A hypervisor or virtual machine monitor (VMM) is a piece of computer software, firmware or hardware that creates and runs virtual machines.
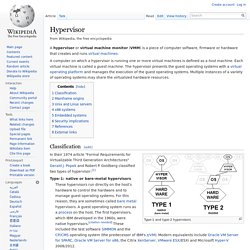
A computer on which a hypervisor is running one or more virtual machines is defined as a host machine. Each virtual machine is called a guest machine. The hypervisor presents the guest operating systems with a virtual operating platform and manages the execution of the guest operating systems. Multiple instances of a variety of operating systems may share the virtualized hardware resources. Wikipedia Real time billing. NX technology. NX technology is a computer program that handles remote X Window System connections, and attempts to greatly improve on the performance of the native X display protocol to the point that it can be usable over a slow link such as a dial-up modem.
It wraps remote connections in SSH sessions for encryption. NoMachine is a privately owned company based in Luxembourg with representative offices located in the United States and Germany and multiple R&D sites around Europe. The NX scheme was derived from that of DXPC – the Differential X Protocol Compressor project.[1] NX software is currently available for Windows, Mac OS X, Linux, and Solaris. NoMachine has clients available for Windows and Mac OS X, and Google makes a freely available Open Source GPL2 version of the server called Neatx. Institut Mines-Télécom. Île-de-France Clusters. The Ile-de-France has eight clusters[1] among 71 approved by the Comité interministériel d'aménagement et de développement du territoire[2] (CIADT, Interdepartmental Committee on Planning and Land Development).[3] The first four were approved by the CIACT the 14th of October 2005.
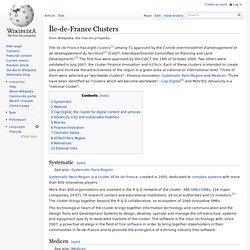
Two others were validated in July 2007: the cluster Finance Innovation and ASTech. Each of these clusters is intended to create jobs and increase the attractiveness of the region in a given area at national or international level. Three of them were selected as "worldwide clusters" : Finance Innovation, Systematic Paris-Region and Medicen. Pôles de compétitivité en Île-de-France. Service d'information du gouvernement. Un article de Wikipédia, l'encyclopédie libre.
Triangle dramatique. Un article de Wikipédia, l'encyclopédie libre. Le triangle dramatique, dit aussi triangle de Karpman, est une figure d'analyse transactionnelle proposée par Stephen Karpman en 1968 (dans son article Fairy Tales and Script Drama Analysis) qui met en évidence un scénario relationnel typique entre victime, persécuteur et sauveur (ces rôles étant symboliques, une même personne peut changer de rôle). Burstable billing. Most ISPs use a five minute sampling and 95% usage when calculating usage. 95th percentile[edit] The 95th percentile is a widely used mathematical calculation to evaluate the regular and sustained use of a network connection. The 95th percentile method more closely reflects the needed capacity of the link in question than tracking by other methods such as mean or maximum rate. The bytes that make up the packets themselves do not actually cost money, but the link and the infrastructure on either end of the link cost money to set up and support.
This method of billing is commonly used in peering arrangements between corporate networks, it is not often used by ISPs because Internet Service Providers need Committed Information Rates (CIRs) for planning purposes. Many sites have the majority of their traffic on Mondays, so the Monday traffic determines the rate for the whole month. Vagrant (software) Tool Command Language. Un article de Wikipédia, l'encyclopédie libre. Pour les articles homonymes, voir Tcl. Comparison of open-source configuration management software. This is a comparison of notable free and open source configuration management software, suitable for tasks typically performed by a system administrator. Basic properties[edit] "Verify mode" refers to having an ability to determine whether a node is conformant with a guarantee of not modifying it, and typically involves the exclusive use of an internal language supporting read-only mode for all potentially system-modifying operations.
Platform support[edit] Note: This means platforms on which a recent version of the tool has actually been used successfully, not platforms where it should theoretically work since it's written in good portable C/C++ or an interpreted language. Atempo Time Navigator. Enterprise Vault. Symantec Enterprise Vault (EV) is an enterprise file and email archiving program created by Symantec. It is part of the company's "Information Foundation" suite.[1] Enterprise Vault has the ability to archive from various sources such as Microsoft Exchange (2013, 2010, 2007,2003), SMTP (any), IBM Domino (latest released), Microsoft Sharepoint and various File Systems (NTFS, Unix) with the ability to store on a multiple of storage platforms, such as; NTFS, NetApp, Centera, CIFS and WORM.[2] The data archived is indexed, classified, de-duplicated and securely stored.
History[edit] Enterprise Vault was originally developed at Digital Equipment Corporation (DEC) by a group of developers who had previously been the engineering team for Digital's VMS based ALL-IN-1 office and messaging system. After DEC was acquired by Compaq Computer Corporation the Enterprise Vault team was terminated just after Version 1 of the product was shipped. Defense in depth (computing) Defense in depth is an information assurance (IA) concept in which multiple layers of security controls (defense) are placed throughout an information technology (IT) system. Its intent is to provide redundancy in the event a security control fails or a vulnerability is exploited that can cover aspects of personnel, procedural, technical and physical for the duration of the system's life cycle.
The idea behind the defense in depth approach is to defend a system against any particular attack using several independent methods. It is a layering tactic, conceived by the National Security Agency (NSA) as a comprehensive approach to information and electronic security.[1][2] Defense in depth is originally a military strategy that seeks to delay, rather than prevent, the advance of an attacker by yielding space in order to buy time. Using more than one of the following layers constitutes defense in depth. Wingz (company) Wingz (formerly known as Tickengo) is a company that operates a web and mobile-based real-time ridesharing service for airport transportation. The company is headquartered near San Francisco, California.[1][2] Wingz was founded by Geoff Mathieux, Jeremie Romand, and Fred Gomez.
It provides rides to the airport scheduled in advance.[3] It holds a pending utility patent for its scheduled rides technology. In November 2013, California regulators formally legalized ridesharing services like Wingz, classifying them as Transportation Network Companies. Joyn. Leapfrogging. The concept of leapfrogging was originally used in the context of economic growth theories and industrial-organization innovation studies with specific focus on competition among firms. Université Paris-Sud. Réseau social d'entreprise. Espace numérique de travail. Data science. PEST analysis. SPSS. Human resource management. Hardware Security Module. Hierarchical storage management. Chorus (logiciel) Unbundling. Presales.
Solutions Architect.