


64 Things Every Geek Should Know « Caintech.co.uk If you consider yourself a geek, or aspire to the honor of geekhood, here’s an essential checklist of must-have geek skills. The term ‘geek’, once used to label a circus freak, has morphed in meaning over the years. What was once an unusual profession transferred into a word indicating social awkwardness. As time has gone on, the word has yet again morphed to indicate a new type of individual: someone who is obsessive over one (or more) particular subjects, whether it be science, photography, electronics, computers, media, or any other field. A geek is one who isn’t satisfied knowing only the surface facts, but instead has a visceral desire to learn everything possible about a particular subject. A techie geek is usually one who knows a little about everything, and is thus the person family and friends turn to whenever they have a question.
How To… Embed This Infographic <a href= "><img src=" title="10 How Tos" alt="How To Infographic" border="0" class="nopin" /></a><br />Source: <a href=' title='Interesting Facts'><a href=' title='Interesting Facts'>Today I Found Out</a></a> 1) How to drastically increase the life of your shaving razor Why it’s hard to be a highly sensitive (HSP) introvert A handful of years ago I was so relieved to discover that there's a name (Highly Sensitive Person, aka HSP) for what I thought were uniquely weird sensitivities. I also finally understand and now even celebrate the fact that I'm highly introverted . Thanks to these new insights into my personality , I've come to appreciate that the traits that make me seem "strange" are also the reasons that I'm an effective personal coach and a successful writer and author. For most of my life I felt that if people knew what I was really like, they'd write me off as strange or different.
Painfully Computer Pranks ~ Computer Hacking Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank). Today , I will show you 5 great computer pranks that will frustrate your victims very much. ccna practice questions Disclaimer: All Simulation Exams practice tests, study guides and/or material are neither sponsored by, nor endorsed by, nor affiliated with Cisco® Systems, Inc., Microsoft® Corporation, Inc., CompTIA® , Check Point Software Corp., Prosoft® or any other company. All trademarks are trademarks of their respective owners and duly acknowledged. MCSE ™, MCSE+I ™ are registered trademarks of Microsoft® Corporation and CCNA™, CCNP™, CCIE™ are registered trade marks of Cisco® Systems.
Soda Machine Hack Most modern vending machines have little computers inside. A tiny screen usually displays some information. Although relatively little known, pressing a certain combinations of buttons can control the settings. For instance, you can check the internal temperature, view the amount of money inside, empty change, or dump certain beverages.
How-To: Easily Remove the Vocals from Most Songs 2015 Shortcut: When I wrote this article Audacity didn’t have an automatic center-panned vocal canceling effect… but now it does, so rather than do the stereo-separate / invert-one-track / play-both-as-mono trick (and that’s pretty much all there is to it), you should be able to find the Vocal Remover option in the Effects menu – but it’s more fun / interesting and can give better results if you do it yourself! =D I found this trick the other day whilst stumbling the Interwebs and thought I’d do a quick-write up w/ pictures to make it as easy as possible… For this exercise we’re going to be using a piece of free audio software called Audacity, which you can get for Linux, Windows and Mac. Update: If you’re trying this out on a Mac, please make sure you get Audacity 1.3 Beta or newer – the stable 1.2 version appears to have a missing equaliser decibal-range slider which you need towards the end of the process! 1.)
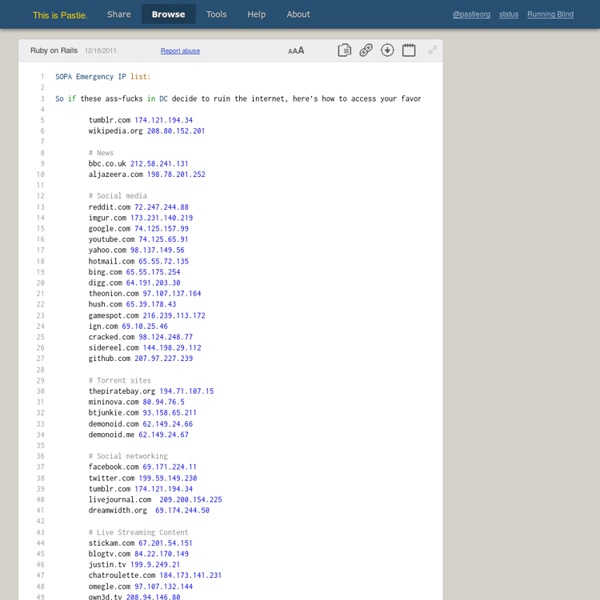
#3038363 SOPA Emergency IP list: So if these ass-fucks in DC decide to ruin the internet, here’s how to access your favorite sites in the event of a DNS takedown tumblr.com 174.121.194.34 wikipedia.org 208.80.152.201 # News bbc.co.uk 212.58.241.131 aljazeera.com 198.78.201.252 # Social media reddit.com 72.247.244.88 imgur.com 173.231.140.219 google.com 74.125.157.99 youtube.com 74.125.65.91 yahoo.com 98.137.149.56 hotmail.com 65.55.72.135 bing.com 65.55.175.254 digg.com 64.191.203.30 theonion.com 97.107.137.164 hush.com 65.39.178.43 gamespot.com 216.239.113.172 ign.com 69.10.25.46 cracked.com 98.124.248.77 sidereel.com 144.198.29.112 github.com 207.97.227.239 # Torrent sites thepiratebay.org 194.71.107.15 mininova.com 80.94.76.5 btjunkie.com 93.158.65.211 demonoid.com 62.149.24.66 demonoid.me 62.149.24.67
Removing an object on a photo with GIMP Tutorial to remove objects (or people) and restore the portion of the background they hide in a photo with the Resynthesizer plugin. An impressive video has been posted on Youtube to show how, with Photoshop, it is possible to delete objects in an image automatically, without any design work. The same can be done with The Gimp in fact and for longer (it is not impossible that the same algorithm has been reused). This plugin "re-synthesizes" the background" and rebuilds it from same elements on the photo. It can thus reconstruct the sky, lawn, or even more complex views, from a sample taken from the image. First, see the Resynthesizer tutorial to know the purpose of controls.
How to Get Started With CSS I've already discussed how you can learn to code for free using languages such as Ruby and JavaScript, but this time we'll explore an even more basic language that can help to make your websites pop. Cascading Style Sheets is like HTML's cooler, more artistic sibling: While HTML handles the structure and content of your website, CSS allows you to add cutting-edge design to it. This guide tells you everything you need to know to get started making better-looking websites fast.
ANONYMITY & PRIVACY [ English | German ] Protection of Privacy on the Internet JAP (called JonDo in the scope of the commercial JonDonym anonymous proxy servers - AN.ON remains free of charge) makes it possible to surf the internet anonymously and unobservably. Without Anonymization, every computer in the internet communicates using a traceable Address. That means: the website visited, the internet service provider (ISP), and any eavesdropper on the internet connection can determine which websites the user of a specific computer visits. 100+ Sites to Download All Sorts of Things These days you can find all sorts of things online, from audio books to flash files, from sound effects to CSS templates. Below we compiled a list with over 100 download sites that serve that purpose. We will also try to keep the list updated, so if your favorite download site is not here, let us know about it with a comment. Audio Books Librivox: One of the most popular audio libraries on the web. The LibriVox volunteers record books that are in the public domain and release them for free.
60 of the world's happiest facts 1. A group of flamingos is called a flamboyance. 2. If you fake laugh long enough you’ll start to really laugh, really, really hard. 3. The book cover to the prize winning short story collection, Spellbound, was chosen because author, Joel Willans, bought his wife’s engagement ring with poker winnings. 6 Books Every Programmer Should Own I’ve seen many lists about the best programming books and I am sure there are a lot of books that are specific to a programming knowledge or technology – that I have not included in my list. The books I have chosen are those that are meant to inspire, increase productivity and improve your programming design skills. Note: This list has no particular order. Code Complete 2