


Keepass Tech: Itt a nagy átverős lista: weboldalak, melyeknek soha ne higgyen el semmit - HVG.hu Szeretne azonnal értesülni a legfontosabb hírekről? Learn Moana: Wayfinding with Code Grades 2+ | Blocks Minecraft Hour of Code Make Music with Scratch Grades 2-8 | Blocks, Scratch Gumball's Coding Adventure Grades 6-8 | Blocks, Scratch Vidcode: Code the News Grades 6+ | JavaScript Kodable (pre-readers welcome) Pre-reader - Grade 5 | Blocks | All modern browsers, iPad app Star Wars: Building a Galaxy with Code Grades 2+ | Blocks, JavaScript Adventure on the High Seas Code with Anna and Elsa Animate Your Name with Scratch CodeCombat Grades 2+ | JavaScript, Python, Lua, CoffeeScript Play Lab Box Island All ages | Blocks codeSpark Academy with The Foos Pre-reader - Grade 5 | Blocks Kano Pixel Hack Grades 2+ | JavaScript, Coffeescript Dragon Dash Grades 2-8 | Blocks Make it Fly with Scratch Analog Clock STEM Kit Grades 6+ | Blocks Vidcode: Bestie Greeting Card Grades 2+ | JavaScript Spritebox Coding Grades 2-8 | Blocks, Java, iOS/Swift Python Turtle Graphics Grades 6+ | Python Lightbot Write your first computer program Khan Academy: Drawing with Code ITCH Bouncing Ball (in Scratch)
Macbeth Quotes Fair is foul, and foul is fair. --Witches, Act I, scene i Fortune, on his damned quarrel smiling, Showed like a rebel's whore. --Captain, Act I, scene ii If you can look into the seeds of time, And say which grain will grow, and which will not, Speak. --Banquo, Act I, scene iii And oftentimes, to win us to our harm, The instruments of darkness tell us truths, Win us with honest trifles, to betray's In deepest consequence. If chance will have me king, why, chance may crown me. --Macbeth, Act I, scene iii There's no art to find the mind's construction in the face. --Duncan, Act I, scene iv Nothing in his life Became him like the leaving it; he died As one that had been studied in his death, To throw away the dearest thing he ow'd, As 'twere a careless trifle. --Malcolm, Act I, scene iv Stars, hide your fires! --Macbeth, Act I, scene iv Glamis thou art, and Cawdor; and shalt be What thou art promised. --Lady Macbeth, Act I, scene v Come, you spirits That tend on mortal thoughts! What's done is done.
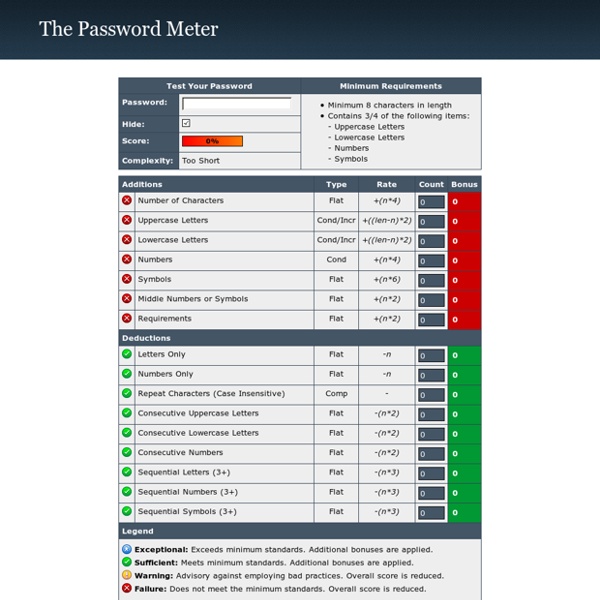
Choisir, sécuriser et gérer ses mots de passe Webmails, forums, réseaux sociaux, banques en ligne : le point commun entre ces différentes applications est l'accès sécurisé par mot de passe. Avec la multiplication des comptes d'utilisateurs nécessitant une authentification, ces derniers sont de plus en plus difficiles à mémoriser. Pourtant, le choix de mots de passe complexe est crucial, à l'heure où les techniques d'ingénierie sociale sont en plein essor. Avec quelques conseils de base, et des outils pratiques, il est assez facile de bien choisir, sécuriser et gérer ses mots de passe. Comment choisir un mot de passe ? Il n'existe pas de "recette" permettant de sécuriser à 100% un mot de passe, mais des conseils simples suffisent pour bien prendre en compte cet aspect : Longueur du mot de passe - Choisir un mot de passe d'une longueur minimum de 8 caractères : idéalement, il doit être composé d'au moins 14 caractères. Quatre pièges à éviter Tester la sécurité de son mot de passe Gestion des mots de passe : les logiciels gratuits
Faille Heartbleed : les sites pour lesquels il est conseillé de changer son mot de passe Le Monde.fr | • Mis à jour le | Par Michaël Szadkowski Deux jours après la révélation d'une faille de sécurité au sein du protocole OpenSSL, baptisée « Heartbleed », cette dernière est décrite par certains comme « le pire cauchemar » qui puisse arriver concernant la sécurité des échanges sur Internet. Le logiciel libre OpenSSL est installé sur les serveurs de très nombreux sites pour établir des connexions chiffrées et sécurisées entre ce dernier et ses utilisateurs. Le bug Heartbleed (dont l'origine se trouve être une erreur de programmation d'un développeur allemand) permet, en théorie, à des pirates informatiques de pouvoir récupérer un grand nombre d'informations sur les utilisateurs des sites utilisant ce protocole de sécurité (leurs identifiants et mots de passe, leurs codes de cartes bancaires, etc.). Lire : Que sait-on de « Heartbleed », l'inquiétante faille de sécurité sur Internet ? Facebook.
The Malware Museum. Vírus animációk software eye favorite 2 comment 1 An example of an MS-DOS-based virus, now removed of its destructive capability but leaving its messages. favoritefavoritefavoritefavoritefavorite ( 1 reviews ) favorite 7 comment 2 An example of an MS-DOS-based virus, now removed of its destructive capability but leaving its messages. favoritefavoritefavoritefavoritefavorite ( 2 reviews ) favorite 3 favorite 5 comment 3 An example of an MS-DOS-based virus, now removed of its destructive capability but leaving its messages. favoritefavoritefavoritefavorite ( 3 reviews ) favorite 0 comment 4 An example of an MS-DOS-based virus, now removed of its destructive capability but leaving its messages. favoritefavoritefavoritefavoritefavorite ( 4 reviews ) favorite 4 An example of an MS-DOS-based virus, now removed of its destructive capability but leaving its messages. favoritefavoritefavoritefavorite ( 4 reviews ) comment 5 by Mikko Hypponen movies favorite 12 comment 0 Presented at DEF CON 19 in Las Vegas, Nevada in 2011.
Kasulikud veebivahendid ja veebipõhised õppematerjalid! How To Do A Southern American Accent (Accents) How To Do A Southern American Accent: This will provide you with basic tips of how to speak in a South American accent. No-one will recognize your voice anymore! Hello, I'm an actor and a voice coach here are some tips for working on your voice. Now the key to any accent is to isolate the sounds that are specific to that accent. So for a Southern American accent we're going to start with the R sound. Now there are lots of variations on what is commonly called a Southern accent, there's quite an old fashioned one that doesn't have a letter R sound after vowels and there's a more modern one that does but we're going to work for the really old fashioned one that you'd hear in Tennessee Williams plays and that you might hear in something like 'Gone With The Wind'. So for this unless an R is written before a vowel it isn't pronounced, listen to this. Listen also to the sound that we get in words like bed and head and then words like bared and lair.
Astuces Le classement des mots de passe les plus pourris Temps de lecture: 2 min — Repéré sur Vice US Le gestionnaire de mots de passe spécialisé NordPass vient de publier la liste des codes utilisés par les internautes pour protéger leur ordinateur et comptes en tous genres. Le constat est simple: nos mots de passe sont toujours aussi ridicules et faciles à deviner. Les internautes ont une fâcheuse tendance à utiliser les mêmes codes de protection que les autres. On retrouve ainsi en tête de liste des suites de chiffres. Parmi les indémodables qui stagnent dans le top 25, l'on trouve qwerty, juste devant I love You et 654321. Davantage de mots de passe Autre phénomène intéressant à noter: on aurait aujourd'hui davantage de mots de passe à gérer qu'auparavant. La raison? Pour celles et ceux qui prennent la sage décision de renforcer la sécurité de leurs codes, afin de se garder de tout piratage, voici quelques conseils.
How Secure Is My Password? Entries are 100% secure and not stored in any way or shared with anyone. Period. Passwords are the bloodline of data and online security, but our research on the password habits in the U.S. shows that less than half of Americans feel confident that their password is secure. Is your password secure? We built this password checker tool to help you find that out yourself, so try it out now! Pro Tip: We recently rolled out a new password generator tool that will help you create super secure passwords in a snap! What Makes a Good Password? Why Is Password Security Important? Not having secure passwords has its consequences, which include but are not limited to: After gaining access to a user’s credentials, many hackers will log into their accounts to steal more of their personally identifiable information (PII) like their names, addresses, and bank account information. The Impact of Stolen Passwords Impact on Businesses Impact on Consumers Other Ways To Protect Yourself Online
Piltide ja videote jagamine | Päriselt ka või? Selleks, et endale ja teistele mitte suuri jamasid kaela tõmmata, mõtle enne oma piltide või videote üles laadimist järgnevale: 1. Mis on avalik, pole enam sinu. Kui sa paned endast internetti üles pildi või video, jääb see sinna igaveseks. 2. Pööra tähelepanu kõikidele kuuldavatele ja nähtavatele asjadele (isegi ka neile, mis on ainult taustal). 3. Kas sa tahad tulevikus tööd leida? 4. Kui laed üles videoid või pilte, millel on ka teisi inimesi, küsi neilt, kas nad on sellega nõus. 5. Jaga oma pilte ja videoid keskkondades, kus saad ise kontrollida, kes neid näeb (jagades neid näiteks ainult teatud grupi või sõpradega). Enne, kui sa isiklikke pilte või videoid üles laed, mõtle: 1. JahEi 2. 3. Kui vastasid kasvõi ühele küsimusele „Jah“, mõtle tõsiselt üle, kas see fail vajab tõesti üles laadimist.
Grimoires Warning : the following documents deal with magic and should not be used without proper care and deep knowledge of this art. The word grimoire is from the Old French grammaire, or grammar. Latin "grammars" (books on Latin syntax and diction) were considered in the Middle Ages as books of basic instruction. Today, a grimoire is considered as a book of magical knowledge, with instructions for its use to achieve certain ends. They contain various magical formulas or symbols such as astrological correspondences, incantations and ritual instructions for working with angels and conjuring spirits and demons as well as directions on casting charms and spells, on mixing medicines, and making talismans. To understand the real content, one must delve into the life and times of the magicians who wrote them and decipher the symbols that were used to hide the real secrets. More about the Necronomicon