

China Continues its Focus on Cyber: Report. WASHINGTON and TAIPEI — China continues to invest in the development of offensive cyberwarfare capabilities that could disrupt global computer networks, according to a new U.S.
Defense Department report. “China is investing in not only capabilities to better defend their networks, but also, they’re looking at ways to use cyber for offensive operations,” said David Helvey, acting deputy assistant defense secretary for East Asia, during a May 18 briefing at the Pentagon. Evidence suggests China already hacking into U.S. drone fleet networks. China's Cyber Militia. There's been an interesting new development in China's use of cyber space as an element in its intelligence and security operations.
The People's Liberation Army (PLA) is reportedly funding a vast complex of part-time cyber-devotees to supplement and compliment the official structure of cyber interception and invasion. Equally as interesting is the willingness of the Chinese authorities to allow the publication of this fact. China calls for joint efforts for peaceful, secure, equitable cyber space. UNITED NATIONS, Oct. 20 (Xinhua) -- China on Thursday called upon the international community to "work together towards a peaceful, secure and equitable information and cyber space," stating that cyber security "represents a major non-traditional security challenge" confronting the world at large.
Wang Qun, the Chinese ambassador for disarmament affairs, made the statement when he was addressing the First Committee of the UN General Assembly on information and cyberspace security. The First Committee is in charge of disarmament and international security. "At present, the information and cyberspace security represents a major non-traditional security challenge confronting the international community," Wang said. Collusion Collision. China’s Brazen Cyber Theft? A senior US lawmaker claims that China is engaging in unprecedented espionage around the world.
Is it? Blog Archive » Collision in Cyberspace Is Unavoidable: The View from Chinese Analysts. A Chinese news vendor waits for customers in front of newspapers.
(Claro Cortes/Courtesy Reuters) People’s Tribune Magazine (人民论坛杂志) has a collection of twelve articles on cyberspace and cyber conflict by Chinese analysts at think tanks and academic institutes. Reading the essays, it is clear that Chinese analysts believe the United States is ahead in the competition. U.S. strengths include “core technology, experts, high military expenditures, and an integrated command system.” WikiLeaks cables reveal fears over Chinese cyber warfare. China is building up an increasingly sophisticated cyber warfare capability by hiring companies that employ hackers, the US fears.
Photograph: AP The US fears China is plotting internet warfare via private companies that are known to have recruited top hackers. Why is the West silent on 5-year cyberwar launched by China? August 04, 2011, 12:16 PM — There were no big surprises in the reaction of the countries or organizations named as targets of a series of persistent, aggressive, often successful online attacks during the past five years – a campaign described in detail by a report from security vendor McAfee, which became public yesterday.
Most of the victims – 49 U.S. -based corporations and a series of U.S. government agencies as well as companies and government sites in 13 other countries – were well aware of the attack, and more aware of their source than the unnamed "state actor" McAfee admitted to in the report. “All the signs point to China,” Vanity Fair quotes James A. Lewis, director and senior fellow of the Technology and Public Policy Program at the Center for Strategic and International Studies as saying. A U.S. China is the Voldemort of hacking: it that must not be named! The most striking thing about news of the latest high-level hacking campaign isn’t just that it has been going on for at least five years.
It isn’t even that among the victims of the hack attack were some of the biggest world organisations (including the United Nations), some national governments (including India), and some of the biggest companies (defence contractors and high-tech enterprises). The most striking thing about it is that, from all accounts, the hack attack was carried out by Lord Voldemort, the evil antagonist of the fictional boy wizard Harry Potter. The Chinese Way Of Hacking. Cyberwarfare in 2011 is an odd beast. Many Western governments reportedly actively monitor rivals and engage in online sabotage, while countries ranging from Israel to Iran to India also engage in cyberwarfare programs of their own.
But it's attacks against the American government and commercial websites such as Google that grab headlines. As foreign governments learn the ease of obtaining intelligence online and foreign corporations continue to get the edge on their competitors through massive online attacks, future hacker efforts will only become more ambitious. One of the countries where many of these civilian and military attacks reportedly originate is China. China Caught With Evidence of Cyberwarfare Against U.S. It was supposed to be just another piece of Chinese propaganda.
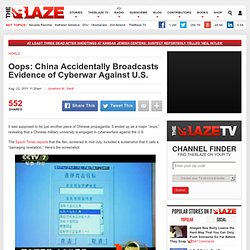
It ended up as a major “oops,” revealing that a Chinese military university is engaged in cyberwarfare against the U.S. The Epoch Times reports that the film, screened in mid-July, included a screenshot that it calls a “damaging revelation.” Biggest-ever series of cyber attacks uncovered, U.N. hit. Oil Firms Hit by Hackers From China, Report Says. A Brief History Of Chinese Cyberspying - The Firewall - the world of security. China telecom briefly hijacked U.S. Web traffic: panel. China's Internet 'Hijacking' Creates Worries for Security Experts China's 18-Minute Mystery. China denies hijacking a huge chunk of US net traffic.
18 November 2010Last updated at 10:14 For 18 minutes in April about 15% of all net traffic was re-routed via China China has rejected claims that it hijacked a huge chunk of net traffic in April 2010.
The allegation surfaced in a report presented to the US Congress which said that for 18 minutes the traffic was redirected to Chinese servers. China Hijacks 15% Of Internet Traffic? More Like .015% - Andy Greenberg - The Firewall. China Hijacked 15% of US Internet Traffic-and no one noticed - TNW Apps. The Internet, though ironically created for communications during a nuclear war, is based on trust.
The trust that all nodes on the Internet are equal and when connecting from one website to another the connections will take the shortest or fastest route. But what if someone said that they were the best route, best no matter what? China Hijacks 15% of Internet Traffic? On Wednesday, the US China Economic and Security Review Commission released a wide-ranging report on China trade, capital markets, human rights, WTO compliance, and other topics.
If you have time to spare, here is a link to the 324 page report. Tucked away in the hundreds of pages of China analysis is a section on the Chinese Internet, including the well-documented April 8, 2010 BGP hijack of several thousand routes (starting on page 244). To review, shortly around 4am GMT on April 8th a Chinese Internet provider announced 40,000 routes belonging to other ISPs / enterprises around the world (though many were for China based companies). The Chinese Way of Hacking. Cyberwarfare in 2011 is an odd beast. Many Western governments reportedly actively monitor rivals and engage in online sabotage, while countries ranging from Israel to Iran to India also engage in cyberwarfare programs of their own. But it's attacks against the American government and commercial websites such as Google that grab headlines. As foreign governments learn the ease of obtaining intelligence online and foreign corporations continue to get the edge on their competitors through massive online attacks, future hacker efforts will only become more ambitious.
For China activists, hacking attacks a fact of life. Even working on her laptop in Amnesty International's London headquarters or talking on her mobile phone going around the city, Corinna-Barbara Francis suspects Chinese authorities are listening in. At a time when authorities in Beijing are carrying out the most serious crackdown on dissent since Tiananmen Square, the human rights group's China researcher says she simply assumes all her electronic data is already compromised. Whether or not she is right is almost impossible to know. Beijing angrily denies any suggestions of official complicity in a string of recent high-profile computer hacks including Internet giant Google GOOG.O., which said it traced an attempt illicitly to access accounts of activists and others to China.
NAQ: Is China stepping towards cyberwar. China's cyberwar goes beyond Google. Meet China’s Newest Soldiers: An Online Blue Army. China's Blue Army of 30 computer experts could deploy cyber warfare on foreign powers. China's People's Liberation Army honour guards physically defend the nation, while the Blue Army division is protecting the systems from cyberattack. Source: AFP. Chinese hackers infiltrated five energy firms: McAfee. Night Dragon hackers smash energy multinationals. Hackers have used a range of techniques in a dedicated attack against global energy companies, a report has indicated. An unnamed selection of oil, energy and petrochemical firms have been targeted by cyber criminals in attacks that may have started as long ago as 2007, McAfee said.
Under the so-called Night Dragon operation, the attacks appeared to have been coordinated from a central point, the recently-acquired security firm claimed. The hackers probed the companies for inside information, such as oil and gas production data, potential areas where the multinationals were looking to work and schematics on how systems worked. What a cyberwar with China might look like. Computerworld - It's August 2020. A powerful and rising China wants to bring the city-state of Singapore into its fold as it has with Hong Kong, Macau and Taipei. Its first physical attacks against Singaporean assets are still weeks away. But already, China has launched a massive cyber campaign, designed largely to degrade and disrupt the communications capabilities of the U.S., Japan and other allied nations.
"Le Pentagone sous-estime le problème des cyberattaques chinoises" - Journal du Net Solutions. Stuxnet n'est pas du tout une révolution, la sécurité est moins une question d'argent que de confiance...Le gourou de la sécurité tord le cou à quelques idées reçues. JDN Solutions. Qu'avez-vous fait pour le Congrès américain exactement ? A quoi ont pu servir vos avis ? Bruce Schneier. J'ai en effet témoigné devant le Congrès sur de nombreux sujets liés à la sécurité informatique. De ce que j'ai pu constater, de près, ils n'ont cependant absolument jamais rien fait malgré mes recommandations. Www.au.af.mil/au/ssq/2011/spring/bronk.pdf. Chinese "Night Dragon" hackers target Western energy firms. China Has Ability to Hijack U.S. Military Data, Report Says. China in the past year demonstrated it can direct Internet traffic, giving the nation the capability to exploit “hijacked” data from the U.S. military and other sources, according to a new report.
Recent actions raise questions that “China might seek intentionally to leverage these abilities to assert some level of control over the Internet,” according to excerpts from the final draft of an annual report by the U.S. -China Economic and Security Review Commission. “Any attempt to do this would likely be counter to the interests of the United States and other countries.” A new approach to China. After Google’s Stand on China, U.S. Treads Lightly. Microsoft admits Explorer used in Google China hack. Google Hack Attack Was Ultra Sophisticated, New Details Show. International : Les Chinois en pointedans la «cyberguerre»