

China Adds New Barrier to Gmail. Photo BEIJING — The Chinese government appears to have blocked the ability of people in China to gain access to Google’s email service through third-party email services like Apple Mail or Microsoft Outlook, which many Chinese and foreigners had been relying on to use their Gmail accounts after an earlier blocking effort by officials, according to Internet analysts and users in China.
The blocking began on Friday and has ignited anger and frustration among many Internet users in China. Data from Google shows traffic to Gmail dropping to zero from Chinese servers. But it is not just a matter of convenience for Chinese Internet users. Some foreign companies use Gmail as their corporate email service, for example, and so companies will have to ensure that employees have V.P.N., or virtual private network, software to get into Gmail. Countering Cyberattacks Without a Playbook. Photo WASHINGTON — For years now, the Obama administration has warned of the risks of a “cyber-Pearl Harbor,” a nightmare attack that takes out America’s power grids and cellphone networks and looks like the opening battle in a full-scale digital war.
Such predictions go back at least 20 years, and perhaps that day will come. But over the past week, a far more immediate scenario has come into focus, first on the back lots of Sony Pictures and then in back-to-back strategy sessions in the White House Situation Room: a shadow war of nearly constant, low-level digital conflict, somewhere in the netherworld between what President Obama called “cybervandalism” and what others might call digital terrorism. In that murky world, the attacks are carefully calibrated to be well short of war.
What does a cyber counterattack look like? - Joseph Marks - POLITICO. President Barack Obama promised at his year-end news conference Friday that the U.S. will respond “proportionally” to North Korea’s cyberattack against Sony Pictures Entertainment, but the conventional options available to him are ineffective, merely symbolic or a bad risk because they might lead to a larger military conflict.
Military action against North Korea is effectively off the table, experts told POLITICO, and trade with the isolated rogue nation is nearly nonexistent, making sanctions ineffective. The U.S. could indict those behind the hack, but that would have little real-world effect. A senior Democrat called for the country to be relisted as a state sponsor of terrorism — but North Korea already spent years on the list before the Bush administration removed it during the past decade. Story Continued Below (Also on POLITICO: U.S. says North Korea behind Sony hack) Xi Jinping Leads China’s New Internet Security Group.
The new central Internet security and informatization leading group is tasked with defining China’s cyber strategy.
China’s new central Internet security and informatization leading group met for the first time on Thursday, with President Xi Jinping himself heading up the meeting. Premier Li Keqiang is also a member of the group. The leading group will focus on cyber issues in all its aspects, including economic , political, cultural, and even military issues. According to Xinhua, Xi Jinping told the group that “Internet security and informatization is a major strategic issue concerning a country’s security and development as well as people’s life and work.”
Who Should Govern the Internet? A certain group of countries want greater control over how the internet is run globally.
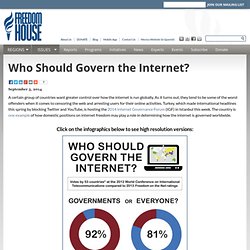
As it turns out, they tend to be some of the worst offenders when it comes to censoring the web and arresting users for their online activities. Turkey, which made international headlines this spring by blocking Twitter and YouTube, is hosting the 2014 Internet Governance Forum (IGF) in Istanbul this week. iPhone Issues Risk Making Apple Like Microsoft: Yiannopoulos: Video. The Social Laboratory. In October 2002, Peter Ho, the permanent secretary of defense for the tiny island city-state of Singapore, paid a visit to the offices of the Defense Advanced Research Projects Agency (DARPA), the U.S.
Defense Department's R&D outfit best known for developing the M16 rifle, stealth aircraft technology, and the Internet. Ho didn't want to talk about military hardware. Rather, he had made the daylong plane trip to meet with retired Navy Rear Adm. John Poindexter, one of DARPA's then-senior program directors and a former national security advisor to President Ronald Reagan. It’s Not Beijing’s Hackers You Should Be Worried About, It’s Moscow’s. When U.S. officials warn of the threat foreign cyber spies pose to American companies and government agencies, they usually focus on China, which has long been home to the world's most relentless and aggressive hackers.
But new information shows that Russian and Eastern European hackers, who have historically focused their energies on crime and fraud, now account for a large and growing percentage of all cyber espionage, most of which is directed at the United States. Individuals and groups in eastern Europe, and particularly in Russia and Russian-speaking countries, are responsible for a fifth of all cyber spying incidents in the world, according to a global study of data breaches conducted by Verizon, published on Tuesday.
The spies are targeting a range of companies as varied as the global economy itself, and are stealing manufacturing designs, proprietary technology, and confidential business plans. China Restricts Messaging Apps, Confirms Blocking Line, KakaoTalk Last Month. Chinese authorities on Thursday issued new rules for messaging applications, adding that a move to ban popular foreign-messaging services like KakaoTalk and LINE in July was in the interest of national security and to block the unsavory aspects of cyberspace.

The new rules require public-account users to sign up with their real names, and only news organizations and authorized users will be allowed to post political views on public accounts, the Wall Street Journal reported Thursday. Rise of The Asian Cyber Armies - USNI News. States are increasingly standing up military and intelligence organizations for computer network operations.
While countries everywhere perceive a need to attack and defend in cyberspace, cyber forces are of particular interest to security in Asia because they coincide with a regional investment in naval, air, and command, control and communications systems. And although American society may be vulnerable to disruption, highly technical and increasingly informatized Asian societies also face complex security challenges. For years, most understood Asian cyber issues through the prism of China. China Restricts Messaging Apps, Confirms Blocking Line, KakaoTalk Last Month. NATO’s September Summit Must Confront Cyber Threats. Jarno Limnéll is the Director of Cyber Security at McAfee (now part of Intel), a PhD in military science, and a former officer in the famously tough Finnish armed forces, where he spent five years as a strategic analyst.
He spoke to us in June about the Russian threat in cyberspace, which many analysts consider far more dangerous than the Chinese (whom we know more about because they keep getting caught….). In this article, he lays out the cyber challenge facing the impending NATO summit in Wales. The views expressed here are his own. – the editors. Cyber is already an integral part of all conflicts and wars in today’s world. But there is plenty of work and planning ahead before NATO, as an alliance, is a credible player in the cyber domain. Lexington Institute » Private Companies Will Be The Core Of A New “Offset” Strategy Against Cyber Attacks. Cyber warfare is not a future threat. It is a real, here and now danger to the security of the West.
Some nations such as Russia have already employed cyber attacks as part of their integrated offensive operations. Others, China for example, are withholding their fire, preferring to employ their cyber troops for a combination of military, economic and intelligence preparation of the battlefield. We are still in the early stages of what could be a new revolution in military affairs, perhaps like the period just before the start of the First World War, when the military applications of the internal combustion engine to combat on land and in the air was mostly speculative.
But make no mistake, as Jarno Limnell, Director of Cyber Security for McAfee pointed out in a recent article for Breaking Defense, we are in a new era: Internet Fragmentation. Nominet Trust has supported Apps for Good since it launched in 2010. Back then, the programme supported less than 50 students. In this academic year, more than 17,000 young people have signed up for the Apps for Good course. Each year the nationwide Apps for Good Awards competition attracts the top student app teams from across the UK to compete to have their apps launched commercially. ICANN delegates are invited to meet the eight 2014 Apps for Good winners while they develop their winning ideas with leading industry app developers. Cyberspace fragmentation: an internet governance debate beyond infrastructure. Since the Peace of Westphalia in 1648 our international system is based upon the principle of territorial sovereignty. Today, however, cross-border online spaces made possible by the internet span across a system of fragmented national jurisdictions.
Tension rises since we do not have the legal equivalent to the technical interoperability that enables the global internet. A choice has to be made. What will happen if countries carve up the internet? Fragmenting the web: what could emerge is a patchwork of online nation states with different rules and regulations and hindered communications. Photograph: Petros Karadjias/AP Twenty years ago, there was nothing like the internet we have today, the global all-connecting network that has become an integral part of our lives. Over the last few decades, we have all witnessed how it has grown exponentially and come to change our everyday existence – keeping most of us online all the time (with accompanying frustrations as well as benefits) and making communications and information exchange unprecedentedly seamless and fast.
What is a Cyber Weapon? What is a Cyber Weapon? At first glance this seems an immediate question to answer, but should anyone try to analyze the meaning of this term more deeply, probably he would be quite surprised and disappointed in discovering that the answer is not so immediate since an exact definition has not been given (at least so far). A real paradox in the same days in which The Pentagon, following the Japanese Example, has unveiled its new strategy aimed to dramatically accelerate the development of new Cyber Weapons. And do not think these are isolated, fashion-driven examples (other nations are approaching the same strategy), but rather consider them real needs in the post-Stuxnet age, an age in which more and more government are moving their armies to the fifth domain of war [you will probably remember the (in)famous episode, when F-Secure was able to discover Chinese Government launching online attacks against unidentified U.S.
Targets]. Going Dark: The Internet Behind The Internet : All Tech Considered. Tor is the main browser people use to access Darknet sites, allowing users to remain completely anonymous. Cloaked Internet: What Is the 'Invisible Web'? August, 2013. NATO’s September Summit Must Confront Cyber Threats. Lexington Institute » Private Companies Will Be The Core Of A New “Offset” Strategy Against Cyber Attacks. It’s Not Beijing’s Hackers You Should Be Worried About, It’s Moscow’s. The Social Laboratory. Wp-content/uploads/2013/04/The-Dark-Future-of-International-Cybersecurity-Regulation.pdf. Wp-content/uploads/2013/04/The-Dark-Future-of-International-Cybersecurity-Regulation.pdf.
It’s Not Beijing’s Hackers You Should Be Worried About, It’s Moscow’s. The Social Laboratory. Cyber confidence building in the Asia-Pacific: three big take-aways from the ARF. The battle for cybermetrics. The battle for cybermetrics. Collaborating for a stronger region – cybersecurity capacity building within the ARF. Polarised cyber perspectives in the Asia-Pacific: what’s the ARF to do? China’s digital transformation. As individual companies adopt web technologies, they gain the ability to streamline everything from product development and supply-chain management to sales, marketing, and customer interactions.
For China’s small enterprises, greater digitization provides an opportunity to boost their labor productivity, collaborate in new ways, and expand their reach via e-commerce. In fact, new applications of the Internet could account for up to 22 percent of China’s labor-productivity growth by 2025. Yet the Internet is not merely a tool for automation and efficiency; it also expands markets rapidly. Events|U.S.-Japan Research Institute (US NPO) Internet Governance: Asia-Pacific perspectives — UN-APCICT. State Department Official Accuses Russia And China Of Seeking Greater Internet Control. A top State Department official on Tuesday accused China and Russia of abandoning international talks on cybersecurity and seeking United Nations approval to assert greater control over the Internet in their countries.
Michele Markoff, the state department’s senior policy adviser on cyber affairs, said 15 countries -- including the United States, Russia and China -- agreed last year to further discuss how countries address the growing use of information technology. But earlier this month, China and Russia -- along with Tajikistan and Uzbekistan -- issued their own proposal to the U.N. Secretary General that included language aimed at restricting Internet freedom, which the United States opposes, Markoff said. The proposal, called the International Code of Conduct for Information Security, asks countries to help prevent technology that “undermines other nations’ political, economic and social stability.” A Scene from the Road to Cyber Governance: The Budapest Cyberspace Conference – by Roger Hurwitz. Special Report - Compelled to control: conflicting visions of the future of cyberspace - Australian Strategic Policy Institute. Governing the Net: the long and winding road.
China, Russia Resume Push for Content Restrictions in Cyberspace. Www.unidir.ch/files/conferences/pdfs/a-cyber-code-of-conduct-the-best-vehicle-for-progress-en-1-963.pdf. China and Russia Submit Cyber Proposal. Files/attachments/130723_jimlewis_testimony_v2.pdf. Chinese Predictions for Cyberspace in 2014: Intense Competition and National Conflict. China’s New Small Leading Group on Cybersecurity and Internet Management. How China Becomes a Cyber Power. China Hacking Is Deep and Diverse, Experts Say - WSJ. Exclusive: Inside the FBI's Fight Against Chinese Cyber-Espionage. China says Internet security necessary to counter 'hostile forces' China denounces US cyber-theft charges. At the Nexus of Cybersecurity and Public Policy: Some Basic Concepts and Issues. Rise of The Asian Cyber Armies.
Hackers expose weak cyber defenses across Asia. China’s President Will Lead a New Effort on Cybersecurity.