

Towards%20Data%20Sovereignity%20in%20Cyberspace Nugraha. Moving Forward with the Obama-Xi Cybersecurity Agreement. China’s leaders often talk about the need for a “new model of great power relations.”
The agreement on cybersecurity between President Xi and Obama is a first step in defining it. The agreement does not mean we are done with cybersecurity. It is the start of a long journey to define both cyberspace and the larger relationship. Serious discussions on how to respond to China’s cyber espionage began several years ago.
A strategy that combined pressure and accommodation seemed the best alternative to passivity, and U.S. concerns were raised many times, including in a December 2013 non-paper given to Chinese officials that discussed sanctions, indictments and other measures if matters did not improve. Threatening to impose sanctions, using the new cyber sanctions created after the Sony incident, played a key part in moving China and orchestrated leaks built pressure with a skill not always seen in the White House. The world needs new norms on cyberwarfare. By Joseph S.
Nye Jr. October 1 Joseph S. Nye Jr. is a professor at the Harvard Kennedy School and a member of the Global Commission on Internet Governance. When President Obama and Chinese President Xi Jinping discussed cyberweaponry rules of the road at their recent White House news conference, it represented a landmark for a new field. Whenever countries confront a disruptive new technology that they cannot control, they eventually seek arms-control agreements. Is cyber arms control the answer? But that doesn’t mean it’s impossible to reach agreements on rules limiting behavior. Critics scoff at vows such as “no first use” of cyberweapons against certain civilian targets.
A norm of self-restraint could also help with dangerous “zero-days,” or undiscovered coding vulnerabilities that take their name from the amount of time that programmers have to act to stop a malicious outsider from exploiting the opening. Such steps are not panaceas that would produce cybersecurity. CBMs. Maurer cyber norm dp 2011 11 final. An Updated Draft of the Code of Conduct Distributed in the United Nations – What’s New? Resources -> INCYDER database On 9th January 2015, six members of the Shanghai Cooperation Organization (SCO) (China, Kazakhstan, Kyrgyzstan, Russia, Tajikistan, and Uzbekistan) proposed an updated version of the International Code of Conduct for Information Security to the United Nations.

The document was submitted to the UN’s Secretary-General Ban Ki-moon with a request that it be circulated as a formal document during the 69th session of the UN General Assembly. The previous draft of the Code of Conduct was submitted to the UN by China, Russia, Tajikistan and Uzbekistan in September 2011. Although the letter accompanying the draft states that the revised text takes account of the comments and suggestions received after the initial document was released, the new draft only includes minor modifications and additions, and the general ideas and nature of the document have remained the same.
Iran, Terrorists, North Korea Scariest Cybersecurity Threats? By Tim Starks Posted at 10:16 a.m. on Oct. 1, 2014 Carlin speaks as Attorney General Eric Holder, right, and U.S.
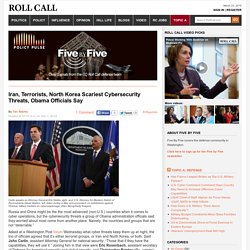
Attorney for Western District of Pennsylvania David Hickton, left, listen during a May announcement on indictments against Chinese military hackers on cyber-espionage. (Alex Wong/Getty Images) Russia and China might be the the most advanced (non-U.S.) countries when it comes to cyber operations, but the cybersecurity threats a group of Obama administration officials said they worried about most come from another place. Namely: the countries and groups that are not “deterrable.” Asked at a Washington Post forum Wednesday what cyber threats keep them up at night, the trio of officials agreed that it’s either terrorist groups, or Iran and North Korea, or both. Most experts say that Russia and China have used their capability against the United States primarily for theft. Rosenbach said some 60 countries were looking to develop the equivalent of the U.S. China Reveals Its Cyberwar Secrets. The second season finale finally showed the gay-themed show could produce compelling drama.

But will HBO give it a third season? [Warning: Spoilers] If you were watching Looking and shouting from your sofa Sunday night, “Leave. Go now,” then you will have finally, like this viewer, been siding with Patrick, the show’s drippy, blandly irritating lead character, played by Jonathan Groff—and hoping he would follow his instinct and get out of his fast-unraveling relationship with Kevin (Russell Tovey). But did he? The ratings have stayed low, however, and so Looking’s future is in question.
Fatally, it’s a gay-themed show that its fans are certainly passionate about, but a critical mass of viewers—gay, straight, whatever—don’t seem to care if it lives or dies. It was refreshing because, in this era of marriage equality, smiles, and wedding bands, the complex fault lines of fidelity and commitment are often glossed over—but not on Sunday night’s episode of Looking.