

National Security Agency (NSA) Collection Archives - The Black Vault. How NSA Tracks You (Bill Binney) [improved audio] So, the NSA Has an Actual Skynet Program. Sentient World Simulation: Meet Your DoD Clone. The NSA - The Super Secret National Security Agency. NSA Atrocities – Part III – Brain Rape and General Michael Aquino. "Skynet" is real, and it could flag you as a terrorist. It may not be quite the self-aware computer network that takes over millions of computers and machines, but "Skynet" is real.
Documents published by The Intercept, leaked by NSA whistleblower Edward Snowden, confirm that the Skynet program exists -- at least in name only. Its name comes from the intelligent computer defense system in the "Terminator" films, which later destroys most of humanity in a nuclear apocalypse. The National Security Agency program analyzes location and metadata from phone records to detect potentially suspicious patterns, according to the publication. In one example, it was used to identify people that act as couriers between al-Qaeda leadership. (This may have been the program that helped identify Osama bin Laden's courier, leading to his targeted killing in Pakistan by US forces in 2011.)
More than 55 million cell records collected from major Pakistani telecom companies were fed into the Skynet system to determine targets of interest, the document said. The NSA Actually Named a Program Skynet. Life in the Electronic Concentration Camp: The Surveillance State Is Alive and Well. By John Whitehead “Big Brother in the form of an increasingly powerful government and in an increasingly powerful private sector will pile the records high with reasons why privacy should give way to national security, to law and order […] and the like.” ― William O.
Douglas, Supreme Court Justice Bottle up the champagne, pack away the noisemakers, and toss out the party hats. There is no cause for celebration. We have secured no major victories against tyranny. We have achieved no great feat in pushing back against government overreach. For all intents and purposes, the National Security Agency has supposedly ceased its bulk collection of metadata from Americans’ phone calls, but read the fine print: nothing is going to change. Is The NSA Really Ending Its Mass Surveillance Program?
By Joshua Krause.
Police Using Biometrics on Americans Without Consent in Unaccountable Database. By Aaron Dykes Facial recognition and biometric databases have been a reality in technology for decades, and have been used overseas by the military to assist in occupying potentially hostile populations in places like Iraq and Afghanistan.
Populations there not only face the possibility of becoming a statistical civilian casualty, but are processed and tagged like cattle as well. Now, that paradigm is coming home to roost – as spy agencies like the NSA have long planned. Biometrics are designed for use in mass populations here in America and throughout the Western world, not just war-torn locales. Domestic Surveillance Techniques - Our Data Collection Program. Surveillance Techniques: How Your Data Becomes Our Data In 2001, NSA published the secret "Transition 2001" report defining our strategy for the 21st century.
No longer could we simply access analog communications using conventional means, the new digital world of globally-networked encrypted communications required a dramatic change to our surveillance strategy: NSA would need to "live on the network". We've turned our nation's Internet and telecommunications companies into collection partners by installing filters in their facilities, serving them with secret court orders, building back doors into their software and acquiring keys to break their encryption. As easy as ABC: NSA’s plans for digital warfare. NSA Cyber War Will Use Internet of Things as Weapons Platform; Your Home is the Battlefield. Old-Thinker News | January 19, 2015 By Daniel Taylor “World War III is a guerrilla information war with no division between military and civilian participation.” – Marshall McLuhan, Culture is Our Business, 1970 New Snowden documents recently revealed that the NSA is getting ready for future digital wars as the agency postures itself in an aggressive manner towards the world.
How the NSA's Domestic Spying Program Works. Snowden leak: NSA plans to infect ‘millions’ of computers. (Thanks to Cheryl for a head’s up on potential virus bombardment!
-A.M.)Published time: March 12, 2014 17:22 Edited time: March 13, 2014 08:34. Secret Space War XVII: Who Runs the New NSA Facility At Bluffdale. Smart Lights: New LEDS Allow NSA To Spy On Your Every Movement. Galactic Connection UFO | Ascension | Conspiracy | Spirituality Smart Lights: New LEDS Allow NSA To Spy On Your Every Movement Fri, July 4, 2014.
NSA pays tech companies millions to engineer backdoors into encryption protocols. (NaturalNews) There is a saying that says, when it comes to government, they've got you coming and going.
No truer words are spoken when the subject comes to serial invasions of your privacy. Not only is the National Security Agency monitoring your every electronic communication, but the agency is paying your tech company and Internet service provider to hack you as well. The NSA's Secret Role in the U.S. Assassination Program. Credit: Kirsty Wigglesworth/Associated Press.
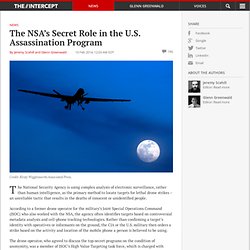
The National Security Agency is using complex analysis of electronic surveillance, rather than human intelligence, as the primary method to locate targets for lethal drone strikes – an unreliable tactic that results in the deaths of innocent or unidentified people. According to a former drone operator for the military’s Joint Special Operations Command (JSOC) who also worked with the NSA, the agency often identifies targets based on controversial metadata analysis and cell-phone tracking technologies. Rather than confirming a target’s identity with operatives or informants on the ground, the CIA or the U.S. military then orders a strike based on the activity and location of the mobile phone a person is believed to be using. His account is bolstered by top-secret NSA documents previously provided by whistleblower Edward Snowden. It is also supported by a former drone sensor operator with the U.S.