

NSA Tests Out Smartphones that Recognize Handwriting Motion. The NSA Has Inserted Its Code Into Android OS, Or Three Quarters Of All Smartphones. Over a decade ago, it was discovered that the NSA embedded backdoor access into Windows 95, and likely into virtually all other subsequent internet connected, desktop-based operating systems.

NSA taps into Google, Yahoo clouds, can collect data 'at will,' says Post. The NSA has secretly tapped into the private fiber-optic networks that connect Google's and Yahoo's worldwide data centers, allowing the spy agency to suck up "at will" metadata and content belonging to users of the companies' services, according to The Washington Post.
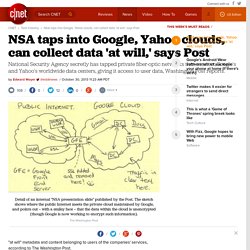
Under a program called MUSCULAR -- a joint project with British NSA counterpart the GCHQ -- the NSA takes advantage of overseas taps to intercept data flowing within Google's and Yahoo's geographically distributed data "clouds," where multiple copies of user data are stored unencrypted, the Post reports. The article cites documents leaked by former NSA contractor Edward Snowden, as well as unnamed "knowledgeable officials.
" Such data might include, for example, information in Gmail accounts or in Google Drive files. In a statement to the Post, Google said it was "troubled by allegations of the government intercepting traffic between our data centers, and we are not aware of this activity. Update, 11:35 a.m. Inner workings of a top-secret spy program. PRISM providers NSA collects, identifies, sorts and stores at least 11 different types of electronic communications Chats E-mail.
NSA develops cyber weapons, ‘attacker mindset’ for domination in digital war – Snowden leaks. Published time: January 17, 2015 23:37.
Timeline of NSA Domestic Spying. The Intercept. The NSA and Me. The tone of the answering machine message was routine, like a reminder for a dental appointment.
But there was also an undercurrent of urgency. “Please call me back,” the voice said. “It’s important.” What worried me was who was calling: a senior attorney with the Justice Department’s secretive Office of Intelligence Policy and Review. ICREACH: How the NSA Built Its Own Secret Google -The Intercept. The National Security Agency is secretly providing data to nearly two dozen U.S. government agencies with a “Google-like” search engine built to share more than 850 billion records about phone calls, emails, cellphone locations, and internet chats, according to classified documents obtained by The Intercept.
The documents provide the first definitive evidence that the NSA has for years made massive amounts of surveillance data directly accessible to domestic law enforcement agencies. Planning documents for ICREACH, as the search engine is called, cite the Federal Bureau of Investigation and the Drug Enforcement Administration as key participants.
ICREACH contains information on the private communications of foreigners and, it appears, millions of records on American citizens who have not been accused of any wrongdoing. Details about its existence are contained in the archive of materials provided to The Intercept by NSA whistleblower Edward Snowden. Exclusive: NSA pays £100m in secret funding for GCHQ. The US government has paid at least £100m to the UK spy agency GCHQ over the last three years to secure access to and influence over Britain's intelligence gathering programmes.
The top secret payments are set out in documents which make clear that the Americans expect a return on the investment, and that GCHQ has to work hard to meet their demands. "GCHQ must pull its weight and be seen to pull its weight," a GCHQ strategy briefing said. Edward Snowden condemns Britain's emergency surveillance bill. Loaded: 0% Progress: 0% The NSA whistleblower Edward Snowden has condemned the new surveillance bill being pushed through the UK's parliament this week, expressing concern about the speed at which it is being done, lack of public debate, fear-mongering and what he described as increased powers of intrusion.
In an exclusive interview with the Guardian in Moscow, Snowden said it was very unusual for a public body to pass an emergency law such as this in circumstances other than a time of total war. "I mean we don't have bombs falling. We don't have U-boats in the harbour. " Suddenly it is a priority, he said, after the government had ignored it for an entire year. Sites/all/files/fusion_centers.pdf. Subrealism: xkeyscore renders the security state more powerful than the 1% (deep state) Targetfreedom | Apparently the criminals in the United States government now have a vested interest in keeping Edward Snowden alive and safe.
Britain's response to the NSA story? Back off and shut up. William Hague told the Commons that every intercept had to be personally signed by him.
Link to video: NSA Prism programme: William Hague makes statement on GCHQ On Monday the Guardian carried a story that British intelligence had spied on delegates at two G20 summits, those chaired by Gordon Brown in 2009. Laptops and mobile phones had been hacked, and internet cafes installed and bugged. Obama's Pledge to Curtail NSA Phone Meta Data Collection is Meaningless - Here's Why.
Sorry to burst your bubble, but Obama's recent announcement regarding the scaling back of the NSA's phone metadata collection, was not a watershed moment. This was nothing but a public relations distraction, designed to give the public the illusion of reform. First of all the proposed changes apply only to telephone messages - not email, social media, video cameras, internet searches, Skype calls, etc.
To put this into perspective, none of Edward Snowden's leaks dealt with phone metadata. Boundless Informant: the NSA's secret tool to track global surveillance data. The National Security Agency has developed a powerful tool for recording and analysing where its intelligence comes from, raising questions about its repeated assurances to Congress that it cannot keep track of all the surveillance it performs on American communications. The Guardian has acquired top-secret documents about the NSA datamining tool, called Boundless Informant, that details and even maps by country the voluminous amount of information it collects from computer and telephone networks.
The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message. The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. NSA paying U.S. companies for access to communications networks. New details of the corporate-partner project, which falls under the NSA’s Special Source Operations, confirm that the agency taps into “high volume circuit and packet-switched networks,” according to the spending blueprint for fiscal 2013.
The program was expected to cost $278 million in the current fiscal year, down nearly one-third from its peak of $394 million in 2011. Voluntary cooperation from the “backbone” providers of global communications dates to the 1970s under the cover name BLARNEY, according to documents provided by former NSA contractor Edward Snowden. These relationships long predate the PRISM program disclosed in June, under which American technology companies hand over customer data after receiving orders from the Foreign Intelligence Surveillance Court. In briefing slides, the NSA described BLARNEY and three other corporate projects — OAKSTAR, FAIRVIEW and STORMBREW — under the heading of “passive” or “upstream” collection. “They lose a ton of money,” Gidari said. Sites/all/files/fusion_centers.pdf. On 6/5, 65 Things We Know About NSA Surveillance That We Didn’t Know a Year Ago.
It’s been one year since the Guardian first published the Foreign Intelligence Surveillance Court order, leaked by former NSA contractor Edward Snowden, that demonstrated that the NSA was conducting dragnet surveillance on millions of innocent people. Since then, the onslaught of disturbing revelations, from disclosures, admissions from government officials, Freedom of Information Act requests, and lawsuits, has been nonstop. On the anniversary of that first leak, here are 65 things we know about NSA spying that we did not know a year ago: 1. We saw an example of the court orders that authorize the NSA to collect virtually every phone call record in the United States—that’s who you call, who calls you, when, for how long, and sometimes where. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14.
NSA Intercepts Hardware And Installs Surveillance Equipment. For years, the US government loudly warned the world that Chinese routers and other internet devices pose a "threat" because they are built with backdoor surveillance functionality that gives the Chinese government the ability to spy on anyone using them. Yet what the NSA's documents show is that Americans have been engaged in precisely the activity that the US accused the Chinese of doing. The drumbeat of American accusations against Chinese internet device manufacturers was unrelenting. In 2012, for example, a report from the House Intelligence Committee, headed by Mike Rogers, claimed that Huawei and ZTE, the top two Chinese telecommunications equipment companies, "may be violating United States laws" and have "not followed United States legal obligations or international standards of business behaviour".
Why Can’t Obama End NSA Spying? Since when has the President waited for Congressional authority to do anything? Steve WatsonInfowars.com March 26th, 2014 Senator Rand Paul called out the president Tuesday, urging that if he were really serious about ending NSA bulk data collection, then he would do it immediately.
Rand Paul “who is truly in charge of our government” Update: Paul’s full speech can be viewed below. Warns of “dystopian nightmares” coming true Steve Watson Infowars.com March 19, 2014. » Justice Scalia ‘Foolish’ to Have the Supreme Court Decide If NSA Wiretapping Is Unconstitutional Alex Jones. Hidden Agenda Behind Rise Of "Domestic Terrorist Label" Flashback: "Obama Lone Wolf Will Be Sovereign" Reid Calls Bundy Supporters Domestic Terrorists Homeland Security Says Your Children Are Terrorists Smart Guns Endanger Children Hold On To The Second Amendment!
Harry Reid Blatantly Lies To America. NSA files decoded: Edward Snowden's surveillance revelations explained. Paper Trail? NSA Releases Email Snowden Sent to Agency Officials. U.S. officials once disputed NSA contractor Edward Snowden’s claim that he had raised questions about the agency’s domestic surveillance programs before he fled the U.S. with thousands of stolen documents, but now confirm that Snowden sent at least one email about the agency’s practices to officials.
Officials Have Warned for 40 Years that Mass Surveillance Would Lead to Tyranny in America. 500 Years of History Shows that Mass Spying Is Always Aimed at Crushing Dissent Washington. It’s Never to Protect Us From Bad Guys No matter which government conducts mass surveillance, they also do it to crush dissent, and then give a false rationale for why they’re doing it. For example, the U.S. Supreme Court noted in Stanford v. NSA 'Secret Interpretation of Patriot Act - Tapping CONTENT, Not Just Metadata.