

Judith Sargentini sur Twitter : "Onze regeringen bespioneren advocaten en nu zelfs @amnesty. GCHQ spied on Amnesty International. Jan sur Twitter : ""@Sloopkogel: Positie Merkel wankelt: We're all living in America... Edward Snowden Tells John Oliver The Government Is Collecting 'Dick Pics' - Spook Magazine. Court Ruling Says GCHQ's Mass Internet Surveillance Was Unlawful - BuzzFeed News. UK, US behind Regin malware, attacked European Union networks. Blame the British and American spy agencies for the latest state-sponsored malware attack, say reporters at The Intercept.
Ex- NSA chief now cozy with Israel as he promotes cyber false flags. Cooperation key to cyber-security, says ex-NSA head. Survival of society as we know it in the battle against cyber-criminals and terrorists requires cooperation involving industry academia and investors.
Expert Witness For Silk Road Suggests FBI Lied About How They Accessed Back-End Servers. According to a court document released today, expert witness Joshua J.
Did the FBI Lie About the Ross Ulbricht Silk Road Case? In any sort of criminal investigation, FBI agents must act responsibly—and legally—when collecting evidence on their suspect.
If they don’t, the evidence might not be admissible in court. On Sept. 23, the legal team for alleged Silk Road operator Ross Ulbricht—headed up by famed criminal defense attorney Joshua Dratel—will attempt to throw a wrench into the prosecution’s case by calling into question the FBI’s murky explanation of how federal agents caught their client. Specifically, they’re going to request more information on how the federal agents got access to Ulbricht’s IP address without some serious, NSA-style illegal hacking. Israel’s N.S.A. Scandal. Photo WASHINGTON — IN Moscow this summer, while reporting a story for Wired magazine, I had the rare opportunity to hang out for three days with Edward J.
Snowden. It gave me a chance to get a deeper understanding of who he is and why, as a National Security Agency contractor, he took the momentous step of leaking hundreds of thousands of classified documents. Among his most shocking discoveries, he told me, was the fact that the N.S.A. was routinely passing along the private communications of Americans to a large and very secretive Israeli military organization known as Unit 8200. Talk - Alfred McCoy - Surveillance State: The Making of the U.S. Internal Security Apparatus. Candidate Obama debates President Obama on Government Surveillance. Sander Faas sur Twitter : "Over de verraderlijke draai van Laflinks in zake de politiestaat. #aivd #nsa #snowden #sp... Mystery Solved: The Truth About 'Fake Cellphone Towers' Fake Cell Towers Allow the NSA and Police to Keep Track of You. The Internet is abuzz with reports of mysterious devices sprinkled across America—many of them on military bases—that connect to your phone by mimicking cell phone towers and sucking up your data.
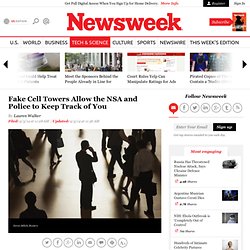
There is little public information about these devices, but they are the new favorite toy of government agencies of all stripes; everyone from the National Security Agency to local police forces are using them. These fake towers, known as “interceptors,” were discovered in July by users of the CryptoPhone500, one of the ultra-secure cell phones released after Edward Snowden’s leaks about NSA snooping. The phone is essentially a Samsung Galaxy S3 customized with high-level encryption that costs around $3,500. Newsweek Magazine is Back In Print Map showing the location of rogue cell towers identified by the firewall on CryptoPhones in August via ESD America, a defense and law enforcement technology provider based in Las Vegas. This NSA-style surveillance is spreading to local cops. 'Nederlandse rechtbank legitimeert privacyinbreuk' Still Report #288 - NSA's Bill Binney - Part 1. Report blasts "unscrupulous" U.S. surveillance in China. BEIJING, May 26 (Xinhua) -- A Chinese Internet information body has complained of "unscrupulous" surveillance by U.S. intelligence agencies over the rest of the world, and called for an immediate cessation of the practice.
A report by China's Internet Media Research Center published on Monday said the U.S. has taken advantage of its political, economic, military and technological hegemony to spy without restraint on other countries, including its allies. The operations have gone "far beyond the legal rationale of 'anti-terrorism' and have exposed the ugly face of its pursuit of self-interest in complete disregard for moral integrity," the report read. It added that the spying "flagrantly infringed international laws, seriously impinged on human rights and put global cyber security under threat. " In particular, it described China as a main target of the U.S. secret surveillance. Chinese authorities have looked into the U.S. Related: China Voice: Big Brother USA's spy charges are absurd.
When you talk too much for Twitter. Instagram. NSA Said to Exploit Heartbleed Bug for Intelligence for Years. The U.S.
National Security Agency knew for at least two years about a flaw in the way that many websites send sensitive information, now dubbed the Heartbleed bug, and regularly used it to gather critical intelligence, two people familiar with the matter said. The NSA’s decision to keep the bug secret in pursuit of national security interests threatens to renew the rancorous debate over the role of the government’s top computer experts. Heartbleed appears to be one of the biggest glitches in the Internet’s history, a flaw in the basic security of as many as two-thirds of the world’s websites. Its discovery and the creation of a fix by researchers five days ago prompted consumers to change their passwords, the Canadian government to suspend electronic tax filing and computer companies including Cisco Systems Inc. to Juniper Networks Inc. to provide patches for their systems.
Related: Controversial Practice. Obama's Pledge to Curtail NSA Phone Meta Data Collection is Meaningless - Here's Why. Sorry to burst your bubble, but Obama's recent announcement regarding the scaling back of the NSA's phone metadata collection, was not a watershed moment.
This was nothing but a public relations distraction, designed to give the public the illusion of reform. First of all the proposed changes apply only to telephone messages - not email, social media, video cameras, internet searches, Skype calls, etc. To put this into perspective, none of Edward Snowden's leaks dealt with phone metadata. BFP Exclusive- Former CIA Officer & Whistleblower Frank Snepp Responds to Sibel Edmonds’ Article on Snowden-Greenwald. The Snowden Effect: From Governmentalized to Privatized & Commoditized.
Sibel Edmonds Interviewed About Edward Snowden and Glenn Greenwald. 'NSA zet EU onder druk om spionage mogelijk te maken' Foto: Channel4 / AFP Dat schrijft klokkenluider Edward Snowden, die documenten over NSA-spionage aan verschillende journalisten doorspeelde, in antwoord op vragen van Europarlementariërs (.pdf).

Snowden noemt Zweden en Nederland als specifieke voorbeelden van landen waar de NSA op deze manier te werk is gegaan. "Een van de de belangrijkste activiteiten van de 'Foreign Affairs Division' van de NSA is om EU-lidstaten onder druk te zetten of te stimuleren om hun wetten te veranderen, zodat massasurveillance mogelijk is", schrijft Snowden. The Al Qaeda Underwear Bomber: Another Foiled False Flag. Wikipedia defines false or black flags as “covert operations designed to deceive the public in such a way that the operations appear as though they are being carried out by other entities.” “The name is derived from the military concept of flying false colors; that is: flying the flag of a country other than one’s own. False flag operations are not limited to war and counter-insurgency operations and can be used during peace-time.”
Big lies substitute for truth. NSA spying poses “direct threat to journalism,” watchdog group warns. By Kate Randall 14 February 2014 Massive spying by the National Security Agency (NSA) poses a “direct threat to journalism,” according to a report by the Committee to Protect Journalists (CPJ) released Wednesday. SenSanders: What I worry about... #NSA... Omidyar’s First Look Introduces The Intercept. The Intercept, the first of First Look’s many intended specialty magazines debuted today. It mostly sucks, but not in such an interesting way that one need belabor the details.
However, since this is the debut issue, I’m going to pass along a few quick thoughts, on my way to encouraging people to start ignoring First Look and all media like it completely: 1. HolladieJan : #Snowden #NSA #Cartoon... NSA Whistleblower: Global Mass Surveillance Protesters Demand Too Little.