

Jabber Features. Easily access voice, video, presence, instant messaging, voice messaging, desktop sharing, and conferencing capabilities.
SAN Based replication ? no problem.. latency.. Problem.. Disaster recovery has become something which is moving higher and higher up agenda on companies “to do” list.

Its becoming increasingly more apparent what the costs to a given business are when companies suffer downtime and/or loss of data.. people are starting to think about the monetary cost to the business is when services or applications are unavailable to both internal staff and more importantly customers and with the big push of server virtualization over the last few years.. where is application data/file data/the application server itself sitting ?
On the SAN; so it makes sense to leverage that existing infrastructure in the SAN and use some form of SAN based replication. So what do you do to make sure the DR solution you have in mind is feasible and realistic ? Firstly make sure you pick the right technology First port of call is sitting down with the customer and mapping out the availability requirements of their applications. Demo Environment. Hire, Find and Review Tested Programmers and IT, Web & Mobile Freelancers. Elance is where businesses go to find, hire, manage and pay top online freelancers.
This includes skilled IT Freelancers, Web Freelancers and Mobile Freelancers with the expertise needed to make your web pages and mobile applications effective and efficient. 3 Steps Your Company Needs to Take Right Now to Protect Your Data. We all know that the bad guys are getting more sophisticated and determined to invade business networks. If we just look at the first week of 2013, there was a series of well-publicized Java exploits, watering hole campaigns, and denial of service attacks – and that was just the first week of the year.
Securing your company’s data is not a destination but a constant process, and one where you need to be vigilant and always look for ways to better protect your networks, servers and user laptops. Companies, specifically small companies, can often rely on in-house staff or local IT providers to help manage this element of their business, however it can still leave vital functions, such as network security, at risk. Here are three important steps to take to beef up your data security. Cisco Switches. Basic & Advanced Catalyst Layer 3 Switch Configuration: Creating VLANs, InterVLAN Routing (SVI), VLAN Security, VTP, Trunk Link, NTP Configuration. IOS License Requirements for SVI Routing. This article covers basic and advanced configuration of Cisco Catalyst Layer 3 switches such as the Cisco Catalyst 3560G, 3560E, 3560-X, 3750, 3750E, 3750-X, 3850 and 4500 series, and extends to include the configuration of additional features considered important to the secure and correct operation of these devices.

In many cases, these Catalyst Layer 3 switches are purchase and installed with basic configuration or features enabled, without leveraging their layer 3 capabilities. After observing many installations that fell into this category (almost out of the box configurations), we decided it was a great idea to begin covering configuration best-practices that will help engineers understand the capabilities of this equipment and better adapt configurations to their company needs. The topics covered in this article include: Configuring IOS Zone-based Firewall with CCP. Cisco.
Build Redundant IP Routing. FocusBuild Redundant IP RoutingProvide a disaster-resistant vehicle to safely carry your e-business onto the internet By Tao Zhou Successful e-commerce relies heavily on IP routing, which delivers e-business information from one company to another.
Without a redundant and fault-tolerant IP routing mechanism, a company's e-business can't survive disasters (e.g., hurricanes, floods, power outages, Internet-connection disruptions, equipment failures) because the company doesn't have an alternative method to reach the Internet. Product Support Visio Stencils. Photographic Blending of Relatives A Genetic Study by Ulric Collette. What do you get when you blend the science of genetics, photographic excellence, and amazing digital artistic talent?
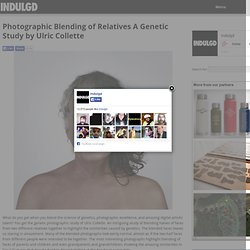
You get the genetic photographic study of Ulric Collette. An intriguing study of blending halves of faces from two different relatives together to highlight the similarities caused by genetics. The blended faces leaves us staring in amazement. Many of the blended photographs look eerily normal, almost as if the two half faces from different people were intended to be together. The most interesting photographs highlight blending of faces of parents and children and even grandparents and grandchildren, showing the amazing similarities in facial features that may be hard to discern looking at the two faces separately. A stunning element of this study is the precise blending and invisible meshing the photographs that Ulric Collette has accomplished allowing us to focus on the faces instead of the line of change.
Nexus 5000 Series NX-OS Software Configuration Guide - Configuring Access and Trunk Interfaces [Cisco Nexus 5000 Series Switches. Table Of Contents Configuring Access and Trunk Interfaces Information About Access and Trunk Interfaces Understanding Access and Trunk Interfaces Understanding IEEE 802.1Q Encapsulation Understanding Access VLANs Understanding the Native VLAN ID for Trunk Ports Understanding Allowed VLANs Configuring Access and Trunk Interfaces Configuring a LAN Interface as an Ethernet Access Port Configuring Access Host Ports Configuring Trunk Ports Configuring the Native VLAN for 802.1Q Trunking Ports Configuring the Allowed VLANs for Trunking Ports Verifying Interface Configuration Configuring Access and Trunk Interfaces Ethernet interfaces can be configured either as access ports or trunk ports.
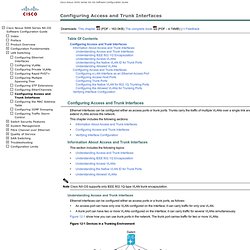
Trunks carry the traffic of multiple VLANs over a single link and allow you to extend VLANs across the network. Recently Active Questions. Adding DNS Records. Now that you've set up a Linode and started hosting a website, it's time to point a domain name at your server and your website.
To do that, you'll use something called the Domain Name System (DNS), which is the Internet's address book. DNS is responsible for directing web traffic to your Linode and emails to your inbox. It maps memorable domain names like example.com to IP addresses like 12.34.56.78. This guide explains how to create basic DNS records for your website, introduces some advanced DNS configurations, and provides basic troubleshooting steps. Before adding any DNS records, you should learn the basics of DNS. Domain Names. Platform » Resolvity. VoiceXML and CCXML Developer Site. HelpServer - Voxeo Support. Access Denied. Un paseo por la 'netbook' de Google que es totalmente online - Tecnología.
(CNNMéxico) — Por ahora, la netbook de Google, Cr-48, es una prueba piloto para que desarrolladores y geeks (principalmente estadounidenses) la evalúen y den su opinión sobre el futuro sistema operativo (SO): Chrome, pues el objetivo de la compañía californiana no es dedicarse a la fabricación de hardware, sino obtener la mayor cantidad de retroalimentación para mejorar el SO y que éste sea adoptado por las fabricantes, al igual que su sistema operativo para móviles: Android.
Basta apretar el botón de encendido para que (en cuestión de segundos) esta laptop solicite tu nombre y contraseña de Gmail. Una vez que ingresas, se abre el navegador Chrome y las primeras preguntas llegan a tu cabeza: “¿Dónde está el escritorio? , ¿Cómo minimizo la pantalla? , ¿Cómo descargo programas? Y finalmente, ¿Cómo dejo de ver el navegador?”. Lo importante de Chrome OS es que se basa en la rapidez y estabilidad del navegador que lleva el mismo nombre. BGP for Internet Service Providers.
Soluciones gobierno. La información contenida en esta página y sus enlaces se proporciona "tal cual", sin garantía de ningún tipo, ya sea expresa o implícita, incluyendo, pero no limitándose a, las garantías implícitas de uso para fines de mercado, conveniencia para un propósito, o la no-infracción.
Ciertas jurisdicciones no permiten la exclusión de las garantías implícitas, así que la exclusión anterior podría no aplicar para usted. A pesar de que la información de esta página se considera exacta, es posible que contenga inexactitudes técnicas o errores tipográficos. 2013 Future of Cloud Computing - 3rd Annual Survey Results. Types of Backup Explained. Call Center Director Benefits. Commerce Workspace - Cisco Systems. Could that be a solution? 50 Disruptive Companies 2013. SaaS. El uso de sistemas cibernéticos de pago en el lavado de dinero. Www.cfnavarra.es/observatoriosi/pdf/estudio_inteco_cloud_computing_en_sector_publico/estudio_inteco_cloud_computing_en_sector_publico.pdf. The Business Value of Digital Transformation - Mike Pearl, PWC - Part 1.
View 13: Cloud computing gets strategic: Reducing technology costs is just the starting point. By Phil Garland, Rob Gittings, and Mike Pearl What a difference a year makes. Last fall, View introduced readers to what we called the latest technology trend to capture the attention of businesses, consumers, and investors alike. That description of cloud computing was apt: Momentum—along with considerable hype—for the new approach and its supporting technologies has been considerable. But the real impact is only now beginning to be felt. A year ago, cloud was squarely in the IT domain; now, it’s making its way to the boardroom.
Www.cemla.org/actividades/2012/2012-12-vigilanciasistemasdepago-backgroundnote-sp.pdf. Download. Citrix VDI-in-a-Box. Seguridad de Oscar Orjuela en Prezi. Programa IX Semana de la Facultad de Economía, Empresa y Negocios. Gestión de Riesgo en la Seguridad Informática. La eficiente integración de los aspectos de la Seguridad Informática en el ámbito de las organizaciones sociales centroamericanas enfrenta algunos retos muy comunes que están relacionados con el funcionamiento y las características de estas. Solutions - Cloud Computing - Service Providers. Cloud Computing - Whiteboard Video. Columbus Data Center Video. Managed Hosting Services and Cloud Computing. Cloud Computing Best Animation. Types of cloud computing: Public, Private & Hybrid cloud explained. What is a private cloud computing? - CloudPro. Search Results for cloud computing.
Banamex y Telcel ofrecen banca móvil por SMS. Search results - jechangm - Gmail. DynaTAC to iPhone: A History of Wireless Phones. If you have been around for a while, you are a witness to the fastest evolution of technology in history. Wireless Phones (also called mobile phones and cell phones) are no exception to this statement. Since 1983 ,they changing shape so fast that it is breathtaking to watch to advancements. If someone slept all the time from 1980′s to this day, It would be very difficult for him to recognize most of the stuff around him. vNewB: The Virtual Legacy.
We can see more and more ads or products using the magical and trendy word , but nobody explains us what is really that … So how can we define Cloud Computing? Let’s take the definition we can find on Wikipedia, which is the website people use when they are looking for a quick definition: So, as you can see, these two definitions comming from the same source are differents. That shows the definition of Cloud Computing is still quite Well, the general idea is the same for everyone: people acces to data/software/hardware from their chair to a remote point, somewhere on the web.
Webconference: Cloud computing, un paseo por la Nube. How to Identify Cloud Washing. Charles Babcock at Information Week, a site I once wrote for, delivered a great piece yesterday on what he calls “cloud washing.” It's similar to things I was writing about in September, when Marc Benioff of Salesforce.com (CRM) was playing the feud with Larry Ellison of Oracle (ORCL) . Here at Seeking Alpha I wrote about it as Cloud or Not a Cloud. Babcock's story has a great definition of cloud computing, one investors need to memorize and understand completely: To actually be part of the cloud requires systems that run on a simplified data center architecture, operated largely by automated policies, not human hands.
The architecture allows end users to self-provision their own servers, and has a billing mechanism that allows the supplier to charge only for the resource used, not the lifetime software license cost. I've boldfaced the important parts. The pattern in this case is more important than the names, and the definition more important than the pattern. Is this author on the ball? Beware of Cloud Washing! The Matrix - Un-Official Trailer HD (1999) What Is Cloud Computing PPT 2. The Three Ways to Cloud Compute. Maurice Jarre - A WALK IN THE CLOUDS (1995) - Soundtrack Suite.