

Mobile cloud computing. Mobile/cloud computing is the combination of cloud computing and mobile networks to bring benefits for mobile users, network operators, as well as cloud computing providers.[1][2] The ultimate goal of MCC (mean of MCC is Mobile/Cloud Computing) is to enable execution of rich mobile applications on a plethora of mobile devices, with a rich user experience.[3] MCC provides business opportunities for mobile network operators as well as cloud providers.[4] More comprehensively, MCC can be defined as "a rich mobile computing technology that leverages unified elastic resources of varied clouds and network technologies toward unrestricted functionality, storage, and mobility to serve a multitude of mobile devices anywhere, anytime through the channel of Ethernet or Internet regardless of heterogeneous environments and platforms based on the pay-as-you-use principle.
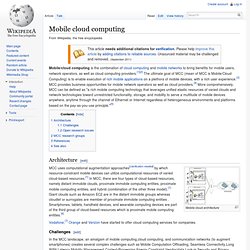
"[5] Architecture[edit] Mobile cloud architecture Challenges[edit] Open research issues[edit] MCC research groups[edit] References[edit] Cloud_Computing_Strategy_v1_0. Governments Move to the Cloud for Mobile Security. With some 10,000 devices to manage across a large and diverse workforce, the IT team that manages mobile devices for the state of Michigan opted for a cloud-based solution.
John McQuaid, IT manager, and Linda Baker, smart device support team manager, say Fiberlink Maas360 offers them an affordable product that lets them quickly deploy mobile devices without having to set up equipment onsite at headquarters in Lansing. Most of the state’s smartphones and tablets are iOS-based, and the department also supports Android and Windows phones. “There’s no way we could go out in the field and touch every one of those devices by hand,” Baker says, pointing out that the mobile group has only four full-time staffers and two students.
“We can also push configuration options to devices remotely; for example, sending out a device’s Wi-Fi or email settings.” The percentage of IT managers who say they have experienced a breach or data loss in which a mobile device was a factor SOURCE: “U.S. Cloud. Security Firms Scour Mobile Apps. By John P.
Mello Jr.TechNewsWorld 02/24/14 4:19 PM PT Many developers allow risky behaviors in their apps in order to remain in business. "They're stuck in a difficult position because of how difficult it is to monetize their apps," said Appthority President Domingo Guerra. "In general, folks are not paying for applications. They'd rather download the apps for free or pay 99 cents. " Security pros weren't very kind to mobile applications last week.
While Android has been a poster child for misbehaving apps in the past, competitor Apple's apps aren't as pristine as is commonly believed, suggests a report from Appthority. Ninety-one percent of the top 400 free and paid iOS apps exhibited risky behaviors, compared to 83 percent of the top 400 paid and free Android apps, according to its Winter 2014 App Reputation Report. "But what we've seen is that security includes privacy, data loss and vulnerabilities," he told TechNewsWorld. Risky Business More Bad News. Exposing the cracks in cloud security. Share article 0googleplus Short of time?
Print this pageEmail article Put simply, one of the principal benefits of cloud computing is that the user does not need to worry about the hardware configuration powering their IT services. But the flipside of the same coin is that they do not have visibility into that configuration. This lack of visibility is the source of much of the anxiety surrounding the security of the cloud. Last year, security consultancy Context took an in-depth look at four established cloud providers in order to audit their security measures. It found that two of the four cloud providers, Rackspace and VPS.NET, had serious security vulnerabilities. The data fragments they discovered, Context analysts Michael Jordon and James Forshaw said in a blog post, “included some personal identifiable information, such as parts of customer databases and elements of system information such as Linux shadow files (containing the system’s password hashes)”.
Cloud Security. The Best Security for Wireless Networks. Securing a wireless network isn't a hard task.

The cheat sheet is relatively small. However, the technical press continues to be flooded with articles and blogs containing technical mistakes. Take, for example, everyone's trusted information source, Consumer Reports Magazine. I'm a big fan of the magazine, having subscribed to the hard copy edition for years. But they seem out of their league, when it comes to computers. On August 6, 2009 a blog posting at the magazine's website suggested using WEP security for wireless networks. So, let me try to offer up just what most people (and Consumer Reports) need to know about securing a wireless network. Starting at the Beginning To begin with, there are four types of Wi-Fi networks (A, B, G and N).
If you can connect to a wireless network without entering a password, then there is no security. Wi-Fi networks offer three security options: WEP, WPA and WPA2. WEP is the oldest security option and it has been shown to be very weak. WPA TKIP Flaws.