

EnergyWise IOS Deployment Guide - Setting Recurring Events [Cisco Energy Management Suite] You can configure the switch to power an end point or interface on and off based on the time or date.
![EnergyWise IOS Deployment Guide - Setting Recurring Events [Cisco Energy Management Suite]](http://cdn.pearltrees.com/s/pic/th/energywise-deployment-238768680)
A recurring event, also referred to as a recurrence, uses the switch time Examples To configure a recurring event with a time range when the switch powers off the phone at 2000 (8 p.m.) on Switch A Note EnergyWise uses only the start time in the time range. SwitchA# configure terminal Enter configuration commands, one per line. Products - Visio Stencils. B APIC Troubleshooting. HyperFlex - Unable to access ESXi Shell...
Symptoms Usually, we can access ESXi Shell by pressing Alt+F1 from ESXi DCUI (Direct Console User Interface).
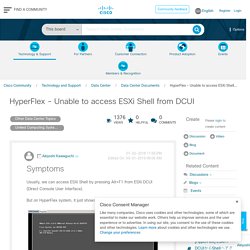
But on HyperFlex system, it just shows black window. Diagnosis. Troubleshooting When BGP Routes Are Not Advertised. Introduction The purpose of this document is to provide a systematic approach to help troubleshoot situations when a Border Gateway Protocol (BGP) router does not announce BGP routes to peers.
There are multiple ways in which a prefix is added to a BGP table and announced to peers: Issue the basic network command under router BGP. This method is used to originate BGP routes from the autonomous system (AS). Refer to the network command section of BGP Case Studies 1 for more information. Peer Gateway Feature on the Nexus 7000. What is peer gateway?
Peer gateway is a feature which was developed to support network devices which use non-standard layer 2 packet forwarding in a vPC environment. This was first discovered by NetApp using the fastpath feature but other devices have started using this method as well over the years. How exactly does this non-standard layer 2 forwarding work? Solved: RTMT traces. Online labs - SharonTools. Find out ARP for Entire Bridge Domain. Sri, Instead of ARP entries, the fabric will install endpoint entries.
For L3 bridge domains (unicast routing enabled), the BD/EPG will learn both IP and MAC from both ARP and data plane traffic. To check the endpoint per EPG, you can do 2 different ways. ACI Fabric Endpoint Learning White Paper. Contents Introduction. 3 Goals of this document 3.
Learning ACI · Adam Raffe. This is a series of blog posts I wrote a few years back whilst working on the Application Centric Infrastructure solution at Cisco.
I no longer work at Cisco and won’t be updating these posts; however, I’m keeping them here as they may still be useful for people starting out with ACI. Here is a consolidated list of blog entries in the Learning ACI series: Part 1: Overview – Provides a very high level overview of ACI and what to expect from the blog series Part 2: Bringing Up An ACI Fabric – Part 2 takes you through bringing up an ACI fabric for the first time, provisioning an APIC cluster and discovering the leaf and spine switching nodes in your network. Part 3: Getting Familiar with the APIC – In this part, I take you through a tour of the APIC GUI, explaining what functionality is found under the main tabs. Configure Fast LACP Timer in ACI. Introduction This document describes how to configure fast Link Aggregation Control Protocol (LACP) timer for port-channel in Cisco Application Centric Infrastructure (ACI).
Prerequisites. Cisco Nexus 9000 Series NX-OS System Management Configuration Guide, Release 6.x - Configuring Rollback [Cisco Nexus 9000 Series Switches] Nexus 9000 Series NX-OS Interfaces Configuration Guide, Release 6.x - Configuring Layer 2 Interfaces [Cisco Nexus 9000 Series Switches] A Layer 2 port can be configured as an access or a trunk port as follows: An access port can have only one VLAN configured on that port; it can carry traffic for only one VLAN.
![Nexus 9000 Series NX-OS Interfaces Configuration Guide, Release 6.x - Configuring Layer 2 Interfaces [Cisco Nexus 9000 Series Switches]](http://cdn.pearltrees.com/s/pic/th/configuration-configuring-195208624)
A trunk port can have two or more VLANs configured on that port; it can carry traffic for several VLANs simultaneously. By default, all ports on the device are Layer 3 ports. APIC REST API Configuration Guide - Provisioning Layer 2 Networks [Cisco Application Policy Infrastructure Controller (APIC)] Maximum uplink port limit When the maximum uplink port limit is reached and ports 25 and 27 are converted from uplink to downlink and back to uplink on Cisco 93180LC-EX switches: On Cisco 93180LC-EX Switches, ports 25 and 27 are the native uplink ports.
![APIC REST API Configuration Guide - Provisioning Layer 2 Networks [Cisco Application Policy Infrastructure Controller (APIC)]](http://cdn.pearltrees.com/s/pic/th/configuration-infrastructure-194881483)
Using the port profile, if you convert port 25 and 27 to downlink ports, ports 29, 30, 31, and 32 are still available as four native uplink ports. Because of the threshold on the number of ports (which is maximum of 12 ports) that can be converted, you can convert 8 more downlink ports to uplink ports. For example, ports 1, 3, 5, 7, 9, 13, 15, 17 are converted to uplink ports and ports 29, 30, 31 and 32 are the 4 native uplink ports (the maximum uplink port limit on Cisco 93180LC-EX switches). APIC REST API Configuration Guide - Using the REST API [Cisco Application Policy Infrastructure Controller (APIC)] ACI CLI Commands "Cheat Sheet" Introduction The goal of this document is to provide a concise list of useful commands to be used in the ACI environment. For in-depth information regarding these commands and their uses, please refer to the ACI CLI Guide. Please note that legacy style commands (show firmware, show version, etc) will not be included in this guide.
Use 'configure replace' Instead of 'copy start run' Newbie Cisco networking admins are typically taught the command copy running-config startup-config, or copy run start, to save their configurations to NVRAM (i.e. Flash memory). (This is in contrast to the older yet much much more convenient write memory command, or simply wr.) Operating Cisco Application Centric Infrastructure - Monitoring [Cisco Application Policy Infrastructure Controller (APIC)] Proactive monitoring is a very important piece of the network administrator's job, but is often neglected because putting out fires in the network usually takes priority. However, since the Application Policy Infrastructure Controller (APIC) makes it incredibly easy to gather statistics and perform analyses, this will save network administrators both time and frustration. Since statistics are gathered automatically and policies are used and can be re-used in other places, the human error and effort is minimal.
Statistics gathering has been a somewhat manual and even resource intensive process for ACME in the past. 802.1X Authentication Services Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) - IEEE 802.1X Voice VLAN [Support & Downloads] 802.1x multi authentication vs 802.1x multi domain authentication - 49774. Hi Scott, m seeing a strange behavior on cc3850 where multi-auth mode also let the hosts (on a port) to participate on both Voice and Data vlan (like multi-domain) Please share your view on this behavior . Logs: switch1#sh run int gigabitEthernet 1/0/3. Howto 81 troubleshooting failed authc. Nexus 5000 Series NX-OS Software Configuration Guide - Configuring Private VLANs [Cisco Nexus 5000 Series Switches] About Private VLANs A private VLAN partitions the Layer 2 broadcast domain of a VLAN into subdomains, allowing you to isolate the ports on the switch from each other. A subdomain consists of a primary VLAN and one or more secondary VLANs (see Figure 1-1).
All VLANs in a private VLAN domain share the same primary VLAN. The secondary VLAN ID differentiates one subdomain from another. The secondary VLANs may either be isolated VLANs or community VLANs. Note. IEEE 802.1X Auth Fail VLAN [Support] - Cisco Systems. You can configure an auth fail VLAN for each 802.1X port on a switch to provide limited services to clients that cannot access the guest VLAN. These clients are 802.1X-compliant and cannot access another VLAN because they fail the authentication process. An auth fail VLAN allows users without valid credentials in an authentication server (typically, visitors to an enterprise) to access a limited set of services. The administrator can control the services available to the auth fail VLAN. Cisco Nexus 5000 Series NX-OS Software Configuration Guide - Configuring Private VLANs [Cisco Nexus 5000 Series Switches] Configure Commonly Used IP ACLs. Introduction This document provides sample configurations for commonly used IP Access Control Lists (ACLs), which filter IP packets based on: Source addressDestination addressType of packetAny combination of these items In order to filter network traffic, ACLs control whether routed packets are forwarded or blocked at the router interface.
Nexus 2000 Fabric Extenders Support & Downloadsed/Unsupported Topologies. IP Routing: BGP Configuration Guide, Cisco IOS XE Release 3S - BGP Support & Downloads for BFD [Cisco IOS XE 3S] Bidirectional Forwarding Detection. Minimum-interval (BFD Liveness Detection) - TechLibrary. Network 101: BGP Community attribute. BGP Community attributes BGP community is a optional attribute of BGP routing protocol. It can be considered as a tag in IGP, making a set of IP addresses. The community strings often use to manipulate route, set BGP attributes for a set of ip addresses. We use access-list or prefix list to assign the community to IP addresses. Once the community attribute has been assigned, it can be changed by the route-map function in the router.
In addition, there are 3 special community values. To assign BGP community string, we use set community <number>/<special community string> in the route-map command. Below is the sample of how to configure BGP special community string and how it works. Establish eBGP connection between R1 and R4 Establish iBGP connection between R1, R2 and R3 with Route-ReflectorR3 advertise its loopback network in BGP with the community string as shown in the figure.Verify route received and community string on R2, R1, and R4 In this example, we expect as followings Note.
Using BGP Community Values to Control Routing Policy in Upstream Provider Network. Configure ASA Version 9.x Port Forwarding with NAT. ACI Fabric Endpoint Learning White Paper. Cisco ASA 5500 Series Configuration Guide using the CLI, 8.2 - Configuring Management Access [Cisco ASA 5500-X Series Firewalls] Cisco ASA 5505 Configuration: 6-Steps Easy Tutorial - RouterFreak. The Cisco ASA 5505 Firewall is the smallest model in the new 5500 Cisco series of hardware appliances.
Although this model is suitable for small businesses, branch offices or even home use, its firewall security capabilities are the same as the biggest models (5510, 5520, 5540 etc). The Adaptive Security technology of the ASA firewalls offers solid and reliable firewall protection, advanced application-aware security, denial of service attack protection and much more. Moreover, the performance of the ASA 5505 appliance supports 150Mbps firewall throughput and 4000 firewall connections per second, which is more than enough for small networks. In this article, I will explain the basic Cisco ASA 5505 configuration for connecting a small network to the Internet (here the complete guides). We assume that our ISP has assigned us a static public IP address (e.g 200.200.200.1 as an example) and that our internal network range is 192.168.1.0/24. Step1: Configure the internal interface vlan. Configure Commonly Used IP ACLs. Cisco UCS C-Series Servers Integrated Management Controller CLI Configuration Guide, Release 1.4 - CIMC Firmware Management [Cisco Integrated Management Controller]
Application Centric Infrastructure — ACI Troubleshooting Book 1.0.1 documentation. Port Monitoring/Mirroring on NX-OS: SPAN Profiles. Port mirroring is a very valuable troubleshooting tool. Cisco calls this SPAN, and it’s pretty easy to do. Cisco’s NX-OS platform does it a little differently than traditional IOS, so I wanted to briefly post a walkthrough. First, you have to set up the monitor session and configure source and destination interfaces: Redistributing Connected Networks into OSPF. Configure and Verify Maximum Transmission Unit on Cisco Nexus Platforms. Cisco Nexus 9000 Series NX-OS Software Upgrade and Downgrade Guide, Release 6.x - Upgrading or Downgrading the Cisco Nexus 9000 Series NX-OS Software [Cisco Nexus 9000 Series Switches] Understanding Ethernet Virtual Circuits... The Problem On traditional switches whenever we have a trunk interface we use the VLAN tag to demultiplex the VLANs. The switch needs to determine which MAC Address table to look in for a forwarding decision.
To do this we require the switch to do two things: Bridge configuration at ISR 4000. Hi. I´m configuring a new router ISR 4000, but i cannot find all needed commands for bridge feature. Please your help if somebody know the equivalent commands for ISR 4000 series. Thanks in advance. Cisco UCS C-Series Servers Integrated Management Controller GUI Configuration Guide, Release 1.5 - Configuring Communication Services [Cisco Integrated Management Controller] - Cisco.
Cisco Unified Contact Center Express Design Guide, Release 10.6(1) - Unified CCX Failover [Cisco Unified Contact Center Express] Virtualization Software Requirements. Some virtualized UCS servers are configured with multiple physical NICs (see UCS page at Network traffic is switched from physical NICs to "vNIC's" of the Virtual Machines (VM) via either VMware vSwitch or Cisco Nexus 1000V. Customers can use these multiple NICs for VM network traffic, VMware console access, or management "back-doors" for administrative access, backups, software updates or other traffic that is desired to be segregated from the VM network traffic. All these uses are supported for UC but note that UC apps like CUCM and UCCX only support a single vNIC with a single IP address. This feature automatically restarts a Virtual Machine (VM) on the same physical server or a different physical server. It can be used to supplement software redundancy as a means of fast, automated Failed-server recovery when a VM (but not the application) is hung or if there is a fault with the physical host server or VMware software.
VMware vNetwork Distributed Switch VMware vMotion Not supported. Virtualization for Cisco Unified Contact Center Express. IP SLAs Configuration Guide, Cisco IOS Release 15M&T - Configuring IP SLAs ICMP Echo Operations [Cisco IOS 15.4M&T] Cisco Support Community. Unable to access CIMC on Cisco UCS server. Error 2001: Service not available. WAN, Routing and Switching. WAN, Routing and Switching. Cisco Host Upgrade Utility 3.0 User Guide - Updating the Firmware on Cisco UCS C-Series Servers [Cisco UCS C-Series Rack Servers]
Cadx106 supervisor desktop user guide. Unified Networking. Cisco Nexus 5000 Series NX-OS Fabric Extender Command Reference - Show Commands [Cisco Nexus 5000 Series Switches] Change Radius-server host to Radius server. Another I.T. blog: IOS Upgrade on Cisco WS-C4507R Chassis with Dual Supervisor V Engines. Nexus 5500 Series NX-OS Software Upgrade and Downgrade Guide, Release 7.1(4)N1(1) Cisco Nexus 5500 Series NX-OS Software Upgrade and Downgrade Guide, Release 7.1(4)N1(1) 802.1x DACL, Per-User ACL, Filter-ID, and Device Tracking Behavior. IEEE 802.1X with ACL Assignments [Support] Pbroute. Cisco Nexus 7000 Series NX-OS Security Configuration Guide, Release 4.1 - Configuring RADIUS [Cisco Nexus 7000 Series Switches] Collecting CUCM Traces from CUCM 8.6.2 for a TAC SR. Configuring iscsi tlv.
Cisco Nexus 5000 Troubleshooting Guide - Troubleshooting FCoE Issues [Cisco Nexus 5000 Series Switches] DCX-No ACK in 100 PDUs Error Message. Using trusted SSL’s in Cisco Unified Communications Manager 10.0. Cisco Support Community.
Cisco Nexus 5000 Series Command Reference - Fabric Extender Commands [Cisco Nexus 5000 Series Switches] Cisco.