

Packages Search - pkgs.org. Emmabuntus:Community portal. How to make Linux more trustworthy. While the fight against government-mandated software backdoors raged for most of 2016—including the showdown between Apple and the FBI over the San Bernardino shooter's iPhone, and the UK's new Investigatory Powers Act, which gives the government the power to demand UK companies backdoor their software to enable mass surveillance—the Core Infrastructure Initiative (CII) has been quietly working to prevent an even more insidious form of backdoor: malicious code inserted during the software build process without a developer’s knowledge or consent.
Such attacks are by no means theoretical. Documents from Snowden's trove make clear that intelligence agencies are actively working to compromise the software build process on individual developer's computers. The CIA created a bogus version of XCode, the software used by developers to package applications for Apple devices. A Beginner Friendly Comprehensive Guide to Installing and Using A Safer Anonymous Operating System v1.0.2. Brutal Toolkit - Create Various Payload, PowerShell & Virus Attack on Kali Linux 2016.2. Pi Zero - Has anyone been able to install Kali Linux? : raspberry_pi. The source for Linux information. The Internet of Things market is fragmented, amorphous, and continually changing, and its very nature requires more than the usual attention to interoperability.
It’s not surprising then, that open source has done quite well here -- customers are hesitant to bet their IoT future on a proprietary platform that may fade or become difficult to customize and interconnect. In this second entry in a four-part series about open source IoT, I have compiled a guide to major open source software projects, focusing on open source tech for home and industrial automation. I am omitting more vertical projects related to IoT, such as Automotive Grade Linux and Dronecode, and I’m also skipping open source, IoT-oriented OS distributions, such as Brillo, Contiki, Mbed, OpenWrt, Ostro, Riot, Ubuntu Snappy Core, UCLinux, and Zephyr. Next week, I’ll cover hardware projects -- from smart home hubs to IoT-focused hacker boards -- and in the final part of the series, I’ll look at distros and the future of IoT. Is your SSH password revealed when you attempt to connect to the wrong server?
GNU Libreboot. 30 days in a terminal: Day 1 — The essentials. Day 1 of my "I'm a ridiculous person who is going to use nothing but a Linux terminal for 30 days" experiment is complete.
And it was not an easy day. Not bad. KDEConnect - KDE Community Wiki. This is the community page for KDE Connect.
Feel free to edit it! KDE on Windows status update. Disclaimer: No, it's not dead :) During Randa we've discussed the KDE on Windows road map.
There's been a brisk involvement of the Randa Meetings participants in the platform discussion sessions on Tuesday. Untitled. After two years of hard work Subgraph OS is finally available for alpha download!
Please note that this software is still in alpha and much testing and bug fixing still has to be done. We strongly encourage you to read the caveats/troubleshooting before you start. System Requirements Anything that can comfortably run GNOME 3: 64-bit machine (Core2Duo or over) 2GB of RAM (4GB recommended) At least 20GB of hard disk space. Grsecurity. The Open Source Security Distribution for Ethical Hackers and Penetration Testers and Forensic Experts. The Matriux is a phenomenon that was waiting to happen.

It is a fully featured security distribution based on Debian consisting of a powerful bunch of more than 300 open source and free tools that can be used for various purposes including, but not limited to, penetration testing, ethical hacking, system and network administration, cyber forensics investigations, security testing, vulnerability analysis, and much more. It is a distribution designed for security enthusiasts and professionals, although it can be used normally as your default desktop system. With Matriux, you can turn any system into a powerful penetration testing toolkit, without having to install any software into your hardisk. Matriux is designed to run from a Live environment like a CD / DVD or USB stick or it can easily be installed to your hard disk in a few steps. How to install Asterisk PBX 13.x on CentOS 7 step by step guide. Hello guys, we're going to do Asterisk 13.0.6 installation in this guide.
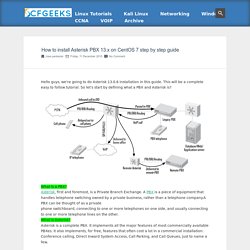
This will be a complete easy to follow tutorial. Ringing in 2016 with 64 open-spec, hacker friendly SBCs · LinuxGizmos.com. Community backed, open-spec SBCs vary wildly, from sub-$10 minimalists to octa-core powerhouses.
Here we present 64 Linux- and Android-friendly models. In 2015, the number of open-spec, hacker friendly single board computers running Linux or Android has continued to grow while prices have dropped to unprecedented levels. Low-cost boards such as the Chip, Raspberry Pi Zero, and Orange Pi PC have set a higher bar for price/performance ratio, while on the high end, we saw the first 64-bit, ARMv8 hacker SBCs arrive at surprisingly low prices. Meanwhile, the board that matters most to makers around the world — the Raspberry Pi — was updated to a Pi 2 model with a modern quad-core, ARMv7 processor that opens up new applications and a wider range of Linux distributions. In our first joint reader survey of community-backed boards with Linux.com in May 2014, readers rated their favorite SBCs from a list of 32. Our list could actually be much longer than 64. .bashrc generator: create your .bashrc PS1 with a drag and drop interface. Hackme: Deconstructing an ELF File.
A friend recently asked me to find the password for a little hard-to-hack program he had written and I agreed to it.

The short journey of a few hours that led me to its password were extremely interesting and this article describes the process as well as some of the new techniques learnt along the way. Few minutes after accepting his challenge, I received a binary called "hackme" in an E-mail and I got started! Those interested in giving it a shot can download the binary file and get back to this article later. Do let me know if you find anything interesting along the way that I did not think of or missed! Robbyrussell/oh-my-zsh.
All commands sorted by votes. Linux. The GNU Operating System. DistroWatch.com: Put the fun back into computing. Use Linux, BSD. The Linux Alternative Project.