

How To Recycle HDPE Plastic (High Density Polyethylene) - a simple method. A Neuroscientist's Radical Theory of How Networks Become Conscious - Wired Science. It’s a question that’s perplexed philosophers for centuries and scientists for decades: Where does consciousness come from?

We know it exists, at least in ourselves. But how it arises from chemistry and electricity in our brains is an unsolved mystery. Neuroscientist Christof Koch, chief scientific officer at the Allen Institute for Brain Science, thinks he might know the answer. Internet bonding - Uplink Bonding. Acceleration - The optional Internet bonding service (Broadband Bonding Service) enables uplink bonding, therefore with BBS all traffic is aggregated for faster transfer via the Broadband Bonding(TM) technology.
Even in cases of single session, all Internet access lines are simultaneously combined together to provide a faster data transfer. Pictured below is a Truffle device bonding 6 Internet access modems. Improved network reliability - With the Internet bonding service, automatic failover is provided for all types of traffic, so that failure of one or more access lines will not cause failure of the aggregated access line, as long as at least one access line is still active. Additionally, Automated Domain Name Service (ADNS) optimization is used to maximize the utility of all active access lines. Minds. ERO - Concrete Recycling Robot by Omer Haciomeroglu. This robot sucks!
Literally! NASA Brings WiFi To Space. Robotics. HUANG YI & KUKA - A DUET OF HUMAN AND ROBOT. Physicists To Test If Universe Is A Computer Simulation. Physicists have devised a new experiment to test if the universe is a computer.
A philosophical thought experiment has long held that it is more likely than not that we're living inside a machine. The theory basically goes that any civilisation which could evolve to a 'post-human' stage would almost certainly learn to run simulations on the scale of a universe. And that given the size of reality - billions of worlds, around billions of suns - it is fairly likely that if this is possible, it has already happened.
Digital Natives - Matthew Plummer-Fernandez. Digital Natives 2012 z-corp powder composite and z-corp tinted binder Everyday items such as toys and a watering can are 3D scanned using a digital camera and subjected to algorithms that distort, abstract and taint them into new primordial vessel forms.
Voyage au cœur des smartphones et des applications mobiles avec la CNIL et Inria. Beaucoup plus qu'un simple téléphone, le smartphone est un compagnon de tous les instants et un véritable ordinateur de poche pour gérer le quotidien, s'informer, se divertir.

Speedtest.net - Le test de bande passante de référence mondiale. Physicists Use Cloud of Rubidium Atoms as Optical Memory Device. To View a brief animation (click link to launch mp4).
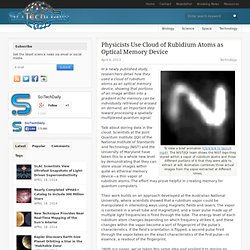
The NIST/JQI team shows the NIST logo they stored within a vapor of rubidium atoms and three different portions of it that they were able to extract at will. Animation combines three actual images from the vapor extracted at different times. In a newly published study, researchers detail how they used a cloud of rubidium atoms as an optical memory device, showing that portions of an image written into a gradient echo memory can be individually retrieved or erased on demand, an important step toward processing a spatially multiplexed quantum signal. Talk about storing data in the cloud.
Scientists at the Joint Quantum Institute (JQI) of the National Institute of Standards and Technology (NIST) and the University of Maryland have taken this to a whole new level by demonstrating that they can store visual images within quite an ethereal memory device—a thin vapor of rubidium atoms. Publication: J.B. Lego Antikythera Mechanism. Controlling the Spin Polarization of Electrons in Three Dimensions. The interior bulk of a topological insulator is indeed an insulator, but electrons (spheres) move swiftly on the surface as if through a metal.
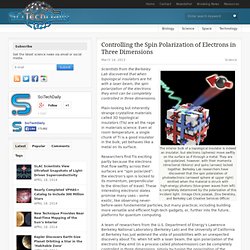
They are spin-polarized, however, with their momenta (directional ribbons) and spins (arrows) locked together. Berkeley Lab researchers have discovered that the spin polarization of photoelectrons (arrowed sphere at upper right) emitted when the material is struck with high-energy photons (blue-green waves from left) is completely determined by the polarization of this incident light. (Image Chris Jozwiak, Zina Deretsky, and Berkeley Lab Creative Services Office) Scientists from the Berkeley Lab discovered that when topological insulators are hit with a laser beam, the spin polarization of the electrons they emit can be completely controlled in three dimensions. Observing Atomic Collapse Resonances in Artificial Nuclei on Graphene.
Getters, Setters, and Constructors - IS2216 - JAVA WIKI. Private Attributes In the last example we created a student class which had attributes studentNumber, studentFirstName, and studentLastName.
We changed the value of those attributes from the main method by accessing them directly using code "myStudent.studentNumber = 108234234". While this works fine for our simple example, it is bad practice to write code in this way. If we allow programmers to directly modify our attributes, then they could change our attributes to invalid values. Wiki: Tutorial Directory. You can find more about this page in LuaTutorial.

It is suggested you read the topics from top to bottom, as they increase in complexity, except when one topic depends on another. TutorialExamples explains how the examples have been created and you can follow them. The tutorial is written for the previous version of Lua, version 5.2, and the previous version, 5.1. It still is largely relevant. The Pirates Who Print Shoes - Modern Nerd.
Care to download and print your next pair of shoes? Without even paying for them? The Pirate Bay invite you to share their vision: a world in which footwear is stolen and printable. They’ve announced a new category called “physibles” — files describing physical objects that can be made with a 3D printer. In their imagined future you do not buy the objects you desire.
You download the files and print them. Cory Doctorow’s craphound.com » Novels. Homeland A few years later, California's economy collapses, but Marcus’s hacktivist past lands him a job as webmaster for a crusading politician who promises reform. Thunderbolt Labs: Machine Learning on the Cheap and Easy. For those not in the know, Weka is the excellent data-mining toolkit made available by the nice folks at the University of Waikato. Weka provides a few features that are worth evaluating for your next datamining/machine learning project: Datamining workbench with strong visualization tools and data manipulation.Machine learning experiment environment – a great way to compare different ML algorithms for performance.Knowledge Flow Environment - datamining workflow engine. Free Software Creator Speaks Out Against SOPA 1/2. Kepler: Overview. Quad Copter Demonstration - Tokyo Hackerspace. Why computers have two zeros: +0 and -0.
Setting an Application's Entry Point (The Java™ Tutorials > Deployment > Packaging Programs in JAR Files) If you have an application bundled in a JAR file, you need some way to indicate which class within the JAR file is your application's entry point. You provide this information with the Main-Class header in the manifest, which has the general form: The value classname is the name of the class that is your application's entry point. Recall that the entry point is a class having a method with signature public static void main(String[] args).
After you have set the Main-Class header in the manifest, you then run the JAR file using the following form of the java command: Learn You a Haskell for Great Good! - Chapters.
Security. Electronics. Robots to take care of prisons in South Korea. It looks like South Korea is really keen on replacing the country’s workers with robotic counterparts. Earlier this year it was reported that cinema ticket sales would be handled by some robots in the country, and now it looks like robots will be taking over the jobs of prison guards in the future. Some new robots that have been developed in cooperation with the country’s justice ministry will be introduced to the prison in Pohang, southeast of Seoul in March next year. If the trial goes well, we’ll see more robots introduced in the future.
Over a billion won ($850,000) was spent on development of the robotic prison guards which are supposed to enable human counterparts to focus more on rehabilitation work with offenders. The robots which will be used mainly at night will patrol the prison, looking for suspicious behavior among prisoners. Bullet Physics. Best Lifehacks for Designers, Developers & Photographers. Neo4j: NOSQL For the Enterprise. Need a graph database like Twitter is built on? @neo4j delivers, @emileifrem tells why. Epic Mode // Think Like (a) Git. 10 code snippets to interact with Twitter.
Artificial Intelligence. Le Robot Atlas de Boston Dynamics. Unified Modeling Language. The Unified Modeling Language (UML) is a general-purpose modeling language in the field of software engineering, which is designed to provide a standard way to visualize the design of a system.[1] Mixin. Combinatorics.
Informatics (academic field) Informatics is - in a general sense - the science of information. As an academic field it involves the practice of information processing, and the engineering of information systems. It studies the structure, algorithms, behaviour, and interactions of natural and artificial systems which store, process, access, and communicate information. The field considers the interaction between humans and information systems alongside the construction of computer interfaces. Currying. Lambda calculus. Ergodic theory. Signs that you're a bad programmer - Software Engineering Tips. You're a Bad Programmer. Embrace It. Padovan sequence. Bezier curves - a primer. LPI Linux Certification. Software. Developer.
Algorithms. Augmented Video: Next Generation Filmmaking.