

Australian metadata laws put confidential interviews at risk, with no protections for research. Each year, academics and students make countless applications for research ethics approval, based on the promise of confidentiality to their interview subjects.
Interviewees sometimes offer academic researchers information that might be self-incriminating or might jeopardise the rights and liberties of others they’re discussing. But Australia’s metadata retention laws can lead to the identification and even incrimination of the very people whose identities academic researchers have promised to keep secret for their work. Read more: Think your metadata is only visible to national security agencies? Think again Imagine, for instance, a criminologist conducting a project examining white collar crime in banking and financial services. Under the metadata laws, government agencies make hundreds of thousands of requests to Australian telcos each year for their customers’ phone and internet communications metadata.
Interviews about a range of sensitive research topics may be at risk. Think your metadata is only visible to national security agencies? Think again. It was bound to happen, and it did.
Poorly crafted legislation – designed to allow national security agencies to collect information with the aim of protecting Australians from terrorists – is now reportedly being exploited by a range of different government agencies for other purposes. It has been widely reported that the Veterinary Surgeons Board of WA, Victorian Fisheries, Liverpool City Council, and the Australian Sports Anti-Doping Authority are among the entities that have requested access to metadata. Read more: Benign and powerful: the contradictory language of metadata retention Under the Telecommunications (Interception and Access) Act 1979, only agencies tasked with enforcing criminal law are entitled to access metadata from telecommunications companies. Metadata is the information recorded by the telco when you make a call or use the internet.
Under the legislation there are 22 criminal law enforcement agencies that can legally access these metadata. Is it possible to circumvent metadata retention and retain your privacy? There has been quite a lot discussion lately on how to avoid metadata retention, particularly in the context of leaking sensitive information to journalists.
Notable examples have come from journalist Laura Tingle and, rather surprisingly, Malcolm Turnbull, who gave the impression that avoiding metadata collection was trivially easy. Is metadata retention really that easy to avoid? If so, what is the point of the legislation? Has parliament just passed a bill for a A$400 million white elephant? Why I told my friends to stop using WhatsApp and Telegram. This morning I told my friends to stop using WhatsApp and sent them an invitation to switch to the Signal messaging app.
Here’s why. Encryption Protocols: The Signal Protocol VS Telegram’s MTProto You may not realize it, but you’re probably already using the Signal Protocol — along with more than 1 billion people every day. The Signal Protocol is used by WhatsApp, Facebook Messenger, Google Allo and Signal’s own messaging app. DNS leak test. Can You Trust Cheap Chinese Phones with Your Privacy? Should you trust a low-priced Android phone from a brand you've never heard of with your security and privacy?
It might not be such a wise idea. Illustration: Tom's Guide The fact is that many low-priced Android smartphones have had security and privacy problems. In late July, Russian antivirus firm Dr.Web reported that models sold under the Leagoo and Nomu names had a malicious program built right into the firmware. Error loading player: No playable sources found Then, just last week, Amazon suspended sales of phones marketed by BLU after researchers reported that snooping adware was built into the devices.
"If you buy a cheap Android phone, you're playing a dangerous game of Russian roulette with your privacy and security. " — Graham Cluley, security threat researcher and blogger. Text & GPS on your phone, even without service. Turtl: A secure, encrypted Evernote alternative. A Map in iPhone Privacy Settings Tracks Your Location - How to Turn Off Location Services - Thrillist. Rows.io Jabber/XMPP Server. The iCepa Project. Jitsi.org.
Online Visual Traceroute. Map Data Map data ©2017 Google, INEGI Map Satellite Visual traceroute may have misplaced routers.
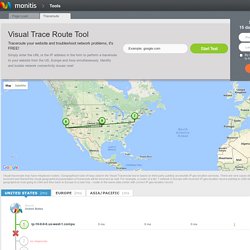
Geographical route of hops used in the Visual Traceroute tool is based on third-party publicly accessible IP geo-location services. Free Network Trace Test Are you having network problems? Monitis visual traceroute is a free diagnostic tool that displays the path the Internet packets take across IP networks to reach a specific destination on a network. You will get a report identifying the approximate geophysical location of each hop and visualizing the route on Google maps. Perform a tracert test from around the world right from your browser Diagnose network connectivity problems Identify routers that are experiencing high latencies Get the most out of your Monitis experience. The Truth Is Coming And It Cannot Be Stopped. Shortly after Edward Snowden went public with his findings on the NSA’s surveillance program, he uttered some very powerful words: “All I can say right now is the US Government is not going to be able to cover this up by jailing or murdering me.
Truth is coming, and it cannot be stopped.” Truth is coming, and it cannot be stopped. Exciting words for most of the general population, but troubling for a select few in Washington, New York, London and Brussels. What he is describing, believe it or not, is the true definition of “Apocalypse” – The “Lifting of the Veil”, when all truths become known and public… Hidden information revealed, including, that pertaining to the purposeful use and abuse of the common people of earth.
From Snowden’s testimony, he covertly said from the very beginning that there was and is an end-game in play. In other words, there are white hats (good guys) within “the matrix” aimed at taking down the banking/political cabalists. Mailvelope. VeraCrypt - Home. IOS Crypto Disks - Store Private and Secret Files/Documents/Photos/Videos in Encrypted Disks on the App Store.
Glenn Greenwald: Why privacy matters.
TPP All Chapters. Treaties and International Law - Treaties for which NZ is Depositary - Trans-Pacific Strategic Economic Partnership - NZ Ministry of Foreign Affairs and Trade. How to Deploy HTTPS Correctly. By Chris Palmer and Yan Zhu Originally published on 15 Nov 2010.
Revised on 12 Dec 2013. Internet technologists have always known that HTTP is insecure, causing many risks to users. Because HTTP traffic is unencrypted, any data sent over HTTP can be read and modified by anyone who has access to the network. As revealed by the Snowden NSA surveillance documents, HTTP traffic can also be collected and searched by government agencies without notice to users or webmasters. While HTTPS has long existed as the bare minimum for web security, some websites have been slow to adopt it. Hope privacy tricks. Alterstep/dnscrypt-osxclient. Edward Snowden: Here's how we take back the Internet. Open Wireless Movement. Open Crypto Audit Project. Why PrivacySOS.org? Hitchens - free speech. Deep Whois. CloudFlare Watch. How to delete Facebook from your life completely. Deleting Facebook: more difficult than you might think.
Photo: Mashable This post was originally published on Mashable. If you're seriously considering deleting your Facebook account, you're not alone.