

L6 dhts. What-is-fingerprinting-the-online-tracking-you-cant-avoid-20191101-p536ff. Fingerprinting happens when sites force your browser to hand over innocent-looking but largely unchanging technical information about your computer, such as the resolution of your screen, your operating system or the fonts you have installed.
Combined, those details create a picture of your device as unique as the skin on your thumb. Sites can use your digital fingerprint to know if you've visited before, create profiles of your behaviour or make ads follow you around. They can also use it to stop you from sharing a password, identify fraudsters and block harmful bots. Fingerprinting isn't yet as widespread as cookies, those tiny files websites drop in your browser to track you.
How Elliptic Curve Cryptography Works. Learn about ECC or elliptic-curve cryptography, including its applications and benefits.
My last article discussed the ingenuity of the Diffie-Hellman key exchange. This article introduces elliptic curves used in a more advanced exchange. (If you'd like a little bit more context, check out my primer on cryptography for some basic information.) Gab reports Apple to the US Department of Justice as the Dissenter iOS app is rejected from the App Store - even though Apple admits it doesn't violate any terms. After reviewing the Dissenter iOS browser and finding that it doesn’t violate any of the App Store’s guidelines, Apple has rejected it because Gab’s other products outside of the App Store contain “defamatory and mean-spirited content.”
Gab says that it submitted the Dissenter iOS browser to Apple for review on May 20, 2019. Earlier today, Gab highlighted that it seems to be taking much longer than usual for the app to come out of review. Shortly after Gab posted this message, Apple rejected the Dissenter iOS browser. Apple said that the Dissenter iOS browser itself doesn’t contain any content that violates its App Store guidelines. The Pentagon has a laser that can identify people from a distance—by their heartbeat. Everyone’s heart is different.

Like the iris or fingerprint, our unique cardiac signature can be used as a way to tell us apart. Crucially, it can be done from a distance. Are our phones listening to us? How my sexual health searches ended up in the hands of the world's biggest tech companies. Updated 7 minutes agoFri 23 Nov 2018, 12:22am When I searched through the vast amount of data my phone and laptop shared in a week, there was one thing that really weirded me out: how my health information was being unexpectedly sent to multiple companies.
And it wasn't just search engines sharing my health-related web browsing — I even found a Victorian Government website delivering data directly to two of the world's biggest tech companies. Fresh Approach to WiFi Cracking Uses Packet-Sniffing. Researchers Break IPsec VPN Connections with 20-Year-Old Protocol Flaw. KRACK Attacks: Breaking WPA2. The BitTorrent Engineering Blog. Librem 5 – A Security and Privacy Focused Phone – Purism. Freedom of Choice We believe phones should not track you nor exploit your digital life.
We are in the middle of a digital rights revolution where you get to decide the future. We at Purism are building a phone that does not run Android nor iOS, but runs PureOS or any GNU/Linux distribution where all the source code is available. Note that the visual design of the phone is a work in progress and is subject to evolve based on technical requirements and people’s feedback. Peace of Mind Our phone will not wholesale gather your data for profit. Does Not Track You Our phone will be built to protect you by default. High Quality We know how to build products that are convenient, privacy and security focused. Purism has built and delivered laptops successfully for over 2 years and is now ready to begin development on a phone product. We are focusing on creating a secure communication device, and will continually expand the product through software with community and developer support.
Traffic – Tor Metrics. Privacy - PGP Messenger. WTF is The Blockchain? – Hacker Noon. Keybase. Slashdot. The Guardian has released new documents from Edward Snowden showing how the U.S.
National Security Agency targets internet anonymity tool Tor to gather intelligence. DHT Protocol. Syncthing. MaidSafe - The New Decentralized Internet. BlackHat USA 2011: SSL And The Future Of Authenticity. Alternative Internet. Jewel/clearskies. Wiki. Anonymous VPN Providers? 2016 Edition (Page 2) ~ TorrentFreak. You can read the introduction (page 1) here. 1.
Do you keep ANY logs which would allow you to match an IP-address and a time stamp to a user of your service? If so, what information and for how long? HelloZeroNet/ZeroMail: End-to-end encrypted, P2P messaging site. DHT Protocol. Public-key cryptography. An unpredictable (typically large and random) number is used to begin generation of an acceptable pair of keys suitable for use by an asymmetric key algorithm.
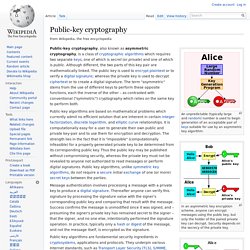
In an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of the private key. In the Diffie–Hellman key exchange scheme, each party generates a public/private key pair and distributes the public key. VeraCrypt - Home. Enabling Communications, Anywhere, Anytime: Arduino Yun as a possible Mesh Extender Platform. Regular readers of this blog will know that we have been looking at a variety of hardware options for the Serval Mesh Extender.
The Serval Mesh Extender is a device that combines ad-hoc WiFi meshing with long-range license-free UHF packet radio to allow the easy formation of mesh networks spanning useful distances. Typically the UHF packet radio has a range about ten times greater than WiFi. This means that in ordinary suburban and urban areas we get a range of a block or two, and in open rural areas the range can be in the kilometres. We run our award winning Serval Mesh software over the top, providing an easy to use communications system that lets you use your cell phone without cellular coverage, for example, during a disaster, or when you and your friends are near one another outside of the range of your native network.
Voluntary - Bitpost. Bitpost private decentralized messaging Source. Open Wireless Movement. iMessage Privacy. iMessage is probably one of the most trendy instant messaging systems. Apple presents it as very secure, with high cryptographic standards, including end-to-end encryption preventing even Apple from reading the messages. Is this true? Apple iMessage Open to Man in the Middle, Spoofing Attacks. P2P microblogging platform. Welcome to CAcert.org. Bitcloud. OpenBitTorrent - An open tracker project. P2PVPN - Home.
Multipeer Connectivity. As consumer web technologies and enterprises race towards cloud infrastructure, there is a curious and significant counter-movement towards connected devices. In this age of mobile computing, the possibilities of collaboration, whether in work or play, have never been greater. In this age of privacy concerns and mass surveillance, the need for secure, ad hoc communications has never been more prescient. In this age of connected devices, the promise of mastery over the everyday objects of our lives has never been closer at hand. The Multipeer Connectivity APIs, introduced in iOS 7, therefore may well be the most significant for the platform. It allows developers to completely reimagine how mobile apps are built, and to redefine what is possible. Multipeer Connectivity is a framework that enables nearby devices to communicate over infrastructure Wi-Fi networks, peer-to-peer Wi-Fi, and Bluetooth personal area networks.