

Converting HEX string to ascii string. Originally Posted by tchadwick71I saw your example converting hex to ascii "=CHAR(HEX2DEC("4A"))".
I would like to know how to convert a string of hex to ascii. The worst volume control UI in the world. Tacotron 2: Generating Human-like Speech from Text. Posted by Jonathan Shen and Ruoming Pang, Software Engineers, on behalf of the Google Brain and Machine Perception Teams Generating very natural sounding speech from text (text-to-speech, TTS) has been a research goal for decades.
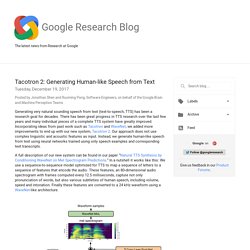
There has been great progress in TTS research over the last few years and many individual pieces of a complete TTS system have greatly improved. Incorporating ideas from past work such as Tacotron and WaveNet, we added more improvements to end up with our new system, Tacotron 2. Keycloak. Docker in Production: An History of Failure – The HFT Guy. My first encounter with docker goes back to early 2015.
Docker was experimented with to find out whether it could benefit us. At the time it wasn’t possible to run a container [in the background] and there wasn’t any command to see what was running, debug or ssh into the container. The experiment was quick, Docker was useless and closer to an alpha prototype than a release. Fast forward to 2016. New job, new company and docker hype is growing like mad. We have 12 dockerized applications running in production as we write this article, spread over 31 hosts on AWS (1 docker app per host).
The following article narrates our journey with Docker, an adventure full of dangers and unexpected turns. Noto Fonts. When text is rendered by a computer, sometimes characters are displayed as “tofu”.
They are little boxes to indicate your device doesn’t have a font to display the text. Google has been developing a font family called Noto, which aims to support all languages with a harmonious look and feel. Noto is Google’s answer to tofu. Chroma.js Color Scale Helper. Ebde50. Click to copy colllor about share Free graph / lined / dot paper generator.
Massivedynamic/openftp4: A list of all FTP servers in IPv4 that allow anonymous logins. Oh, shit, git! ColorBrewer: Color Advice for Maps. GitHub - blackthorne/Codetective: a tool to determine the crypto/encoding algorithm used according to traces from its representation. Text to Decimal — Cryptii. Alphabet.

Fuck Off As A Service (FOAAS) GitHub - json-porn-api/demo: Demo client for the JSON Porn API. Instant Logo Search. Scott Hanselman's 2014 Ultimate Developer and Power Users Tool List for Windows. Agréger plusieurs connexions ADSL grâce à OverTheBox. Alors là, je dis bravo OVH, c'est du bon boulot !
Waifu2x. AlessandroZ/LaZagne. Motherfucking Website. Une IA de Google décrit avec précision le contenu de photos ! Jusqu'à présent, on connaissait les outils de reconnaissance faciale qui permettent de repérer et d'identifier les visages apparaissant sur une photo.
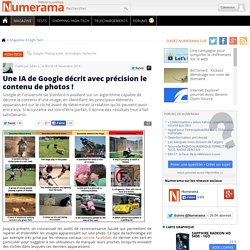
Ce type de technologie est par exemple très prisé par les réseaux sociaux comme Facebook. Ce dernier s'en sert en particulier pour suggérer à ses utilisateurs de marquer leurs proches lorsqu'ils envoient des clichés dans lesquels ces derniers apparaissent. Mais il y a beaucoup plus impressionnant : ce sont les outils qui sont capables d'analyser le contenu d'une photographie et d'en faire une description très fidèle. Et justement, Google est sur le coup - en partenariat avec l'université de Stanford - avec une solution qui est non seulement capable de détecter les éléments d'un cliché, mais aussi de déterminer les relations qu'ils ont entre eux. Le résultat est saisissant. Dans le détail, le système essaie d'associer des images à des phrases. UnlawfulPaleGnat. How I reverse-engineered Google Docs to play back any document's keystrokes « James Somers (jsomers.net) If you’ve ever typed anything into a Google Doc, you can now play it back as if it were a movie — like traveling through time to look over your own shoulder as you write.

This is possible because every document written in Google Docs since about May 2010 has a revision history that tracks every change, by every user, with timestamps accurate to the microsecond; these histories are available to anyone with “Edit” permissions; and I have written a piece of software that can find, decode, and rebuild the history for any given document. See that little gizmo above? It’s like a video player, but made especially for writing. Un gros Troll de plus sur Javascript.
Emoji unicode characters for use on the web. Apps.timwhitlock.info Emoji Unicode Tables The following tables show commonly-supported Emoji that map to standardized Unicode characters.
Reset The Net - Privacy Pack. How to fix limited or no connectivity Wi-Fi issues in Windows 8. What happens when Windows 8 or 8.1 shows the following arcane message whenever you try to connect to your wireless network: This connection has limited or no connectivity. No internet access Or maybe you’ve seen this laconic message: The connection is limited So brief. So rude. Computrace - Le mouchard universel présent sur les PC, Mac et appareils Android. Et si je vous disais qu'il y a dans votre ordinateur un mouchard que vous ne pouvez pas enlever, qui a été mis en place par le constructeur, qui est sur les listes blanches de la plupart des antivirus et dont vous n'avez jamais entendu parler ?
La société Kaspersky, spécialisée dans la détection et l'élimination de malware a débusqué il y a quelques mois un logiciel installé sur plus de 2 millions d'ordinateurs de par le monde qui est commercialisé par la société Absolute et qui permet OFFICIELLEMENT : Online graphing calculator and function plotter. RegExr: Learn, Build, & Test RegEx. Heartbleed Bug. Test your server for Heartbleed (CVE-2014-0160) If there are problems, head to the FAQ Results are now cached globally for up to 6 hours. Enter a URL or a hostname to test the server for CVE-2014-0160.
All good, seems fixed or unaffected! Uh-oh, something went wrong: Check what it means at the FAQ. It might mean that the server is safe, we just can't be 100% sure! Here is some data we pulled from the server memory: (we put YELLOW SUBMARINE there, and it should not have come back) Critical crypto bug in OpenSSL opens two-thirds of the Web to eavesdropping. For a more detailed analysis of this catastrophic bug, see this update, which went live about 18 hours after Ars published this initial post. Researchers have discovered an extremely critical defect in the cryptographic software library an estimated two-thirds of Web servers use to identify themselves to end users and prevent the eavesdropping of passwords, banking credentials, and other sensitive data.
The warning about the bug in OpenSSL coincided with the release of version 1.0.1g of the open-source program, which is the default cryptographic library used in the Apache and nginx Web server applications, as well as a wide variety of operating systems and e-mail and instant-messaging clients. Svn cleanup failed–previous operation has not finished; run cleanup if it was interrupted. August 1, 2013 Anuj Varma svn cleanup failed–previous operation has not finished; run cleanup if it was interrupted All content on this site is original and owned by anujvarma.com. Specializing in high volume web applications, Anuj Varma has helped architect, re-architect and troubleshoot some of the largest web applications out there.
His customer base includes Fortune 100 companies ( British Petroleum, dell.com, Schlumberger) as well as smaller to mid size firms within the United States. Spreadsheet Service - Google Apps Script. CodeCombat. Historique des positions Google. How the Bible and YouTube are fueling the next frontier of password cracking. Early last year, password security researcher Kevin Young was hitting a brick wall. Daily learnings. Minecrafting with OS OpenData. We have created GB Minecraft 2, a Minecraft® world made with digital map products – freely available as OS OpenData™. The world consists of more than 83 billion blocks representing over 220,000 square kilometres of mainland Great Britain and surrounding islands. We don't include Northern Ireland, the Channel Islands or the Isle of Man because they are mapped by other organisations.
Take a look at our Developer Centre for lots more information on the data, tools and other resources we offer. Gaupol Subtitle Editor. Gaupol is an editor for text-based subtitle files. It supports multiple subtitle file formats and provides means of creating subtitles, editing texts and timing subtitles to match video. The user interface is designed with attention to batch processing of multiple documents and convenience of translating. Gaupol should run on all Unix-like (GNU/Linux, *BSD, Solaris, etc.) operating systems and on Windows. The beginners guide to breaking website security with nothing more than a Pineapple. Bayesian Methods for Hackers. An intro to Bayesian methods and probabilistic programming from a computation/understanding-first, mathematics-second point of view. Prologue The Bayesian method is the natural approach to inference, yet it is hidden from readers behind chapters of slow, mathematical analysis.
The typical text on Bayesian inference involves two to three chapters on probability theory, then enters what Bayesian inference is. Unfortunately, due to mathematical intractability of most Bayesian models, the reader is only shown simple, artificial examples. New AWS Command Line Interface (CLI) Graphical user interfaces (e.g. the AWS Management Console) are great, but nothing beats the expressiveness of the command line! Why I Dislike EC2. Open Source Game Clones.
Practical, Visual, Three-Dimensional Pedagogy for Internet Protocol Packet Header Control Fields. Practical, Visual, Three-Dimensional Pedagogy for Internet Protocol Packet Header Control Fields June 27, 2010 Hal Pomeranz, Deer Run Associates. Solved Windows 8 Wifi Help. YouTube Options - a browser extension. Buffer speed, size and video size on YouTube.
Layervault/psd.rb. 10 Easy Steps to a Complete Understanding of SQL. Learn Go in Y Minutes.