

12 Useful Commands For Filtering Text for Effective File Operations in Linux. 23.2. FreeBSD Update. Written by Tom Rhodes.

Based on notes provided by Colin Percival. Applying security patches in a timely manner and upgrading to a newer release of an operating system are important aspects of ongoing system administration. FreeBSD includes a utility called freebsd-update which can be used to perform both these tasks. This utility supports binary security and errata updates to FreeBSD, without the need to manually compile and install the patch or a new kernel.
Binary updates are available for all architectures and releases currently supported by the security team. This utility also supports operating system upgrades to minor point releases as well as upgrades to another release branch. Note: If a crontab utilizing the features of freebsd-update(8) exists, it must be disabled before upgrading the operating system. Rclone sync. Click For Information: How To Use Files And File System Security In Linux. A few minutes of preparation and planning ahead before putting your systems on-line can help to protect them and the data stored on them.
Umask Settings The umask command can be used to determine the default file creation mode on your system. It is the octal complement of the desired file mode. If files are created without any regard to their permissions settings, the user could inadvertently give read or write permission to someone that should not have this permission. Typical umask settings include 022, 027, and 077 (which is the most restrictive).
File Permissions. Vimqrc. For educational purposes. How to disable IPv6 on Linux. IPv6 offers a much larger addressing scheme than IPv4, which is one of the many reasons why it was developed.
However, I have seen rare instances in which IPv6 has caused network problems. Since some hardware doesn't take advantage of IPv6 (and most admins are still working with IPv4), a temporary and easy solution is to disable IPv6; the protocol can be re-enabled when the time comes when the issue has been permanently resolved. SEE: IPv6: The smart person's guide If you have hardware that perfectly implements IPv6 and software that uses it correctly, this is a non-issue. But if you're having networking issues with Linux servers or desktops, and you've exhausted all possible areas, you might try disabling v6 of the network protocol. A freeware download site with no ads. Nada . Zip. Zero. Not gonna make us rich but it does make us feel all warm and fuzzy.
Dependencies - How can apt-get deal with dependency problems associated with a slightly problematic package? 6 Best Linux/Unix Command Cheat Sheet. Linux has become so user-friendly nowadays that there is less and less need to use the command line.
However, the commands and shell scripts remained powerful for advanced users to be able to do more complicated tasks quickly and efficiently. With the vast number of commands available, you have to know loads of commands and how to effectively use them. But there is really no need to memorize everything since there are many cheat sheets available on the internet and books. Free Cloud Services – AWS Free Tier. * These free tier offers are only available to new AWS customers, and are available for 12 months following your AWS sign-up date.
When your 12 month free usage term expires or if your application use exceeds the tiers, you simply pay standard, pay-as-you-go service rates (see each service page for full pricing details). Restrictions apply; see offer terms for more details. ** These free tier offers do not automatically expire at the end of your 12 month AWS Free Tier term, but are available to both existing and new AWS customers indefinitely. † The following Windows variants are not eligible for the free tier: Microsoft Windows Server 2008 R2 with SQL Server Web, Microsoft Windows Server 2008 R2 with SQL Server Standard, Microsoft Windows 2008 R2 64-bit for Cluster Instances and Microsoft Windows 2008 R2 SQL Server 64-bit for Cluster Instances.
4 Easy Ways To Generate A Strong Password In Linux - OSTechNix. Yesterday, We have covered how to force users to use a strong password in DEB based systems such as Debian, Ubuntu, Linux Mint, Elementary OS etc.
You might wonder how a strong password looks like, and how could I create one? No worries! Ten command line time-savers for Linux administrators. Although the Linux desktop has been subject to enormous improvements over the past twenty years (with perhaps the most notable change coming by way of the Ubuntu Unity interface), the command line remains unparalleled in terms of the power it can offer an experienced system administrator.
Although most of the following 10 tips focus on the Bash shell, all of these tips will be easily applicable to other modern shells. 1. Create and enter a directory using one command Creating and subsequently entering a new directory is such a common task it seems that there should be a shortcut for executing both commands in the shell. While it’s not, you can add the following function to your .bashrc file: mkcd() { mkdir $1 cd $1 } Then run source .bashrc to read the changes into memory, and complete both tasks using the mkcd command: wjgilmore@ubuntu:~$ mkcd articles wjgilmore@ubuntu:~/articles $
What are some lesser known but useful Unix commands? - Quora. Untitled. A public and private key each have a specific role when encrypting and decrypting documents. A public key may be thought of as an open safe. When a correspondent encrypts a document using a public key, that document is put in the safe, the safe shut, and the combination lock spun several times. The corresponding private key is the combination that can reopen the safe and retrieve the document. In other words, only the person who holds the private key can recover a document encrypted using the associated public key. The procedure for encrypting and decrypting documents is straightforward with this mental model.
To encrypt a document the option --encrypt is used. 15 Things to do after Ubuntu 16.04 Installation - JoinTux. Viber Desktop. VPN Forever: Lifetime Subscription. POP server settings for Yahoo Mail. POP lets you connect your Yahoo Mail account to a desktop mail client or mobile app.
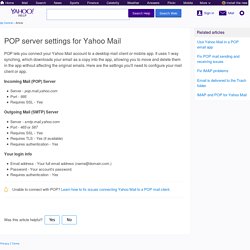
It uses 1-way synching, which downloads your email as a copy into the app, allowing you to move and delete them in the app without affecting the original emails. Here are the settings you'll need to configure your mail client or app. Incoming Mail (POP) Server Server - pop.mail.yahoo.com Port - 995 Requires SSL - Yes Outgoing Mail (SMTP) Server. How to Use Awk and Regular Expressions to Filter Text or String in Files. When we run certain commands in Unix/Linux to read or edit text from a string or file, we most times try to filter output to a given section of interest.
This is where using regular expressions comes in handy. Read Also: 10 Useful Linux Chaining Operators with Practical Examples What are Regular Expressions? How to Use Awk and Regular Expressions to Filter Text or String in Files. Linux cheat sheet. Quora - The best answer to any question. Configuring Your Linux for Development With Zsh, Tmux, and Vim. Codementor Luke Murphy is a software engineer by trade.
He spent most of his professional career working with the Python programming language, and likes to write programs in Haskell and Clojure. Moving around. You can save a lot of time when navigating through text by using appropriate movement commands. In most cases the cursor keys are not the best choice. Here are some basic movement commands that may help you acquire a taste for more: e. How to...favorite & forget. Just because I like you guys. BASH Programming - Introduction HOW-TO. Next Previous Contents BASH Programming - Introduction HOW-TO by Mike G mikkey at dynamo.com.ar Thu Jul 27 09:36:18 ART 2000. Bash scripting Tutorial.
Hello World Bash Shell Script Attention: For more verbose and beginner style Bash scripting tutorial visit our Bash Scripting Tutorial for Beginners. Bash Scripting Tutorial - Ryans Tutorials. Welcome! How can I list directories only in linux? Software.opensuse.org: TIL my office skills could use some improvement. OSNews is Exploring the Future of Computing. Linux News On Internet Time. DistroWatch.com: Put the fun back into computing. Use Linux, BSD.