


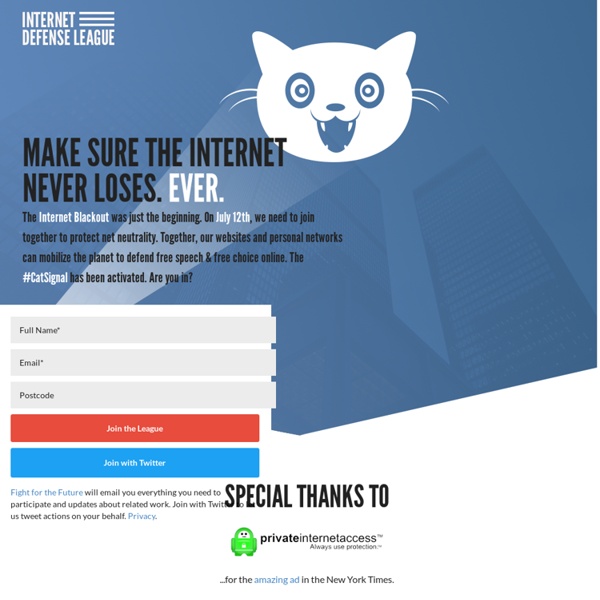
https://www.internetdefenseleague.org/
8,200+ Strong, Researchers Band Together To Force Science Journals To Open Access Evolutionary biologist Michael Eisen made this t-shirt design in support of the Elsevier boycott. Academic research is behind bars and an online boycott by 8,209 researchers (and counting) is seeking to set it free…well, more free than it has been. The boycott targets Elsevier, the publisher of popular journals like Cell and The Lancet, for its aggressive business practices, but opposition was electrified by Elsevier’s backing of a Congressional bill titled the Research Works Act (RWA). Though lesser known than the other high-profile, privacy-related bills SOPA and PIPA, the act was slated to reverse the Open Access Policy enacted by the National Institutes of Health (NIH) in 2008 that granted the public free access to any article derived from NIH-funded research. But the fight for open access is just getting started. Seem dramatic?
Image Join Now! Share Share on redditShare on facebookShare on twitterShare on tumblrMore Sharing Services0 ABOUT FORAUS – Foraus Independent. Scientific. Relevant. When is the social curation bubble going to burst? You just can’t move for social curation services right now. The biggest noise might be coming from Pinterest, which is growing like a weed — but whether it’s the new-look Delicious, Switzerland’s Paperli, shopping curation site Svpply, image service Mlkshk or another site, the fact is that almost everybody seems to want to help you save and sort and share the things you find on the web right now. With this swirl of activity, then, it’s no surprise to hear that Parisian service Pearltrees — slogan “collect, organize, discover” — has just raised another $6 million of funding, led by local conglomerate Groupe Accueil. The company, which has been running in public since 2009, welcomed the injection of funds as a way to help expand and scale up its system for bookmarking and organizing, which is based around a clustered visual interface. And it needs that scale.
Full text of "Guerilla Open Access Manifesto" Guerilla Open Access Manifesto Information is power. But like all power, there are those who want to keep it for themselves. The world's entire scientific and cultural heritage, published over centuries in books and journals, is increasingly being digitized and locked up by a handful of private corporations. Want to read the papers featuring the most famous results of the sciences?
Image Join Now! Share Share on redditShare on facebookShare on twitterShare on tumblrMore Sharing Services0 The Conversation: In-depth analysis, research, news and ideas from leading academics and researchers. Efforts to regulate the lucrative mining venture are not proving successful due to collusion and corruption. Megaproject construction has been a major response to globalization in the urban realm. Whether successful or not – and most impeachments are not – the fallout for the Democrats and the US will be deep and enduring. Creative thinking needs to go into implementing copyright in countries like Liberia.
Call to Action: Reclaim Pride From the 1% #OccuPride #OccuPride #OccuQueers #Tranarchism #PinkBlocGlobal Facebook eventMany more events are listed below the call to action!If your organization would like to endorse the call to action, or if you have events to add, please e-mail lgbtq@occupywallst.org. Pride 2012: The Struggle for Sexual and Gender Justice Continues This summer, communities across the world will celebrate Pride Festivals commemorating the birth and victories of the Gay and Trans Liberation Movements. Net Neutrality 101 When we log onto the Internet, we take lots of things for granted. We assume that we'll be able to access whatever Web site we want, whenever we want to go there. We assume that we can use any feature we like -- watching online video, listening to podcasts, searching, e-mailing and instant messaging -- anytime we choose. We assume that we can attach devices like wireless routers, game controllers or extra hard drives to make our online experience better. What makes all these assumptions possible is "Network Neutrality," the guiding principle that preserves the free and open Internet. Net Neutrality means that Internet service providers may not discriminate between different kinds of content and applications online.
Blog Archive Next Japanese nuclear accident will be even worse This is my sixth column about the Fukushima Daiichi nuclear accident that started last year in Japan following the tsunami. But unlike those previous columns (1,2,3,4,5), this one looks forward to the next Japanese nuclear accident, which will probably take place at the same location. That accident, involving nuclear fuel rods, is virtually inevitable, most likely preventable, and the fact that it won’t be prevented comes down solely to Japanese government and Tokyo Electric Power Company (TEPCO) incompetence and stupidity. Japanese citizens will probably die unnecessarily because the way things are done at the top in Japan is completely screwed up.
How I Published My Scholarly Book With an Open Access CC-BY License [Open Access Week in 2014 is October 20-26.] Have you noticed that scholarly books are getting more and more expensive? It’s not just the journals that are exorbitantly priced. Yesterday I didn’t buy a really interesting anthology in my field because it cost over $100. More and more of the monographs I’m interested in cost £50 or £60 or even £80. You can download Seeing Ourselves Through Technology for free.
Canadian Police Server Hacked, Lots of Personal Information Leaked By Anonymous In what has been a huge week for cyber attacks yet another police department has been hit, this time its a Canadian one and the attack has been carried out by Anonymous hackers in the name of #opQuebec. The leak has been uploaded to pastehtml with the following message and it also contains 4 links to the actual information that was leaked and was announced via twitter with the following message and image by @SunkiAnonymous. #Anonymous hack la #police #quebecoise : || #AbricotSec - #
Meet the Robin Hood of Science The tale of how one researcher has made nearly every scientific paper ever published available for free to anyone, anywhere in the world. On the evening of November 9th, 1989, the Cold War came to a dramatic end with the fall of the Berlin Wall. Four years ago another wall began to crumble, a wall that arguably has as much impact on the world as the wall that divided East and West Germany. The wall in question is the network of paywalls that cuts off tens of thousands of students and researchers around the world, at institutions that can’t afford expensive journal subscriptions, from accessing scientific research. On September 5th, 2011, Alexandra Elbakyan, a researcher from Kazakhstan, created Sci-Hub, a website that bypasses journal paywalls, illegally providing access to nearly every scientific paper ever published immediately to anyone who wants it.