


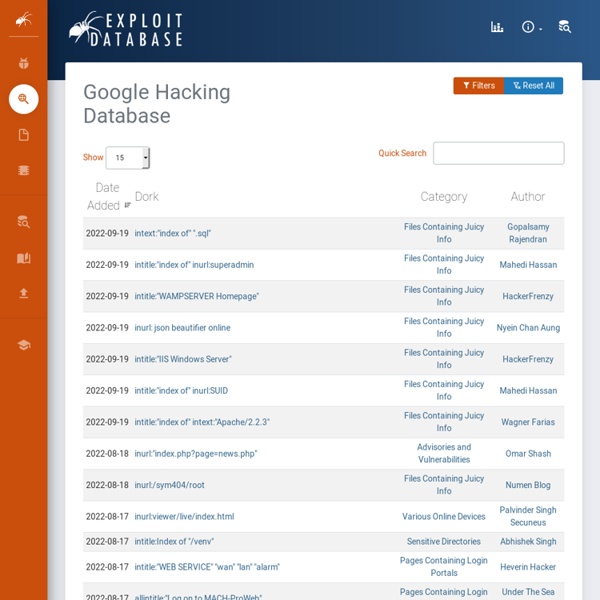
https://www.exploit-db.com/google-hacking-database/
Related: Facts/KnowledgeGoogle hacking master list This master list of Google Hacking command sets has show up on a forum in Russia, as well as on Scribd. While we often forget about Google hacking, and rarely use it against our own sites, a list like this is going to keep the kids happy as they merrily pound their way through Google to your systems. This makes the data much more accessible than at Johnny I hack stuff. There are some drawbacks in how Johnny I hack stuff works, you have to do a lot of clicking to get to the right hacks. This master list also includes things I have not seen or tried yet meaning that the body of knowledge for Google hacks is still being expanded upon. It has been a while since a really good Google hack has come out, but this list promises to keep me busy for a while.
Comprehensive Package Database Although packages are easily navigated from any jailbroken iOS device through the Cydia application itself, Cydia Search is a browser-based search engine offering a quick and reliable alternative for finding packages currently available in Cydia. Cydia Search checks all included repositories for new and updated packages once per hour. Additional information on how this system handles package data as well as asnwers to many frequently asked questions can be found on the FAQs page. How to Pick a Lock with a Bump Key The point that many people miss is that bump keys and lockpicks allow access to an area without any obvious sign of forced entry. This allows for long term theft, especially in an office or retail situation where high value items may be stored in a supposedly secure area and not be missed for some time, but where attempting to force a lock would bring immediate attention. If my wife comes home to a lock drilled off the door, she going to call the police. If an intruder uses a bump key, she could be totally unaware that someone was lurking inside.
How to Crack a Wi-Fi Network. 1.Back Track Today we’re going to run down, step-by-step, how to crack a Wi-Fi network with WEP security turned on. Dozens of tutorials on how to crack WEP are already all over the internet using this method. 7 Clever Google Tricks Worth Knowing Email Below I have compiled a list of 7 clever Google tricks that I believe everyone should be aware of. Together I think they represent the apex of the grand possibilities associated with Google search manipulation tricks and hacks.
Google bomb A Google bomb on March 31st, 2013. Despite Google's intervention, some of the first search results still refer to Bush. The terms Google bomb and Googlewashing refer to the practice of causing a web page to rank highly in search engine results for unrelated or off-topic search terms by linking heavily. In contrast, search engine optimization (SEO) is the practice of improving the search engine listings of web pages for relevant search terms. It is done for either business, political, or comedic purposes (or some combination thereof).[1] Google's search-rank algorithm ranks pages higher for a particular search phrase if enough other pages linked to it use similar anchor text (linking text such as "miserable failure").
Tic tac toe... … three in a row! Apple released iOS 4.3.3 on Wednesday, and once again the untethered jailbreak exploit that @i0n1c created for 4.3.1 still works. That makes it an unprecedented three firmwares where the same userland exploit works. We’re not exactly sure why Apple hasn’t fixed the hole yet, but we’re not complaining! Today’s PwnageTool and redsn0w incorporate @i0n1c’s port to 4.3.3 (it’s ironic that such a long-lasting untether doesn’t even have an official name!). Know the Trade – Your IT Security Information Portal CISSP/CEH/CISA/Hacker and Penetration Testing Specialist Google Hacking allintitle:Brains, Corp. camera allintitle:"index of/admin" allintitle:"index of/root" allintitle:restricted filetype:doc site:gov allintitle:restricted filetype :mail allintitle:sensitive filetype:doc allinurl:/bash_history allinurl:winnt/system32/ (get cmd.exe)
How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine. However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. 100+ Google Tricks That Will Save You Time in School – Eternal Code [via onlinecolleges.net] With classes, homework, and projects–not to mention your social life–time is truly at a premium for you, so why not latch onto the wide world that Google has to offer? From super-effective search tricks to Google hacks specifically for education to tricks and tips for using Gmail, Google Docs, and Google Calendar, these tricks will surely save you some precious time. Search Tricks
80+ Best Free Hacking Tutorials Learning to become hacker is not as easy as learning to become a software developer. I realized this when I started looking for learning resources for simple hacking people do. Even to start doing the simplest hack on own, a hacker requires to have in depth knowledge of multiple topics. Some people recommend minimum knowledge of few programming languages like C, Python, HTML with Unix operating system concepts and networking knowledge is required to start learning hacking techniques. Though knowing a lot of things is required, it is not really enough for you to be a competent and successful hacker. You must have a passion and positive attitude towards problem solving.