

GrammarViz 3.0. Time series anomaly and recurrent pattern discovery made interactive GrammarViz approach for time series pattern discovery is based on two algorithms that have linear time and space complexity: (i) Symbolic Aggregate approXimation (SAX), that discretizes the input time series into a string, and (ii) Sequitur, that induces a context-free grammar (CFG) from it.
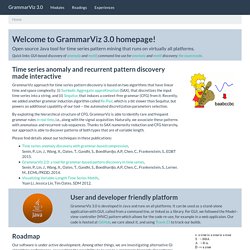
Recently, we added another grammar induction algorithm called Re-Pair, which is a bit slower than Sequitur, but powers an additional capability of our tool -- the automated discretization parameters selection. By exploiting the hierarchical structure of CFG, GrammarViz is able to identify rare and frequent grammar rules in real time, i.e., along with the signal acquisition.
Untitled. Untitled. Untitled. Previously, I demonstrated that a live forensic distribution can automatically mount file systems on suspect (internal) drives during the boot process.
Untitled. Untitled. Hi, On 8 Feb 2011, at 19:37, Phillip Susi wrote: > Is there a debugfs like tool somewhere?
I would like to manually > manipulate a test volume for debugging purposes. Ext4 - Reverse lookup of inode/file from offset in raw device on linux and ext3/4? Untitled. Untitled. This article gives details on how to find out which file owns a given disk sector.
The main purpose for doing so is finding out which file was damaged in the event a storage device develops any bad sectors (that way you will know if you lost anything important). For most of these commands you will have to be either root or a user that has direct read access to the drive you are checking (being a member of the disk group should be enough). As usual, a current backup is always a good idea, especially if imminent drive failure is suspected. S.M.A.R.T. can help determining that. Finding bad sectors.
Untitled. But what is a Fourier series? From heat flow to circle drawings. Digital Forensics and Incident Response Blog. I shall be posting a series detailing the additional data not included in the paper [1] on recovering overwritten data in the following weeks.

My thanks to Dave Kleiman (one of the original papers co-author's with myself) for reviewing and adding some details to this post series. Due to the limitations of peer reviewed papers, much of the detail of a process is commonly lost. This series of posts will endeavor to fill out the areas that are not covered in the paper in any detail and also add some further level of knowledge.
124 - Cold Boot Attack! - dump a computer's memory to a USB drive - RMPrepUSB. The Best Open Source Digital Forensic Tools – H-11 Digital Forensics. Forensic investigations are always challenging as you may gather all the information you could for the evidence and mitigation plan.
Here are some of the computer forensic investigator tools you would need. Autopsy User Documentation: Quick Start Guide. Data sources are added to a case.
A case can have a single data source or it can have multiple data sources. Currently, a single report is generated for an entire case, so if you need to report on individual data sources, then you should use one data source per case. Use PowerShell and Regular Expressions to Search Binary Data – Hey, Scripting Guy! Blog. Summary: Guest blogger and pioneer of the PowerSploit module talks about using Windows PowerShell and regular expressions to search binary data.
Microsoft Scripting Guy, Ed Wilson, is here. Today we kick off a four-part Windows PowerShell and security series with a new guest blogger, Matt Graeber. The Scripting Wife and I had the privilege of meeting Matt at the Windows PowerShell Summit earlier this year in Seattle. I was impressed with his commitment to Windows PowerShell and in the way he had been using Windows PowerShell in his security work. Note This follows along with a series of blogs that I posted earlier.
Hardware forensics. STANDS4 Web Services - Synonyms API. OSForensics - Digital investigation for a new era by PassMark Software® Showing Evidence. Untitled. How I Cracked your Windows Password (Part 2) If you would like to read the first part in this article series please go to How I Cracked your Windows Password (Part 1).
Introduction In the first part of this series we examined password hashes and the mechanisms Windows utilizes to create and store those values. We also touched upon the weaknesses of each method and possible avenues that can be used to crack those passwords. In the second and final article in this series I will actually walk you through the process of cracking passwords with different free tools and provide some tips for defending against having your password cracked.
Windows registry quick reference. Digital forensics method validation: draft guidance (second consultation) - Consultations. Users Guide · log2timeline/plaso Wiki. This page is work in progress.
How to get started First determine which version of plaso is must suitable to your needs, for more information see Releases and roadmap Installing the packaged release To install the packaged release see: SANS Computer, Digitial Forensics, Incident Response Summit Archives. Windows Forensic Analysis DVD Toolkit - Harlan Carvey. Windows Forensic Analysis. Registry Analysis (Windows Forensic Analysis) Part 7. Finding Users Information about users is maintained in the Registry, in the SAM hive file.
Under normal circumstances, this hive is not accessible, even to administrators, not without taking special steps to manually edit the access permissions on the hive. DEFT Linux - Computer Forensics live CD. The Law Society of Scotland - Directory of Expert Witnesses. Experts and expert witnesses. CRCnetBASE. Untitled. DF marking form - Excellent - A thorough investigation and a very clearly structured, written and presented report. Most significant evidence recovered - certainly enough to mount a prosecution.
" SysKey and the SAM. The Security Accounts Manager The Security Accounts Manager, or SAM, has been used by Windows since the days of NT to store information on local user accounts (or, in the case of a domain controller, the accounts for all users on the domain). It takes the form of a registry hive, and is stored in %WINDIR%\system32\config. Generally, two types of hash are stored in the SAM: the LanMan hash and the NT hash. The LanMan hash has many flaws: It is not salted, and is thus vulnerable to precomputed dictionary attacks such as rainbow tables. The NT hash, by contrast, is simply the MD4 hash of the password (encoded as UTF-16 little endian). The SAM before Windows 2000.
Partition types: List of partition identifiers for PCs. Below a list of the known partition IDs (system indicators) of the various operating systems, file systems, boot managers, etc. For the various systems, short descriptions are given, in the cases where I have some info. Sepero/SearchBin. DPATechInfo.
Rattlesnake. SQLite. Streaming media. M Gowrie's data at Radaris - The #1 information search database on the web. Search now! Forensic visualization.