

Using NSlookup.exe. The Passive Splice Network Tap - Home of Janitha Karunaratne. Wired networks are everywhere whether you like it not.
Almost every building is wired inside out, from businesses to schools to hotels. Unfortunately in most cases, little or no thought given to the physical security of the wiring. Don't take my word for it, just lift a ceiling tile in any hallway and take a peek for your self. This indirectly affect wireless networks as well, as the Access Points are still connected via a wired network. The Internet Centre - Ethernet Cable - Color Coding Diagram. The information listed here is to assist Network Administrators in the color coding of Ethernet cables.
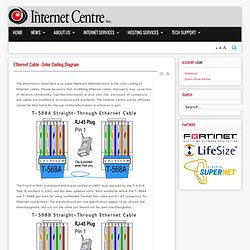
Please be aware that modifying Ethernet cables improperly may cause loss of network connectivity. T1: A Survival Guide: Chapter 5: Timing, Clocking,and Synchronization in the T-carrier System. Subnettingquestions.com - Free Subnetting Questions and Answers Randomly Generated Online. Subnets. Subnets (originated in 1985 with RFC 950) This is one of the few long, detailed explanations of subnets that you will find - so stick with it and read through it slowly.

The concept is very important !! Subnets are for LAN's only, and the Internet has no idea that subnets exist - and continues addressing the same way, with the same network address. But behind the router, the network address is broken up into 2 or more subnets. Simple Network Management Protocol (SNMP) and Traps. O Simple Network Management Protocol (SNMP) é um sistema de gerenciamento de rede baseado em protocolo.
É usado para gerenciar redes baseadas em TCP/IP e IPX. Informações sobre SNMP podem ser encontradas na RFC 1157. A Microsoft oferece um agente SNMP, ou cliente, para Windows NT e Windows 95. Simple Network Management Protocol. The effect of TCP Chimney offload on viewing network traffic - Microsoft Enterprise Networking Team. Have you ever run in to a problem where you are attempting to troubleshoot a network connectivity issue with a network capture utility and seen only the 3 way handshake?

This will happen if you are using Netmon 2.x, Netmon 3.x, Wireshark, Ethereal and most other network capture utilities. It is relatively common knowledge that this will happen when TCP Chimney offload is enabled but disabling it via the registry or netsh sometimes doesn’t always resolve the problem. TCP Chimney offload enables TCP/IP processing to be offloaded to network adapters that can handle the TCP/IP processing in hardware. The use of TCP Chimney offload causes traffic to be delivered at a lower layer of the TCP/IP stack than we listen on with most network capture utilities. The initial troubleshooting for this type of issue is to turn off TCP Chimney Offload via Netsh as follows. To turn off TCP Chimney by using the Netsh.exe tool, follow these steps: Click Start, click Run, type cmd, and then click OK. MIB Archive from plixer International. IPSec Overview Part Four: Internet Key Exchange (IKE) > IKE Overview. Internet Key Exchange (IKE) negotiates the IPSec security associations (SAs).
This process requires that the IPSec systems first authenticate themselves to each other and establish ISAKMP (IKE) shared keys. A security association (SA) is a relationship between two or more entities that describes how the entities will use security services to communicate securely. In phase 1 of this process, IKE creates an authenticated, secure channel between the two IKE peers, called the IKE security association. Network Computing. DNS Oversimplified: How to check your DNS. ... or, even a rocket scientist can understand DNS The goal of this page is to help you make sure that your DNS is set up properly, and help you many common errors that may exist.
It will also help you if you are setting up DNS for the first time -- there is a lot of valuable information in here, and after you are done, you can walk through this step-by-step to make sure you did everything properly. Just go through the following steps in order: That should cover most common errors. For a more comprehensive way to check your DNS, you may want to check out www.DNSstuff.com and www.DNSreport.com. Daryl's TCP/IP Primer. Addressing and Subnetting on the Near Side of the 'Net This document is designed to give the reader a reasonable working knowledge of TCP/IP subnetting, addressing, and routing.
Cisco Training CCNA IP Addressing - Part 1 of 5. CSMA/CD - A Clay Animation About Computer Networking. Watch How Fiber Optics Are Made Video. Network topology. Ieee Preambels. Introduction to Networking. Introduction to Networking In this day and age, networks are everywhere.
The Internet has also revolutionized not only the computer world, but the lives of millions in a variety of ways even in the “real world”. We tend to take for granted that computers should be connected together. In fact, these days, whenever I have two computers in the same room, I have a difficult time not connecting them together! Given the ubiquitousness of networking, it's hard to believe that the field is still a relatively young one, especially when it comes to hooking up small computers like PCs. In this section, I provide a quick introduction to networking, discussing what it is all about in general terms. Home - Table Of Contents - Contact Us. OSI Reference Model.