

Malware's Most Wanted: CryptoLocker—The Ransomware Trojan. Love From China : Netis Backdoor Exploitation. I came around this news sometime back there is a router Backdoor from NETIS/Netcore Router which allows any attacker,externally connect to the router do some nasty stuffs.So i decided to go along and analyze the firmware and find out really what’s going on with the Netis Router.Before We begin i could like to introduce you the NETIS brand.

Netis is a consumer Electronic Router (Also termed as SOHO) which is mainly from China which sells there as the Brand name of Netcore. They have Various Products from ADSL/ Wireless ranging the Speed from 150 mbps to 300 mbps. They have Very Cheap Products which is useful for small funding firms but are they getting the Security that they should provide? I think not. First Step was me to Download the Firmware from the site where i could analyze it. Requirements: A 32 bit Linux Distro ( Debian/Ubuntu preferred)IDA Proqemu for MIPSSome Knowledge about how Linux works.BinwalkFirmware-analysis-kit Getting Started (netis backdoor): What is the solution? » Gdy na wojnę trzeba pójść… Rzecz o przygotowaniu i wdrożeniu efektywnego procesu zarządzania incydentami bezpieczeństwa informacji w przedsiębiorstwie. [1405.0534] On The Longest Chain Rule and Programmed Self-Destruction of Crypto Currencies. Can Heartbleed be used in DDoS attacks?
With nearly every major threat to information security, it is not long before security experts ask the question, "Can the threat play a role in distributed denial of service (DDoS) attacks?
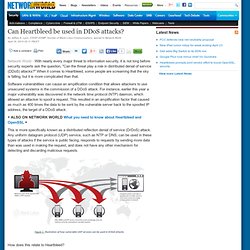
" When it comes to Heartbleed, some people are screaming that the sky is falling, but it is more complicated than that. Software vulnerabilities can cause an amplification condition that allows attackers to use unsecured systems in the commission of a DDoS attack. For instance, earlier this year a major vulnerability was discovered in the network time protocol (NTP) daemon, which allowed an attacker to spoof a request. This resulted in an amplification factor that caused as much as 400 times the data to be sent by the vulnerable server back to the spoofed IP address, the target of a DDoS attack. Check out the new Microsoft Threat Modeling Tool 2014. Threat modeling seeks to solve a fundamental quandary of developing applications: If you haven’t considered all of the potential threats to your software, how can you develop security controls to prevent them?
If you don’t know what you’re defending against, how can you implement effective protection? Microsoft—more specifically Microsoft Trustworthy Computing—is a zealous evangelist for threat modeling. When I visited Redmond in February and spent some time with various leaders in Microsoft Trustworthy Computing, most could not get through a 30-minute conversation without waxing poetic about the benefits and value of effective threat modeling. Now, Microsoft has launched the new Microsoft Threat Modeling Tool 2014 to help others embrace and employ the concept. A post on the Security Development Lifecycle Blog states, “Threat modeling is an invaluable part of the Security Development Lifecycle (SDL) process. Microsoft also made the tool more flexible. Facebook users targeted by iBanking Android trojan app. Cybercriminals have started using a sophisticated Android Trojan app designed for e-banking fraud to target Facebook users, possibly in an attempt to bypass the two-factor authentication protection on the social network.
Security researchers from antivirus vendor ESET have identified a new variant of a computer banking Trojan called Qadars that injects rogue JavaScript code into Facebook pages when opened in a browser from an infected system. The injected code generates a message instructing users to download and install Android malware that can steal authentication codes sent to their phones via SMS. These man-in-the-browser attacks are known as webinjects and have long been used by computer Trojans to display rogue Web forms on online banking websites with the goal of collecting log-in credentials and other sensitive financial information from users. Musalbas/heartbleed-masstest. Wepawet » Home. Texting ATMs for Cash Shows Cybercriminals’ Increasing Sophistication. There is a growing chorus of voices calling for businesses and home users to upgrade existing Windows XP installations to newer versions of Windows, if not for the features, then at least for the improved security and support.
ATMs are basically computers that control access to cash, and as it turns out, almost 95 percent of them run on versions of Windows XP. With the looming end-of-life for Windows XP slated for April 8, 2014, the banking industry is facing a serious risk of cyberattacks aimed at their ATM fleet. This risk is not hypothetical — it is already happening. Cybercriminals are targeting ATMs with increasingly sophisticated techniques. In late 2013, we blogged about new ATM malware in Mexico, which could let attackers force ATMs to spew cash on demand using an external keyboard.
What was interesting about this variant of Ploutus was that it allowed cybercriminals to simply send an SMS to the compromised ATM, then walk up and collect the dispensed cash. Figure 1. Figure 2. 12 terrific tech and security-related TED talks. How Does a Modern Malware Attack Defeat a Layered Security Design? Join this webinar and learn why consistency is the hallmark of an effective, agile organisation.
With thousands of moving parts, ensuring that every user, every system is being managed consistently is critical. This webinar will show you how a best practice IT systems management software effectively defines, manages, applies and enforces IT policies across groups of machines. A state-of-the art Policy Management system streamlines the process of creating, setting and remotely applying IT policies to groups of systems across a distributed organisation. Administrators need to be able to view all policies from a single dashboard, customise them and assign them based on organisation, group, machine type, platform or any dynamic view of machines to ensure all systems are in compliance. By automating management by policies and enforcement, administrators can then take immediate action to remediate any system that is not in compliance. How Does a Modern Malware Attack Defeat a Layered Security Design?