


Portmanteau Word blending the sounds and combining the meanings of two others Thank you, dear donor! Your generosity helps keep Wikipedia thriving. Select "hide appeals" to suppress fundraising messages in this browser for a week, or go back to the appeal if you're still interested in donating. We ask you, humbly: don't scroll away. Hi. Thank you! Origin[edit] You see it's like a portmanteau—there are two meanings packed up into one word. In his introduction to his 1876 poem The Hunting of the Snark, Carroll again uses portmanteau when discussing lexical selection:[12] Humpty Dumpty's theory, of two meanings packed into one word like a portmanteau, seems to me the right explanation for all. An occasional synonym for "portmanteau word" is frankenword, an autological word exemplifying the phenomenon it describes, blending "Frankenstein" and "word".[18] Examples in English[edit] Jeoportmanteau! Oxbridge is a common portmanteau for the UK's two oldest universities, those of Oxford and Cambridge. Irish[edit]
Computer worm Many worms are designed only to spread, and do not attempt to change the systems they pass through. However, as the Morris worm and Mydoom showed, even these "payload-free" worms can cause major disruption by increasing network traffic and other unintended effects. History[edit] On November 2, 1988, Robert Tappan Morris, a Cornell University computer science graduate student, unleashed what became known as the Morris worm, disrupting many computers then on the Internet, guessed at the time to be one tenth of all those connected.[3] During the Morris appeal process, the U.S. Harm[edit] Countermeasures[edit] Worms spread by exploiting vulnerabilities in operating systems. Users need to be wary of opening unexpected email,[13][14] and should not run attached files or programs, or visit web sites that are linked to such emails. Mitigation techniques include: Worms with good intent[edit] Several worms, like XSS worms, have been written to research how worms spread. See also[edit] References[edit]
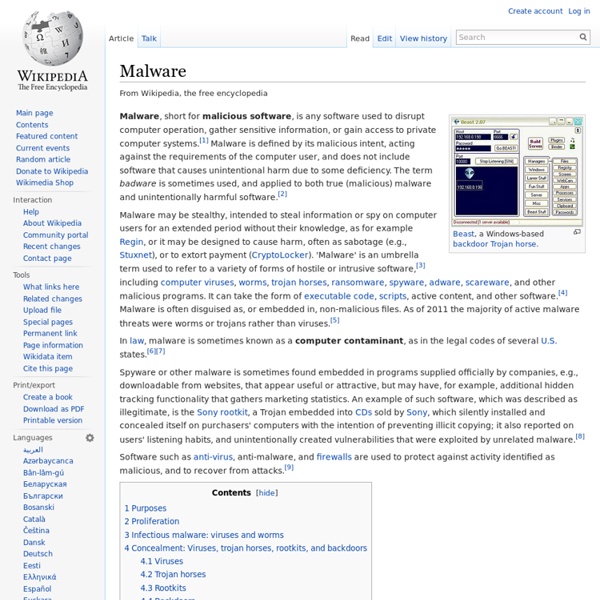
Malware definition – What is it and how to remove it | Malwarebytes You know how every year the medical community campaigns for everyone to get a flu shot? That’s because flu outbreaks typically have a season—a time of year when they start spreading and infecting people. In contrast, there are no predictable seasonal infections for PCs, smartphones, tablets, and enterprise networks. For them, it’s always flu season. But instead of suffering chills and body aches, users can fall ill from a kind of machine malady—malware. Malware infections come at us like a torrent of water from a fire hose, each with its own methods of attack—from stealthy and sneaky to subtle like a sledgehammer. What is malware? Malware, or “malicious software,” is an umbrella term that describes any malicious program or code that is harmful to systems. Hostile, intrusive, and intentionally nasty, malware seeks to invade, damage, or disable computers, computer systems, networks, tablets, and mobile devices, often by taking partial control over a device’s operations. How do I get malware?
Computer virus Computer program that modifies other programs to replicate itself and spread A computer virus[1] is a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs.[2][3] If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses.[4] Computer viruses generally require a host program.[5] The virus writes its own code into the host program. As of 2013, computer viruses caused billions of dollars' worth of economic damage each year.[10] In response, an industry of antivirus software has cropped up, selling or freely distributing virus protection to users of various operating systems.[11] A computer virus generally contains three parts: the infection mechanism, which finds and infects new files, the payload, which is the malicious code to execute, and the trigger, which determines when to activate the payload.[33] Trigger Payload
Malware vs Viruses: What's the Difference? July 27, 2018 | By admin Loading... Understanding the difference between malware and viruses is very important. A virus is just one type of malware, but the term is more widely used by the public. The term malware refers to any malicious software, including a computer virus. Malware is infecting computers and mobile devices at an increasingly greater pace. What is a Malware? Malware is software written specifically to harm and infect the host system. Virus: As discussed, Virus is a specific type of malware by itself. Adware: Adware is also known as advertising-supported software. Spyware: This type of malicious software, spies on you, tracks your internet activities. Worms: This type of malware will replicate itself and destroys information and files saved on the host PC. Trojan: Trojans are a type of virus that are designed to make a user think they are a safe program and run them. Get your Website Secured Today Related Resources: Best Free Antivirus of 2018 Free Virus Protection
Trojan horse (computing) To what extent should one trust a statement that a program is free of Trojan horses? Perhaps it is more important to trust: the people who wrote the software. 5th Grade Weekly Computer Lessons - Qtr.1 Touch Typing, Spreadsheet Budgets with Charts Fifth Grade Technology Lessons focus on (Qtr.1) - typing skills development and spreadsheet budgets with charts, (Qtr.2) coding and logic games, (Qtr.3) graphics / photo editing , and (Qtr.4) presentations. In the 1st Qtr, students continue to develop two hand homerow typing proficiency. Students also create a variety of spreadsheet budgets with charts. Students will learn spreadsheet vocabulary such as rows,columns, cells, data, values, and formulas. Recommendations: Typing Lessons: Focus on typing accuracy and correct finger placement, not speed. File Distribution: Share assignment files using Dropbox, Google Drive, Box.com, Microsoft OneDrive or a shared network drive on your school network server. Enrichment: Use the enrichment activities to support regular classroom curricula. Time Management: These weekly lessons are programmed for 2 weekly sessions of 45 minutes each. Fifth Grade Technology Lesson Schedule: Qtr. 1 - Week 1: Session 1: Oahu
Spyware Malware that collects and transmits user information without their knowledge Spyware (a portmanteau for spying software) is any software with malicious behavior that aims to gather information about a person or organization and send it to another entity in a way that harms the user by violating their privacy, endangering their device's security, or other means. This behavior may be present in malware and in legitimate software. Websites may engage in spyware behaviors like web tracking. Hardware devices may also be affected.[1] Spyware is frequently associated with advertising and involves many of the same issues. The first recorded use of the term spyware occurred on October 16, 1995, in a Usenet post that poked fun at Microsoft's business model.[3] Spyware at first denoted software meant for espionage purposes. The Windows Registry contains multiple sections where modification of key values allows software to be executed automatically when the operating system boots. [edit]
Free Graphic Organizers for Studying and Analyzing Introduction In my opinion, the free graphic organizers that I've been finding recently on the Internet are limited in variety and quality. If you are a regular visitor to Daily Teaching Tools, you may have noticed that two of the last three pages I've added to this site along with this new page, have been devoted entirely to graphic organizers. This hasn't been a coincidence. I'm trying my best to offer you quality graphic organizers WITHOUT draining your wallet. The free ones I'm offering on this page focus entirely on studying and analyzing. And now, the Quick Links. Quick Links for THIS Page You may use the following quick links to go directly to what interests you on this page. Analysis Webs The following graphic organizers are designed to reinforce and extend study and analysis skills that will help kids to be more successful in your class. Let's begin with the ones done in portrait style. Here is a brief slideshow of the ones done in landscape style. Author Study Maps Icebreakers KWL Charts