

All The Cheat Sheets That A Web Developer Needs. How to Design Programs. Programming, Motherfucker - Do you speak it? Philosophy. Philosophy. Top 15 Open Source/Free Security/Hacking Tools. 1.
Nmap Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. Nmap homepage. 2. Wireshark is a network protocol analyzer. 3. Metasploit Community Edition simplifies network discovery and vulnerability verification for specific exploits, increasing the effectiveness of vulnerability scanners. 4.
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers. A Quick, Painless Tutorial on the Python Language. Norman Matloff University of California, Davis June 17, 2008 ©2003-2008, N.

Matloff Contents What Are Scripting Languages? Invent Your Own Computer Games with Python. Chapter 1.

Codecademy Labs. The Best Hacking Tutorial Sites - Learn Legal Hacking. Lecture Slides and Video Archives. "ON TRIAL: LEE HARVEY OSWALD" (PART 21)(WITNESS: DR. CYRIL WECHT) About Cyril H. Wecht, Forensic Pathologist, Attorney, Medical-Legal Consultant. Crime Scene Investigation Articles. Visible Proofs: Forensic Views of the Body: Galleries: Technologies. How To Set Up SSH Encrypted MySQL Replication. CrypTool - Educational Tool for Cryptography and Cryptanalysis. How to Bypass Most Firewall Restrictions and Access the Internet Privately. Ciphers By Ritter: Cryptography and Technology. Ophcrack. Codefetch{
One-Time Pad Generator. This page, which requires that your browser support JavaScript (see Why JavaScript below), generates one-time pads or password lists in a variety of forms.

It is based a high-quality pseudorandom sequence generator, which can be seeded either from the current date and time, or from a seed you provide. Fill in the form below to select the format of the pad and press “Generate” to create the pad in the text box. You can then copy and paste the generated pad into another window to use as you wish. Projects. CrypTool - Educational Tool for Cryptography and Cryptanalysis. Logical Paradoxes.
How to Make Anything Signify Anything. For much of his long and largely secret career, Colonel William F.
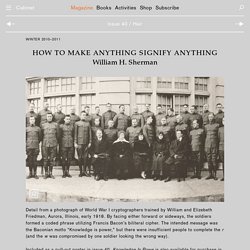
Friedman kept a very special photograph under the glass plate that covered his desk. As desks go, this one saw some impressive action. By the time he retired from the National Security Agency in 1955, Friedman had served for more than thirty years as his government’s chief cryptographer, and—as leader of the team that broke the Japanese PURPLE code in World War II, co-inventor of the US Army’s best cipher machine, author of the papers that gave the field its mathematical foundations, and coiner of the very term cryptanalysis—he had arguably become the most important code-breaker in modern history.1 At first glance, the photo looks like a standard-issue keepsake of the kind owned by anyone who has served in the military.
Yet Friedman found it so significant that he had a second, larger copy framed for the wall of his study. Cryptography. Visual Cryptography. What is Visual Cryptography Visual Cryptography is a special encryption technique to hide information in images in such a way that it can be decrypted by the human vision if the correct key image is used.

The technique was proposed by Naor and Shamir in 1994. Visual Cryptography uses two transparent images. One image contains random pixels and the other image contains the secret information. It is impossible to retrieve the secret information from one of the images. When the random image contains truely random pixels it can be seen as a one-time pad system and will offer unbreakable encryption. How Visual Cryptography works Each pixel of the images is divided into smaller blocks. Handbook of Applied Cryptography. Alfred J.

Menezes, CRC Press ISBN: 0-8493-8523-7 October 1996, 816 pages Fifth Printing (August 2001) The Handbook was reprinted (5th printing) in August 2001. The publisher made all the various minor changes and updates we submitted. Book Publishers. Md5.rednoize.com - reverse engineer md5 hashes - powered by rednoize.com. An Overview of Cryptography. As an aside, the AES selection process managed by NIST was very public.

A similar project, the New European Schemes for Signatures, Integrity and Encryption (NESSIE), was designed as an independent project meant to augment the work of NIST by putting out an open call for new cryptographic primitives. NESSIE ran from about 2000-2003. While several new algorithms were found during the NESSIE process, no new stream cipher survived cryptanalysis. As a result, the ECRYPT Stream Cipher Project (eSTREAM) was created, which has approved a number of new stream ciphers for both software and hardware implementation. Similar — but different — is the Japanese Government Cryptography Research and Evaluation Committees (CRYPTREC) efforts to evaluate algorithms submitted for government and industry applications.
Encryption. Simple Complexity — Making Simple Sense From Complex Data.