

Firesheep. The extension was created as a demonstration of the security risk of session hijacking vulnerabilities to users of web sites that only encrypt the login process and not the cookie(s) created during the login process.[3] It has been warned that the use of the extension to capture login details without permission would violate wiretapping laws and/or computer security laws in some countries.
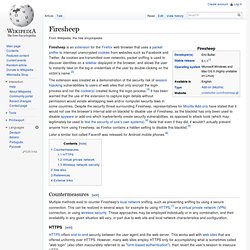
Off The Grid. The grid above contains a highly random arrangement of characters,but with very special properties.

It can be used to encryptwebsite domain names into secure passwords. Why is this useful? This “Off The Grid” technology is the only known system to providesecure encryption using nothing but a specially designed piece of paper. Although this system initially uses software to design and print the grid, no technology of any kind is used to perform the encryption. Every other strong and modern encryption technology relies upon software running in your computer, your browser, your phone, or some other device to encrypt, decrypt, or store your passwords.
“Off The Grid” converts any website's name into a secure password that you never need to write down, store, or remember because you can easily re-create the same secure password from the same website name the next time, and every time, you need it. Even though we can no longer live “offthe grid” . . . at least our passwords can! Password Strength. How long would it take to crack your password? About three years ago, developer Cameron Morris had a personal epiphany about passwords, he recently told ZDNet's John Fontana: The time it takes to crack a password is the only true measure of its worth.

Not whether it has a minimum of x or a maximum of y characters, not whether it's got blah-blah amount of numbers, not whether it includes your frou-frou leetspeak ch@r@ct3rs, not whether it contains the verboten from lists of taboo words. Syntax laws like those make up the typical password policy creations most organizations use and that many security practitioners preach. How Long Would Your Password Take To Crack? If you saw the recent press coverage about the hackers who managed to breach Sony's systems, you'll know that they managed to discover millions of users' passwords which were stored in the systems' databases in an unencrypted form.
Most reputable systems, including Windows itself, store your password in an encrypted form, and there's no way to reverse that encryption to discover the original password. The only option is to simply try every possible combination, in what's known as a brute force attack. Trouble is, computers are very good at doing brute force attacks, and a decently powerful desktop computer can try tens of millions of combinations every second. Ironically, the biggest improvement to password-cracking software in recent years has come about because of the availability of hugely powerful graphics cards. With the right software, the chips that normally render 35 fps of Grand Theft Auto 9 can now crack passwords instead. Are you worried yet? How the Boy Next Door Accidentally Built a Syrian Spy Tool.
Jean-Pierre Lesueur.
Photo: Jean-Pierre Lesueur Jean-Pierre Lesueur is in many ways a typical 22-year-old computer geek. He lives outside of Paris, coding Java by day for a European company that processes airline tickets. He likes playing the piano and reading Stephen Hawking. But he’s also the man who built Dark Comet — which was recently used by the Syrian government to steal information from the computers of activists fighting to overthrow it. Dark Comet is a software application that gives you remote control over another computer, and Lesueur says he wrote it just to prove his programming cred. Sometimes, the boy next door can become a tool in a state-sponsored cyberespionage campaign. According to Lesueur, Dark Comet is no worse than other hacking tools such as Metasploit or BackTrack Linux, which can be used both by legitimate security testers and criminals to launch online attacks against computers and test networks for security flaws.
Twitter Account Retweets People's Postings of Their Debit Cards. Facepalm, as the kids would say. Even if you’re a relative newcomer to the Internet, there are probably some things you would consider unsafe to do — such as, oh, posting a picture of your credit or debit card for all the world to see. And yet, a Twitter account rose to prominence last week for lambasting a practice that’s the digital equivalent of walking down a dark alley with your wallet out and an expensive camera around your neck.
The message of twitter.com/needadebitcard is simple: “Please quit posting pictures of your debit cards, people.” The feed’s followers have piled on to call out and laugh at the people who do just that, and a few appear to have been shamed into better behavior, as some of the photos users linked to have been taken down. (MORE: How Recruiters Use Social Networks to Make Hiring Decisions) No, it’s not the kind of online photo gaffe that will keep you from running for office 20 years from now, but it’s still extremely, colossally stupid.
Plenty.