

Hackers & hacking. How to Build a Maze. Cryptologist- Spies All Around Us! Codes and Ciphers. Hackers & hacking. Willkommen bei Facebook - anmelden, registrieren oder mehr erfahren. Home Audio. Hot Pearls to be sorted. CMD. Vanalidades varias. Free Design Stuff&Tutorials. Tendance. Net Art - Dr. Hugo Heyrman ( ( (Motions of the Mind) ) )
THE PLAIN TRUTH by Judge Napolitano 1/27/12. Hot2. Drbazuk. Florida Trip. Drbazuk. Technology. Crowdsourcing. Reseaux_sociaux_opensource. Free Ebooks. Туроператор TUI Russia & CIS. Туры в Египет, Турцию, Испанию, Чехию, Италию. Более 60 направлений по всему миру для вашего отдыха! Мы организуем туры по всему миру уже более 30 лет. Ciphers & Puzzles. Victoronomy. Miscellaneous. Ciphers & Puzzles. Navajo Code Talkers' Dictionary. Sharky's Vigenere Cipher. This page is for amusement only.
Instructions are given below this form. instructions: Enter the string to encrypt or decrypt in the Input field (you may copy and paste it from another text editor). Enter the key in the Key field. (You may use any sequence of characters, but only alphabetic characters will actually be processed. On most computers: To copy: Highlight text, press Ctrl-C; To paste: Position cursor, press Ctrl-V. explanation: Vigenere coding is one of the most ancient forms of cryptography. Choose a key that is as long as the plaintext message. Unfortunately, these steps take all the fun out of the Vigenere cipher.
Vigenere ciphers with moderate keys are appropriate for situations that do not require failproof security. We hope you enjoy this simple JavaScript-based implementation. Steganography_Decode - Utility Mill - Utility. Www.enigmaco.de/enigma/enigma.swf. GC1M2NP A Lesson in Ciphers # 1 (Unknown Cache) in Missouri, United States created by TripCyclone. This cache series is designed to give you an introduction to the world of ciphers.
It will not cover every type of cipher out there, instead focusing on a small variety of different ciphers. Hopefully, you will walk away from solving this series with a new set of puzzle solving skills. Voynich Manuscript. MP3Stego. When looking at the steganographic tools available on the Net, it occurred to me that nothing had been done to hide information in MP3 files, that is sound tracks compressed using the MPEG Audio Layer III format.
There is a growing interest world-wide in MP3 or indeed WMA files because they offer near-CD quality at compression ratio of 11 to 1 (128 kilobits per second). This gives a very good opportunity for information hiding. Although WMA has better quality in general, I did not have access to code and only an implementation for MP3 is provided as a proof of concept. Cryptography. When I wrote my first book, Fermat’s Last Theorem, I made a passing reference to the mathematics of cryptography.
Keyed Caesar. One variation to the standard Caesar cipher is when the alphabet is "keyed" by using a word.
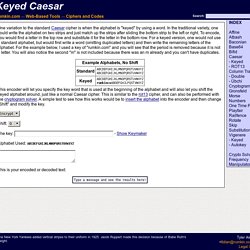
In the traditional variety, one could write the alphabet on two strips and just match up the strips after sliding the bottom strip to the left or right. To encode, you would find a letter in the top row and substitute it for the letter in the bottom row. For a keyed version, one would not use a standard alphabet, but would first write a word (omitting duplicated letters) and then write the remaining letters of the alphabet. May Day Mystery:Historical Madness. Home - www.simplesite.com/the_runes. Category:Puzzlehunts. Carvings riddle stumps villagers. Puzzled residents across Yorkshire are turning detective after mysterious stone heads were left outside their properties in the dead of night.
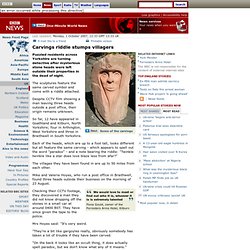
The sculptures feature the same carved symbol and come with a riddle attached. Despite CCTV film showing a man leaving three heads outside a post office, their origin remains unknown. So far, 12 have appeared in Goathland and Kilburn, North Yorkshire; four in Arthington, West Yorkshire and three in Braithwell in South Yorkshire.
Cipher. Codes generally substitute different length strings of characters in the output, whilst ciphers generally substitute the same number of characters as are input.
There are exceptions and some cipher systems may use slightly more, or fewer, characters when output versus the number that were input. Codes operated by substituting according to a large codebook which linked a random string of characters or numbers to a word or phrase. Cipher Tools. Trip's GeoAdventures. President Jefferson's Secret Code. The Cipher File and How to Decipher. Triple goddess.
S List of Famous Unsolved Codes and Ciphers. Add to iGoogle. There, I Fixed It - Redneck Repairs. Log in with OpenID, Facebook or Twitter. Help - Custom Services. Any public service is eligible to be placed in our directory for all to use.
Since approval can take up to a month, and some services are not for public consumption (e.g., on a private intranet, or invitation-only), you may also add any service to your own menu at run-time. Optional Arguments services_custom Optional Array Specify your own AddThis bookmarking services with an array of Javascript configuration object added to the global addthis_config variable: All three fields must be present for each custom service. By default, we assume your icon is 16x16. Note: as of AddThis 3.0, custom services no longer appear in the compact menu by default. Code Examples Example #1 This example creates an AddThis button.
Example #2 This example adds an AddThis toolbox with your custom service. Example #3 This example adds your custom service to our expanded menu. API Reference Check out the full Client API specification to learn more.