Anonymity
> Internet & location privacy/security
Anonymized Phone Location Data Not So Anonymous, Researchers Find. Anonymized mobile phone location data produces a GPS fingerprint that can be easily used to identify a user based on little more than tracking the pings a phone makes to cell towers, a new study shows.
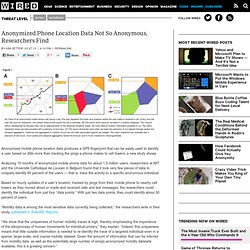
Analyzing 15 months of anonymized mobile phone data for about 1.5 million users, researchers at MIT and the Universite Catholique de Louvain in Belgium found that it took very few pieces of data to uniquely identify 95 percent of the users — that is, trace the activity to a specific anonymous individual. Based on hourly updates of a user’s location, tracked by pings from their mobile phone to nearby cell towers as they moved about or made and received calls and text messages, the researchers could identify the individual from just four “data points.”
With just two data points, they could identify about 50 percent of users. “Mobility data is among the most sensitive data currently being collected,” the researchers write in their study, published in Scientific Reports.
FBI Seized Anonymizer Server. The US State Department keeps saying it wants to support a free and open internet, and to build systems that protect dissedents and reformers who are speaking out.
But it seems that they can't get the message through to the rest of the US government. Apparently the FBI has seized a server used by various people to anonymize their emails, because it was also used as part of a bomb threat: On Wednesday, April 18, at approximately 16:00 Eastern Time, U.S. Federal authorities removed a server from a colocation facility shared by Riseup Networks and May First/People Link in New York City. The seized server was operated by the European Counter Network (“ECN”), the oldest independent internet service provider in Europe, who, among many other things, provided an anonymous remailer service, Mixmaster, that was the target of an FBI investigation into the bomb threats against the University of Pittsburgh.
Your Morning Commute is Unique: On the Anonymity of Home/Work Location Pairs. May 13, 2009 at 6:42 am.

Commute.pdf (application/pdf Object)
De-anonymization is not X: The Need for Re-identification Science 33 Bits of Entropy. October 14, 2009 at 9:42 pm.

De-anonymizing Social Networks. Operators of online social networks are increasingly sharing potentially sensitive information about users and their relationships with advertisers, application developers, and data-mining researchers.

Privacy is typically protected by anonymization, i.e., removing names, addresses, etc. We present a framework for analyzing privacy and anonymity in social networks and develop a new re-identification algorithm targeting anonymized social-network graphs.
Identifying People using Anonymous Social Networking Data. There is no such thing as anonymous online tracking. A 1993 New Yorker cartoon famously proclaimed, "On the Internet, nobody knows you're a dog.
" The Web is a very different place today; you now leave countless footprints online. You log into websites. You share stuff on social networks. You search for information about yourself and your friends, family, and colleagues.
Google+ and the loss of online anonymity. On the Issue of Pseudonymity. Honestly, I feel like I write this post every year.
Or at least discuss writing it every year. Usually other people say what I think much better on these issues than I do. And yet, every time, I hear from people, via Twitter, Email, etc, saying I should join under my Real Name.
Google+ Identity Crisis: What’s at Stake With Real Names and Privacy. After a steady stream of angry blog posts and heated debate among its own users over the value of pseudonymity on the web, Google announced Monday that it was revising its “real name” policy, at least for display, on Google+.
In a post on Google+, Google VP Bradley Horowitz promised greater transparency, particularly in suspension of user profiles. The new algorithm — human as well as computational — offers users a chance to correct their profiles before suspension. In the past week, most banned profiles simply disappeared without warning. The great Google+ profile purge began last week with business and media company profiles: ABC News Radio, Sesame Street, Wired. This wasn’t a surprise: Google had stated that it wanted to limit the social network to individuals until it could set up special pages for businesses.
Danish Police Aim to End Anonymity on the Internet.
Best Free Anonymous Surfing Service. Read this article in Spanish (Español) Introduction This is the 21st century, the so-called Digital Age, an age where information is more public than it is private.
The sheer growth and pervasiveness of the Internet have led to additional concerns over privacy issues for a great number of people. As we are entitled to our privacy in the physical world, why not so in the virtual one too?
Home Internet with Anonymity Built In. Many political activists, nonprofits, and businesses use an anonymity system called Tor to encrypt and obscure what they do on the Internet.

Now the U.S.
-based nonprofit that distributes Tor is developing a low-cost home router with the same privacy protection built in. The Tor software masks Web traffic by encrypting network messages and passing them through a series of relays (each Tor client can also become a relay for other users’ messages). But using Tor has typically meant installing the software on a computer and then tweaking its operating system to ensure that all traffic is routed correctly through the program.









