

Come datare foto su iPhone. Adblock Plus.
Open Fiber - Connettiamo l’Italia,1 gigabit alla volta. How to create Telegram-like channels on WhatsApp. One of the main reasons that many users prefer Telegram over WhatsApp is because the latter doesn’t offer the mass distribution channels that Telegram is known for.
For those who aren’t aware, Telegram lets users create massive groups where only the admins can send information to their enormous audience. It just so happens that we have one where we share the most important news from Uptodown. However, in one of the latest versions of WhatsApp, it’s possible for only admins to send messages. Here we explain how to create a channel on WhatsApp. The first thing you have to do is create a group as usual, opening the drop-down menu in the upper right corner of the screen and tapping New group.After you do that and open your group, you have to open a new menu inside the chat itself and go to Group info.
Beyond adding an image and description, the most important option is found in the Group settings section. Modem - Router generico - INTERNET: Modem ADSL e Fibra TIM - Assistenza Tecnica 187 Alice Telecom Italia. Phone Number Validation: Verify Numbers in 3 Seconds.
Pentesting. Phones and Tablets. School webpages. Ubuntu in Win 10. WordPress. ERP e CRM open source. Free Proxy List - Just Checked Proxy List. URL Shortener, Custom Branded URLs, API & Link Management. Web Hosting Search Tool, Reviews & More at WhoIsHostingThis.com. Tutorial To Test Internet Speed In Linux Using Command Line. Tutorial To Test Internet Speed In Linux Using Command Line It’s always fun to use Terminal to do the normal thing in a geeky way.
Here, we are going to write about the method test Internet speed in Linux and we will talk about geeky way to do the Internet testing. We will be using command line to test Internet speed in Linux. Test Internet Speed In Linux Using Command Line For Ubuntu Operating System: Launch ‘Terminal’ in your Ubuntu. Sudo apt install speedtest-cli After the installation is complete, Start testing the internet speed of your Network. Speedtest Testing Internet Speed in Arch Linux, Manjaro, and other derivatives Use the following command in terminal to download ‘Speedtest’ tool. Website Speed and Performance Optimization.
Redirect Detective - A Free Tool To Trace Where Redirects End Up. Campaign URL Builder — Google Analytics Demos & Tools. Screaming Frog SEO Spider Tool & Crawler Software. About The Tool The Screaming Frog SEO Spider is a fast and advanced SEO site audit tool. It can be used to crawl both small and very large websites, where manually checking every page would be extremely labour intensive, and where you can easily miss a redirect, meta refresh or duplicate page issue.
You can view, analyse and filter the crawl data as it’s gathered and updated continuously in the program’s user interface. The SEO Spider allows you to export key onsite SEO elements (URL, page title, meta description, headings etc) to a spread sheet, so it can easily be used as a base for SEO recommendations. Check our out demo video above. Crawl 500 URLs For Free. How to Identify the Cookies Your Site Installs in Browsers.
How do I know which cookies are installed by my website?
To properly inform users about cookies that your site installs in their browsers, you must learn to identify them. This is not an easy task, so we have created a brief guide to help you with it. 1 – Browser extensions The identification of cookies installed on your website may end up being a result from the combined use of different tools, the main and most commonly used are Wappalyzer and BuiltWith, both are available as add-ons to all the most widely used browsers and allow a thorough analysis of all the resources and technologies implemented within a website. Atom. MAC Vendor Lookup Tool & API. Network Tools by YouGetSignal.com. Online Ping, Traceroute, DNS lookup, WHOIS, Port check, Reverse lookup, Proxy checker, Bandwidth meter, Network calculator, Network mask calculator, Country by IP, Unit converter.
Hunter. Con Opera si può attivare una VPN gratuita, illimitata e integrata - Navigaweb.net. Web Hosting Search Tool, Reviews & More at WhoIsHostingThis.com. WGET - Online Tool. Hashbot. Recuva - Free Data Recovery tool - Free Download. Navigare in privato con la modalità di navigazione in incognito - Computer - Guida di Google Chrome. Tips, Tools and How-tos for Safer Online Communications. Boot Camp - Supporto Apple. Linux Commando: Splitting up is easy for a PDF file.
Occasionally, I needed to extract some pages from a multi-page pdf document.
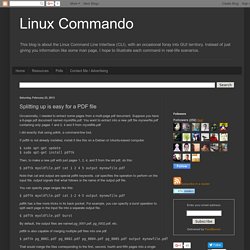
Suppose you have a 6-page pdf document named myoldfile.pdf. You want to extract into a new pdf file mynewfile.pdf containing only pages 1 and 2, 4 and 5 from myoldfile.pdf. I did exactly that using pdktk, a command-line tool. If pdftk is not already installed, install it like this on a Debian or Ubuntu-based computer. $ sudo apt-get update $ sudo apt-get install pdftk. 25, 465, 587... What port should I use? It's a common question that we receive here at Mailgun.
To ensure connectivity to our Simple Mail Transfer Protocol (SMTP) endpoint, Mailgun offers multiple port options, but which one should you use? United Nations Interregional Crime and Justice Research Institute. Fast & Secure Browser, Maxthon Cloud Browser. Remove hidden data and personal information by inspecting documents. If you plan to share an electronic copy of a Microsoft Word document with clients or colleagues, it is a good idea to review the document for hidden data or personal information that might be stored in the document itself or in the document properties (metadata).
Because this hidden information can reveal details about your organization or about the document itself that you might not want to share publicly, you might want to remove this hidden information before you share the document with other people. This article describes how the Document Inspector feature in Word can help you find and remove hidden data and personal information in your documents. In this article Find and remove hidden data and personal information Types of hidden data and personal information. Angry IP Scanner - the original IP scanner for Windows, Mac and Linux.
Google Hacking Diggity Project – Bishop Fox. Sometimes, the best defense is a good offense.
Bishop Fox’s attack tools for Google Hacking level the playing field by allowing our clients to find information disclosures and exposed vulnerabilities before others do. Arm yourself with our arsenal of attack tools that leverage Google, Bing, and other popular search engines. RingMeMaybe - Disposable & Temporary Phone Number App. VirusTotal - Free Online Virus, Malware and URL Scanner. How to View Passwords Hidden Under Asterisks [Video] Google Chrome, Firefox and other browsers hide passwords behind asterisks but you can easily view the saved passwords using the built-in developer tools.
![How to View Passwords Hidden Under Asterisks [Video]](http://cdn.pearltrees.com/s/pic/th/passwords-hidden-asterisks-40134694)
Web browser hide passwords under asterisk characters for improved security. For mobile - Disposable Email Address. Linux Text Editors. Linux Editors for Plain Text: Linux editors for plain text can be divided into two categories, graphical GUI editors and console text editors.
The advantage of the GUI editor is intuitive user friendly interface while the benefit of the console text editor is the suitability over long distance network connections which may or may not provide suitable bandwidth or reliability which would both be required by the GUI editors for remote operation. Console Based Editors: Graphical GUI Editors: Structured Text editors: Come entrare nel Bios UEFI Windows 10, 8.1 e 8. Boot da pendrive usb con UEFI Bios. 7 Sins. 4chan. Crack/Keygen Sites That Are Safe To Use. Blindly searching the web for cracks & keygens is about as smart as using Limewire to search for antivirus software - something not well-advised. Undoubtedly and unfortunately, the number of crack sites with overtones of a malicious agenda heavily outweigh sites that just want to serve up the honest goods. Having said that, there actually are quite a few creditable ‘crack’ sites that won’t try to bombard you with full-screen popup ads, or commandeer your computer into a spam-loving Kraken or Srizbi Botnet army.
We’ve done the hard work for you, and present a list of “clean” crack sites for all the latest warez. Levels of the Deep Web & Internet. What are the Levels? There are, supposedly, 5 levels of the deep web (not counting Level 0). According to an anon, however, three more levels exist after the 5th one. This is yet to be proven, but all eight levels will be listed and described whatsoever. The levels are supposed to be more and more difficult to access following their number; for example, only a simple proxy is needed to access Level 2, but complex hardware is apparently needed to access parts of Level 4, and all the following levels.
ABC Sicurezza: Google Dorking. BGproxy.org - The Bulgarian Proxy - Българско Прокси. ThePirateBay-proxylist.org - A list with fast piratebay proxies. ProtonMail Is the Easiest Way to Send and Receive Encrypted Emails. SANS Information Security Training. Tools.bartlweb.