

Tugaflix.com - Filmes e Séries Online. First_Hop_Redundancy.pdf. Cisco IOS 15 ssh key auth. Port Security. Port security is a layer two traffic control feature on Cisco Catalyst switches.
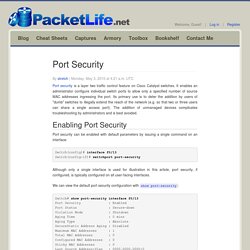
It enables an administrator configure individual switch ports to allow only a specified number of source MAC addresses ingressing the port. Its primary use is to deter the addition by users of "dumb" switches to illegally extend the reach of the network (e.g. so that two or three users can share a single access port). The addition of unmanaged devices complicates troubleshooting by administrators and is best avoided. Iadnat-stateful-nat64.pdf.
IKEv2 RA VPN. VPN IKEv2. Cisco ASA VPN: Site to Site with IKEv2 and Router part 1. Hello Recently I’m working with a new Cisco ASA 5500-X series box.
It will be used for Remote Access, and Site-to-Site VPN for Branch Offices. Because from version 8.4 ASA supports ikev2 and part of my branch routers also. I decided play a little bit with an ikev2. At the first step I took the ASA VPN Site-to-Site on the board. Cisco - How to configure an IKEv2 Site to Site IPSEC VPN ? Written on .
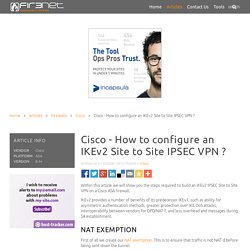
Posted in Cisco Within this article we will show you the steps required to build an IKEv2 IPSEC Site to Site VPN on a Cisco ASA firewall. IPv6 IPv4 network interconnection, NAT-PT (v4-mapped) Hello , I am trying to setup nat-pt so that an ipv6-only network can communicate with an ipv4-only network and vice-versa..
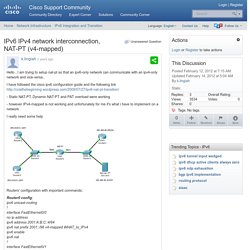
I have followed the cisco ipv6 configuration guide and the following link - Static NAT-PT, Dynamic NAT-PT and PAT overload were working. EtherChannel considerations. EtherChannel is Cisco's term for bundling two or more physical Ethernet links for the purposes of aggregating available bandwidth and, to a lesser extent, providing a measure of physical redundancy.

Under normal conditions, all but one redundant physical link between two switches will be disabled by STP at one end. With EtherChannel configured, multiple links are grouped into a port-channel, which is assigned its own configurable virtual interface. The bundle is treated as a single link. EtherChannel Negotiation. FreeRADIUS Used for Administrative Access on Cisco IOS Configuration Example. Introduction This document describes how to configure RADIUS Authentication on Cisco IOS® switches with a third party RADIUS server (FreeRADIUS).
This example covers the placement of a user directly into privilege 15 mode upon authentication. Prerequisites Requirements. Cisco Network Security Technologies and Solution: IKE Version 2 (IKEv2) based VPN. Author: Sandeep Yadav, CCIE#42053 - Technical Head | CCIE Network Security Consultant, Covenant Network Technologies Pvt Ltd (Inter-networkz), Bangalore.

Lab Topology: Devices Used for the Lab: c7200-adventerprisek9-mz.152-4.S2.binVideo is available on YouTube for the same Lab topology: IKEv2 Based VPN- (with Audio)Cisco Site-To-Site IPsec VPN Using IKEv2- Part1Cisco Site-To-Site IPsec VPN Using IKEv2- Part2In IKEv1 i.e. Internet Key Exchange Version 1 we have two PHASE:PHASE-I and PHASE-IIPHASE-I is also known as ISAKMP Phase.ISAKMP stands for Internet Security Association and Key Management Protocol.In PHASE-I we have two protocols working for successful establishment of PHASE-I SA (Security Association or Tunnel ) 1. ISAKMP 2. How to configure Site-to-Site IKEv2 IPSec VPN using Pre-Shared Key Authentication. If you are new to the basic concepts of VPN (Virtual Private Network) and IPSec, please learn following lessons before continuing.

What is VPN (Virtual Private Network) What is IPSec and Why we need IPSec. Cisco ASA Site-to-Site IKEv2 IPSEC VPN - Networklessons.com. IKEv2 has been published in RFC 5996 in September 2010 and is fully supported on Cisco ASA firewalls.
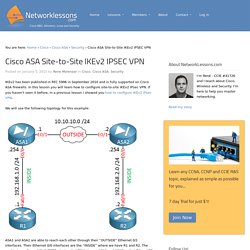
In this lesson you will learn how to configure site-to-site IKEv2 IPsec VPN. If you haven’t seen it before, in a previous lesson I showed you how to configure IKEv2 IPsec VPN. We will use the following topology for this example: ASA1 and ASA2 are able to reach each other through their “OUTSIDE” Ethernet 0/1 interfaces. CCNP Studies: Configuring DHCP Snooping. I’ve been enthralled with the security features for Catalyst switches.

I’ve had to plug away at the theory and lab work recently, but have probably gone a little further down the rabbit hole in this area. I feel that solid knowledge of DHCP Snooping is needed as a foundation for other security features. Both IP Source Guard and Dynamic ARP Inspection rely on it, so if you’ve got your head around snooping, you’ll be in good shape. Cisco IOS SPAN and RSPAN.
Cisco Catalyst Switches have a feature called SPAN (Switch Port Analyzer) that lets you copy all traffic from a source port or source VLAN to a destination interface. This is very useful for a number of reasons: If you want to use wireshark to capture traffic from an interface that is connected to a workstation, server, phone or anything else you want to sniff.Redirect all traffic from a VLAN to an IDS / IPS.Redirect all VoIP calls from a VLAN so you can record the calls.
The source can be an interface or a VLAN, the destination is an interface. How To Configure DNS Server On A Cisco Router. The DNS protocol is used to resolve FQDN (Fully Qualified Domain Names) to IP addresses around the world. This allows us to successfully find and connect to Internet websites and services no matter where they are. Its usefulness, however, doesn't stop there: local company and private networks also rely on DNS to operate efficiently and correctly. This documentation has been moved - Implementing NAT-PT for IPv6 [Support] CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1 - Configuring IPSec and ISAKMP [Cisco ASA 5500-X Series Next-Generation Firewalls] Configuring ISAKMP This section describes the Internet Security Association and Key Management Protocol (ISAKMP) and the Internet Key Exchange (IKE) protocol. This section includes the following topics: Configuring IKEv1 and IKEv2 Policies. [Config] help completing vpn configuration - asa5505 - Cisco.
Site-to-Site IKEv2 Tunnel between ASA and Router Configuration Examples. Introduction This document describes how to set up a site-to-site Internet Key Exchange version 2 (IKEv2) tunnel between a Cisco Adaptive Security Appliance (ASA) and a router that runs Cisco IOS® software. Prerequisites Requirements Cisco recommends that you have knowledge of these topics: Internet Key Exchange version 2 (IKEv2)Certificates and Public Key Infrastructure (PKI)Network Time Protocol (NTP)
CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1 - Configuring Remote Access VPNs [Cisco ASA 5500-X Series Next-Generation Firewalls] CLI Book 3: Cisco ASA Series VPN CLI Configuration Guide, 9.1 - Configuring Remote Access VPNs [Cisco ASA 5500-X Series Next-Generation Firewalls] Dynamic Site to Site IKEv2 VPN Tunnel Between an ASA and an IOS Router Configuration Example. Introduction This document describes how to configure a site-to-site Internet Key Exchange Version 2 (IKEv2) VPN tunnel between an Adaptive Security Appliance (ASA) and a Cisco router where the router has a dynamic IP address and the ASA has a static IP address on the public-facing interfaces. Prerequisites. How to Configure EtherChannel on Cisco Switch. SSH with key authentication on Cisco IOS devices.