

OSI Pizza example. OSI Pizza - Full Article. Encapsulation process. OSI model LAN. VTP Pruning. Introduction As you would be aware a switched network creates one broadcast domain, similar to that of a VLAN powered network where all nodes belonging to the same VLAN are part of the same broadcast domain, receiving all broadcasts sent on their network.
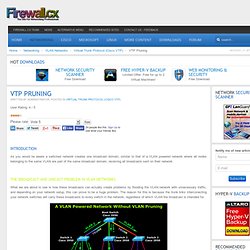
The Broadcast And Unicast Problem In VLAN Networks What we are about to see is how these broadcasts can actually create problems by flooding the VLAN network with unnecessary traffic, and depending on your network setup, this can prove to be a huge problem. The reason for this is because the trunk links interconecting your network switches will carry these broadcasts to every switch in the network, regardless of which VLAN the broadcast is intended for. As shown and described, a host connected to a port configured for VLAN 2 on Switch 1 (first switch on the left), generates a network broadcast. In addition, the Catalyst switch will forward the broadcast out its trunk link, so it may reach all ports in the network assigned to VLAN 2.
Static Route interface vs Next hop vs Both. Old CCIE Myths: VTP. Every aspiring CCIE knows this one.

VTP has 3 versions, of which one we don’t have available in the lab – version 3. Versions 1 and 2 behave differently when the switch is configured in VTP transparent mode. This blog takes a stab at that established truth. Theory. HSRP,VRRP,GLBP Comparison. Secondary IP addresses and HSRP. Enhanced Interior Gateway Routing Protocol. Introduction Enhanced Interior Gateway Routing Protocol (EIGRP) is an interior gateway protocol suited for many different topologies and media.
In a well designed network, EIGRP scales well and provides extremely quick convergence times with minimal network traffic. EIGRP Theory of Operation Some of the many advantages of EIGRP are: very low usage of network resources during normal operation; only hello packets are transmitted on a stable network when a change occurs, only routing table changes are propagated, not the entire routing table; this reduces the load the routing protocol itself places on the network rapid convergence times for changes in the network topology (in some situations convergence can be almost instantaneous) EIGRP is an enhanced distance vector protocol, relying on the Diffused Update Algorithm (DUAL) to calculate the shortest path to a destination within a network.
Major Revisions of the Protocol. Special-Use IPv6 Addresses. [Docs] [txt|pdf] [draft-ietf-v6ops-...]

[Diff1] [Diff2] [IPR] Obsoleted by: 6890 INFORMATIONAL Network Working Group M. Blanchet Request for Comments: 5156 Viagenie Category: Informational April 2008 Status of This Memo This memo provides information for the Internet community. It does not specify an Internet standard of any kind. Distribution of this memo is unlimited. Understanding OSPF Database. Introduction OSPF, being a link-state protocol, allows for every router in the network to know of every link and OSPF speaker in the entire network.
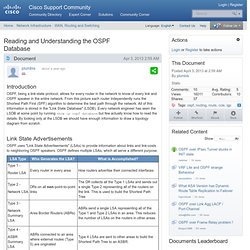
From this picture each router independently runs the Shortest Path First (SPF) algorithm to determine the best path through the network. All of this information is stored in the "Link State Database" (LSDB). Every network engineer has seen the LSDB at some point by running show ip ospf database but few actually know how to read the details. By looking only at the LSDB we should have enough information to draw a topology diagram from scratch. How to Calculate TCP throughput for long distance WAN links. So you just lit up your new high-speed link between Data Centers but are unpleasantly surprised to see relatively slow file transfers across this high speed, long distance link — Bummer!

Before you call Cisco TAC and start trouble shooting your network, do a quick calculation of what you should realistically expect in terms of TCP throughput from a one host to another over this long distance link. When using TCP to transfer data the two most important factors are the TCP window size and the round trip latency. If you know the TCP window size and the round trip latency you can calculate the maximum possible throughput of a data transfer between two hosts, regardless of how much bandwidth you have. Cisco ASA Configuration Cleanup Tool - TunnelsUP.
MicroNugget: Configuring SPAN and RSPAN on a Cisco Switch. IOS upgrade! Anytime Cisco releases a new IOS image for its network switch (or router), it is recommended that you upgrade it.
This article explains 7 easy steps to upgrade IOS image on a cisco switch or router. Since you’ll be upgrading the IOS image, make sure you have physical access to the switch and you are in front of it. Use a console cable to connect to the switch. Please note that the steps given below will be similar to both switches and routers. How the network statement works! Cisco Hardening. Desde ya hace bastante tiempo que deseo publicar esto... se trata de algunas de las practicas más comunes utilizadas para hacer de tu equipo de redes Cisco un dispositivo más seguro.
Esta claro que las necesidades de seguridad de persona a persona, pero como un muy buen amigo me dijo una vez "la seguridad nunca esta de más". NOTA: No todos los comandos funcionaran en todos los dispositivos (router o switch). Es altamente recomendable probar estos comandos previamente en un entorno de pruebas antes de ser implementados a producción. Si bien hay demasiados aspectos que se pueden cubrir, solo me enfocare en cuatro elementos que considero críticos, estos elementos son: Cisco IOS hardening. Cisco ASA hardening. Cisco-router-hardening-step-by-step. /Cisco/Firewall/ASA/ASDM/7.x/7.4.x. Security Appliance System Log Messages, Version 7.0 - Messages Listed by Severity Level [Cisco ASA 5500 Series Adaptive Security Appliances. Table Of Contents. PPTP vs L2TP vs OpenVPN vs SSTP vs IKEv2 - BestVPN.com. With Edward Snowden’s shocking revelations that the NSA has for years been working to crack and subvert VPN encryption technologies, together with the fact that it is becoming increasingly obvious that most such technologies have been developed and certified by the US government’s National Institute of Standards and Technology (NIST) and may therefore be considered suspect, we have decided it is time to revisit and update this popular article.
We will start with a rundown of the major differences between the different VPN protocols and how they affect you, before looking in more detail at the key concepts involved in cryptography, and how the NSA’s assault on encryption standards affects VPN users. The discussion below is rather technical, and although I have made every effort to make it as approachable as possible, you may prefer to just jump to the end of the article for a quick summary. Pros Client built-in to just about all platformsVery easy to set upFast Cons L2TP and L2TP/IPsec.
L2L-VPN - ikev2 - troubleshooting. I would like to review the commons mistakes in the L2L VPN (ikev2) configuration on IOS routers ans Cisco ASAs.
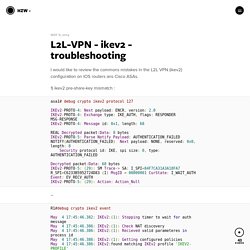
Most Common L2L and Remote Access IPsec VPN Troubleshooting Solutions. Introduction This document contains the most common solutions to IPsec VPN problems. These solutions come directly from service requests that the Cisco Technical Support have solved. Many of these solutions can be implemented prior to the in-depth troubleshooting of an IPsec VPN connection.