

How to Use Wireshark to Capture, Filter and Inspect Packets. 5 Killer Tricks to Get the Most Out of Wireshark. Wireshark has quite a few tricks up its sleeve, from capturing remote traffic to creating firewall rules based on captured packets.
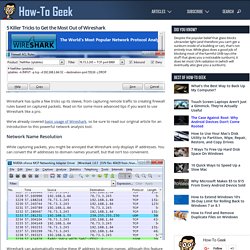
Read on for some more advanced tips if you want to use Wireshark like a pro. We’ve already covered basic usage of Wireshark, so be sure to read our original article for an introduction to this powerful network analysis tool. Network Name Resolution While capturing packets, you might be annoyed that Wireshark only displays IP addresses. You can convert the IP addresses to domain names yourself, but that isn’t too convenient. Wireshark can automatically resolve these IP address to domain names, although this feature isn’t enabled by default. You can enable this setting by opening the preferences window from Edit -> Preferences, clicking the Name Resolution panel and clicking the “Enable Network Name Resolution” check box. Packet Tracer. Cisco Packet Tracer is a powerful network simulation program that allows students to experiment with network behavior and ask “what if” questions.
As an integral part of the Networking Academy comprehensive learning experience, Packet Tracer provides simulation, visualization, authoring, assessment, and collaboration capabilities and facilitates the teaching and learning of complex technology concepts. Packet Tracer supplements physical equipment in the classroom by allowing students to create a network with an almost unlimited number of devices, encouraging practice, discovery, and troubleshooting. The simulation-based learning environment helps students develop 21st century skills such as decision making, creative and critical thinking, and problem solving. IP subnetting made easy. George Ou explains IP subnetting using his own graphical approach.
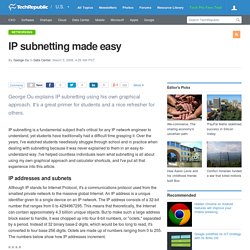
It's a great primer for students and a nice refresher for others. VLAN. IT Certification and Training Blog. NAT and PAT - What's the Difference? NAT and PAT - What's the Difference?

Posted by Kelson Lawrence on Tue, Feb 08, 2011 @ 10:22 AM. Nexus 5000 Series NX-OS Software Configuration Guide - Configuring VLANs [Cisco Nexus 5000 Series Switches] Configuring VLANs You can use virtual LANs (VLANs) to divide the network into separate logical areas.
![Nexus 5000 Series NX-OS Software Configuration Guide - Configuring VLANs [Cisco Nexus 5000 Series Switches]](http://cdn.pearltrees.com/s/pic/th/configuration-configuring-93730574)
VLANs can also be considered as broadcast domains. Any switch port can belong to a VLAN, and unicast, broadcast, and multicast packets are forwarded and flooded only to end stations in that VLAN. Each VLAN is considered a logical network, and packets destined for stations that do not belong to the VLAN must be forwarded through a router. This chapter includes the following sections: LAN Network Cable Media and Connectors.
This article takes a look at the LAN network cable media that is typically installed in most environments and the different connectors that are often used.
Like this article? We recommend When coming into the networking or Internet Technology (IT) field, it is often overwhelming, this is because there are so many different things that are expected to be known upfront. Cisco LAN Switching Fundamentals: Configuring Switches > An Ounce of Planning. This chapter covers the following topics: An ounce of planningConfiguration overviewInitial configurationConnecting the switchesConfiguring the access layerConfiguring SNMP Now that you have learned about the concepts behind Layer 2 and Layer 3 switching in some detail, you will focus on a start-to-finish configuration of a relatively simple campus switching design in this chapter.
Everyone has probably heard the old joke "ready, fire, aim. " Routing 101: The Basics [Networking Fundamentals] In a small business LAN, the primary networking devices are network interface cards (NICs), that connect PC's and servers to the LAN, and Hubs and/or switches that interconnect the various LAN devices and create the Ethernet backbone.
![Routing 101: The Basics [Networking Fundamentals]](http://cdn.pearltrees.com/s/pic/th/networking-fundamentals-108643795)
These devices operate at Layer 2 (the data link layer) of the OSI reference model. For the LAN users to connect to the Internet or to a remote branch office a device called a router must be used. A router passes data between multiple networks. It works at the OSI Network Layer (Layer3), which means that it must be able to understand the data packets so that it can route them to their destination.
The Undersea Cables that Connect the World. What you see above is a submarine communications cable.
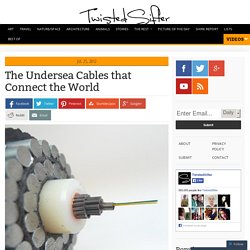
With a diameter of 69 millimeter (2.7 inches), it carries 99% of all international traffic (i.e., internet, telephony and private data) and connects every continent on Earth with the exception of Antarctica. These amazing fibre optic cables traverse oceans and span hundreds of thousands of kilometers. Below you will find pictures, descriptions and links to much more informative resources about this incredible network of cables that connect our planet. Map of the Worldwide Undersea Submarine Cable Network. Submarine Cable Map 2014. Comprehensive Guide to Configuring and Troubleshooting Frame Relay. Introduction Frame Relay is an industry-standard, switched data link layer protocol that handles multiple virtual circuits using High-Level Data Link Control (HDLC) encapsulation between connected devices.

In many cases, Frame Relay is more efficient than X.25, the protocol for which it is generally considered a replacement. Troubleshooting PPP (CHAP or PAP) Authentication. Introduction Point-to-Point Protocol (PPP) authentication issues are one of the most common causes for dialup link failures. This document provides some troubleshooting procedures for PPP authentication issues. Subnetting made easy subnet 101 Only 16 minutes to become Subnet Guru! Configuring IP Access Lists. Introduction This document describes how IP access control lists (ACLs) can filter network traffic. It also contains brief descriptions of the IP ACL types, feature availability, and an example of use in a network. Access the Software Advisor (registered customers only) tool in order to determine the support of some of the more advanced Cisco IOS® IP ACL features. contains assigned numbers of well-known ports. RFC 1918 contains address allocation for private Internets, IP addresses which should not normally be seen on the Internet.
Home - Networking Academy.