

Renewing ADFS 2.0 Certificates in SharePoint 2013. First export your certificate(s) from ADFS.
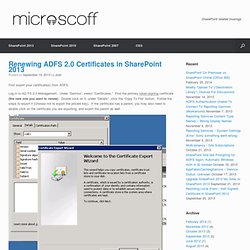
Log in to AD FS 2.0 Management. Under “Service”, select “Certificates.” AD FS 2.0: How to Replace the SSL, Service Communications, Token-Signing, and Token-Decrypting Certificates. Replacing the SSL and Service Communications certificate *Note - Replacing the SSL and Service Communications certificates go hand-in-hand.
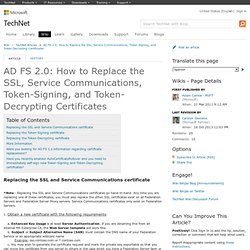
Any time you are replacing one of these certificates, you must also replace the other. SSL certificates exist on all Federation Servers and Federation Server Proxy servers. Service Communications certificates only exist on Federation Servers. 1. Obtain a new certificate with the following requirements a. *Note - Be careful when making your certificate selection. D. How to renew your ADFS 2.0 token signing certificate in SharePoint.
Over the past year or so, Content and Code have found that Active Directory Federation Services (ADFS) has become a more common requirement for both cloud and on-premises SharePoint deployments.

Although we find that it is often implemented to facilitate single sign on across otherwise disconnected infrastructure, we have also deployed it to support claims augmentation for SharePoint environments that utilise SAML claims. As such, we have built up a fair chunk of experience deploying and operating ADFS in both production and our own internal development environments. AD FS 2.0 token signing certificate roll over results in loss of access to all Office 365 services.
If single sign-on users (also known as federated users) are experiencing any of the following symptoms, it may be due to an expired certificate that needs to be updated in Windows Azure Active Directory.
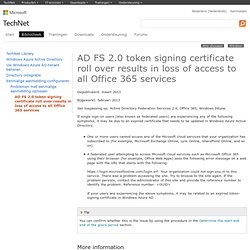
One or more users cannot access any of the Micosoft cloud services that your organization has subscribed to (for example, Microsoft Exchange Online, Lync Online, SharePoint Online, and so on). A federated user attempting to access Micosoft cloud services such as Microsoft Office 365 using their browser (for example, Office Web Apps) sees the following error message on a web page with the URL that starts with the following: Your organization could not sign you in to this service.
There was a problem accessing the site. Try to browse to the site again. If the problem persists, contact the administrator of this site and provide the reference number to identify the problem. More information. Setting the ADFS Timeout for CRM 2011 Internet Facing Deployments (IFD) - TechNet Articles - United States (English)
Link to Dynamics CRM Wiki Home Page Once you deploy ADFS in a functional environment, the users will generally receive timeout requests, or requests to log back in, which can quickly become an issue within an 8 hour shift (480 minutes).
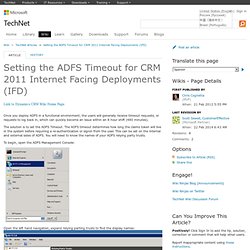
The solution is to set the ADFS Timeout. The ADFS timeout determines how long the claims token will live in the system before requiring a re-authentication or signin from the user. This can be set on the internal and external sides of ADFS. You will need to know the names of your ADFS relying party trusts. To begin, open the ADFS Management Console: Open the left hand navigation, expand relying parting trusts to find the display names: Now, run the Windows Powershell from the machine with ADFS installed. Claims-based authentication and security token expiration. The lifetime of a default security token for a claims-based authentication deployment using AD FS 2.0 is 60 minutes.
By default, Microsoft Dynamics CRM Server 2011 is configured to display the Authentication is Required dialog box 20 minutes before the token expires. In the Authentication is Required dialog box, if you click Cancel, the token expires as indicated. SharePoint 2010: How to Install and Configure ADFS 2.0 for SharePoint 2010 on Windows Server 2008 R2 (en-US) 1 Overview Active Directory Federation Services 2.0 helps IT enable users to collaborate across organizational boundaries and easily access applications on-premises and in the cloud, while maintaining application security.
Through a claims-based infrastructure, IT can enable a single sign-on experience for end-users to applications without requiring a separate account or password, whether applications are located in partner organizations or hosted in the cloud. 2 System requirements Supported operating systems: Windows Server 2008 Datacenter, Windows Server 2008 Enterprise, Windows Server 2008 R2, Windows Server 2008 R2 Datacenter, Windows Server 2008 R2 Enterprise, Windows Server 2008 R2 Foundation, Windows Server 2008 R2 Standard, Windows Server 2008 Service Pack 2, Windows Server 2008 Standard, Windows Small Business Server 2008 Premium, Windows Small Business Server 2008 Standard 3 Additional information 4 Download Center Microsoft ADFS Download.
How to setup Active Directory Federation Services « GAPTHEGURU. How to setup Active Directory Federation Services Part 1 Active directory federation service is Windows component which enables authentication of users on sites beyond its administrative domain.

Example for this type of authentication is when users from one site have to access resources on some external site such as resources in partner network (e.g. Partner web sites etc.) When resource on remote site needs authentication for accessing, but “local” credentials should to be used, that is point where Active Directory Federation Service (AD FS) takes place. Configuring SharePoint 2010 and ADFS v2 End to End - Share-n-dipity. In this post I’m going to do an end-to-end walk through on how to configure SharePoint 2010 and ADFS v2 together to use SAML claims authentication.
I’ll includes steps and PowerShell scripts to demonstrate and will try and bring all of the pieces together in one big posting. First a brief overview of the components involved and what we’re going to need to do. In this scenario ADFS v2 is our Identity Provider, also known as an IP-STS (Security Token Service). We need to configure ADFS with information about our Relying Party, or RP. In this case, SharePoint is our RP – it’s depending on ADFS to do the authentication and provide the claims. We’ll begin by creating the relying party in ADFS. Click on the Add Relying Party Trust link in the right pane to start the Add Relying Party Trust wizard.
Click the Start button to continue. Select the option to Enter data about the relying party manually, and then click the Next button. AD FS 2.0: How to Enable and Immediately Use AutoCertificateRollover. When the GUI Initial Configuration Wizard (ICW) of AD FS 2.0 has been executed, AutoCertificateRollover is automatically enabled by default and the token-signing and token-decrypting certificates are self-signed and maintained by the AD FS 2.0 service.
When the command line ICW of AD FS 2.0 has been executed, AutoCertificateRollover is either on or off depending on the syntax you provided at the command line. You can optionally turn off AutoCertificateRollover post-ICW by running the following from PowerShell: Jorge's Quest For Knowledge!