

Blog. Seasoned malware analysts/reversers/crackers move along – you already know this stuff Analyzing malware is always challenging as there are a few dozen if not hundreds different ways to detect the virtual environment plus other tools used by reversers during dynamic or in-depth analysis – most of these can be easily picked up by malware looking for process names, registry keys, or using one of the undocumented, or semi-documented bugs/features of VMs (usually snippets of code producing different results when executed on a real CPU vs. on a virtual CPU).
This short post describes a few ways how to hide VM (main focus on VMWare) and tools – by hiding their files, processes, services + associated with them registry keys/values. Changing VM settings It has has been described quite well here. Hiding Processes only If you need to hide the process only, you can use HideToolz available for a download from Fyyre’s web site. Bunnie's burrow. Once space is conquered, all that will be left is here. once time is conquered, all that will be left is now.

Do not lament on our parting, for between here and now, should we not meet again? An Introduction... Well, I finally did it. Index of /article/book. C++ Template Functions Explained with an Example Program. Let us assume that we are in the situation where we need to create a function that calculates the absolute value of a number.
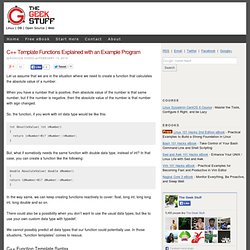
When you have a number that is positive, then absolute value of the number is that same number, but if the number is negative, then the absolute value of the number is that number with sign changed. So, the function, if you work with int data type would be like this: But, what if somebody needs the same function with double data type, instead of int? In that case, you can create a function like the following: In the way same, we can keep creating functions reactively to cover: float, long int, long long int, long double and so on. There could also be a possibility when you don’t want to use the usual data types, but like to use your own custom data type with typedef.
We cannot possibly predict all data types that our function could potentially use. C++ Function Template Syntax. DRKSpider - Web site crawler (site map generator) and link checker. DRKSpiderJava is a website crawler stand-alone tool for finding broken links and inspecting a website structure.
It builds a tree representing the hierarchical page distribution inside the site. Analyzing every link found, including those which point to another domain. Crawling is limited by external links, a maximum depth level given by the user, URL exclusion list, and the optional setting for obeying robots.txt site definition. DRKSpiderJava can keep site's content in memory (optional) for doing global searches in content. Once the spider finishes its work, the user can export a sitemap, a list of all links and the list of broken links. When a node in the tree is selected, DRKSpiderJava displays contextual information in the right panel. There are two advanced search dialogs: one for link searching and other for nodes. File transfer over sound card. Before I even start, a word of warning: Never try these programs with your headphones on.
THEY MAKE LOUD NOISES! It is possible to configure these programs to make noises way louder than you ever imagined your headphones could make. You can damage your hearing when playing with audio programming. Tinnitus isn't fun. This will be you if you don't take my warning seriously: Background and problem I have an old laptop laying about. Ah, I thought, and wrote a program that encoded data in sound. The basic protocol is trivial: For every character: For every bit: Send a short pulse if the bit is 1. This is nice and not very error prone. The crux isn't the signal generation (which is laughably trivial), it is the analysis on the receiving end; or rather dealing with the noise in the signal. So, the second approach would be to use a Fourier transform, to select the part of the spectrum where our signal resides (400 Hz is what I chose).
Flexamail - We make mail do more! Dynaweb. Download : Hacking-Lab.com. CPTE Firecat Demo - Mile2® - Cyber Security Training - Penetration Testing, Digital Forensics. LastActivityView reveals too much. - Page 4. Cyber Warfare. Prologue On April 10, 2013, a collective of politically motivated hacktivists announced a round of planned attacks called #OPUSA.
These attacks, slated to begin May 7, 2013, are to be launched against U.S. -based targets. #OPUSA is a follow-up to #OPISRAEL, which were a series of attacks carried out on April 7 against Israeli-based targets. Our goal here is to summarize and inform readers of resources, recommendations, network mitigations, and best practices that are available to prevent, mitigate, respond to, or dilute the effectiveness of these attacks.
Analysis If the attackers follow the same patterns as previously witnessed during the #OPISRAEL attacks, then targets can expect a mixture of attacks. Publicly announced attacks of this nature can have highly volatile credibility. Likely Avenues of Attack Using previous attacks as indicators, there are three major categories in which likely attacks can be placed. These mitigations will be discussed in more detail below. Conclusion.