

Marshaling Data with Platform Invoke. .NET Framework 4.6 and 4.5 To call functions exported from an unmanaged library, a .NET Framework application requires a function prototype in managed code that represents the unmanaged function.
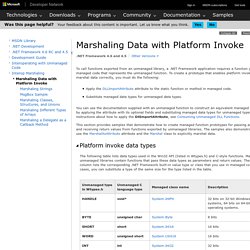
To create a prototype that enables platform invoke to marshal data correctly, you must do the following: The following table lists data types used in the Win32 API (listed in Wtypes.h) and C-style functions. Many unmanaged libraries contain functions that pass these data types as parameters and return values. The third column lists the corresponding .NET Framework built-in value type or class that you use in managed code.
The following code defines the library functions provided by Pinvoke.dll. Secure Salted Password Hashing - How to do it Properly. If you're a web developer, you've probably had to make a user account system.

The most important aspect of a user account system is how user passwords are protected. User account databases are hacked frequently, so you absolutely must do something to protect your users' passwords if your website is ever breached. The best way to protect passwords is to employ salted password hashing. This page will explain why it's done the way it is. There are a lot of conflicting ideas and misconceptions on how to do password hashing properly, probably due to the abundance of misinformation on the web.
IMPORTANT WARNING: If you are thinking of writing your own password hashing code, please don't!. If for some reason you missed that big red warning note, please go read it now. You may use the following links to jump to the different sections of this page. There is BSD-licensed password hashing source code at the bottom of this page: What is password hashing? Using the Reliability Features of the .NET Framework. ExecuteCodeWithGuaranteedCleanup erects a structured exception handling (SEH) handler within the CLR.
With that protection in place, the method calls back into the managed TryCode. If a stack overflow occurs within that code, the runtime catches it and ensures that enough stack space exists to run CleanupCode correctly. Of course, you still need to make sure that the back-out code itself does not cause a stack overflow (it should not make highly recursive calls or depend on code that requires a large or unknown amount of stack space). As an aside, note that C# doesn't currently allow you to specify a custom attribute on an anonymous method, so try not to use anonymous methods for your back-out code.
CLR Hosts and Escalation Policies When does an out-of-memory condition not result in an OutOfMemoryException? These types of policies aren't enough for all hosts. It's important to internalize how the CLR treats graceful thread aborts differently from rude thread aborts. Using Connection String Keywords with SQL Server Native Client. There are two ways OLE DB applications can initialize data source objects: IDBInitialize::Initialize IDataInitialize::GetDataSource In the first case, a provider string can be used to initialize connection properties by setting the property DBPROP_INIT_PROVIDERSTRING in the DBPROPSET_DBINIT property set.
In the second case, an initialization string can be passed to IDataInitialize::GetDataSource method to initialize connection properties. Both methods initialize the same OLE DB connection properties, but different sets of keywords are used. The set of keywords used by IDataInitialize::GetDataSource is at minimum the description of properties within the initialization property group. Any provider string setting that has a corresponding OLE DB property set to some default value or explicitly set to a value, the OLE DB property value will override the setting in the provider string. connection-string ::= empty-string[;] | attribute[;] | attribute; connection-string empty-string ::= .NET Delegates: A C# Bedtime Story.
The following is an excerpt from Windows Forms 2.0 Programming, Chris Sells & Michael Weinhardt, Addison-Wesley, 2006.

It's been updated from the original version for C# 2.0. Once upon a time, in a strange land south of here, there was a worker named Peter. He was a diligent worker who would readily accept requests from his boss. However, his boss was a mean, untrusting man who insisted on steady progress reports. Since Peter did not want his boss standing in his office looking over his shoulder, Peter promised to notify his boss whenever his work progressed. Interfaces Now Peter was a special person. Delegates Unfortunately, Peter was so busy talking his boss into implementing this interface that he didn't get around to notifying the Universe, but he knew he would soon.
How to create a COM object using VS 2008 and consume it from VB 6.0 client application: Part II. Download LINQPad. Using .NET: Avoid Common Performance Pitfalls for Speedier Apps. Reflection Dodge Common Performance Pitfalls to Craft Speedy Applications Joel Pobar.
Using the DropDownList and ListBox with ASP.NET MVC in C# for Visual Studio 2010.