

Company Salaries and Reviews. Jigsaw Business Contact Directory. Full Text Search. PeekYou. PicFog - Quick Image Search. People Find Tools at The Ultimates. Big Port DB. Cheat Sheet : All Cheat Sheets in one page. Security Advancements at the Monastery Blog Archive Whats in Your Folder: Security Cheat Sheets. On my desk is a folder containing all sort of cheat sheets relating to security, operating systems, and various web applications.
Many a times, these quick references have helped me remember particular options and information that are all too easily forgotten. These guides are also very useful in any training program, helping remind students of the essential information. Agile Hacking: A Homegrown Telnet-based Portscanner. Agile Hacking: A Homegrown Telnet-based Portscanner published: May 11th, 2008 So here is the scenario: the attacker has limited access to a box and he/she needs to perform a portscan from it.

However, he/she does not want to download any tools to the target system. There might be various reasons for not wanting to upload a portscanner to the box. Perhaps, the attacker wants to minimize the footprint. In my case, the reason why I had to come up with a solution to this problem is because I had to simulate an attack in which the attacker had gained access to a Internet-visible web server. I really didn’t want to download a tool such as nmap and then compile it. Anyway, my solution to this problem was to write a simple TCP portscanner in bash which glues around the telnet command which is present on most Unix/Linux distributions.
Command Line Kung Fu. Simple yet effective: Directory Bruteforcing. One thing you learn when you start a career pentesting is: Never assume anything.
In my experience hacks aren’t always elegant and elaborate. Sometimes something simple and effective is your avenue of penetration. The Grammar of WMIC. Whenever I’m Handler on Duty, I typically write up a little Windows command line tip to help security people and especially incident handlers analyze and understand their Windows systems better.
Most of thesearticlesfocus on very specific ways to use a given command, usually the very powerful WMIC command included in WinXP Pro, Win2003, and WinVista. But, you know, quite often, people tell me, “I like to use the WMIC command in this or that specific way, but I don’t really follow the underlying syntax of the thing.” Or, I hear, “I can never remember the overall flow of the WMIC command, so I just Google every time I need to use it to get the syntax for what I want to do.” Windows Command-Line Kung Fu with WMIC. A few weeks ago, uber-handler Tom "I-Write-Spyware" Liston and I were working on some tests of anti-spyware applications.

One of the experiments we performed was to take an ultra-infected box and run various anti-spyware tools to see if any of them could clean up the mess. The Windows machine we had was so thoroughly laced with spyware that IE couldn't run, Task Manager couldn't start, and the services control panel was kaput. Pretty much every GUI-based management and analysis tool on the box was hosed. Windows CMD Commands. Running a command on every mac. Command-Line Ninjitsu. Recently I wrote a blog post about using some basic native DOS commands to extract information from a target PC about user accounts, shares, software, networking information etc...
What I didn't cover in that post was WMIC (Windows Management Instrumentation Command). If that previous post was say the equivelent of DOS Kung Fu then WMIC to me is the Ninjitsu of DOS. WMIC, the other OTHER white meat. Hacking Without Tools: Windows - RST. I'm not an MCP, MCSE, MCTS, MCPD, MCITP, or MCA I'm not even very good at Minesweeper I'm a UNIX geek I love the command line How much you ask? This entire presentation was created by writing out HTML markup by hand in the Vim text editor. Pentesting Ninjitsu 1. Pentesting Ninjitsu 2 Infrastructure and Netcat without Netcat. [PenTester Scripting] Windows-scripting-COM-tricks. Advanced-Command-Exploitation. IPv4 subnetting reference. In the IPv4 address space certain address blocks are specially allocated or reserved for special uses such as loopback interfaces, private networks (RFC 1918),[1] and state-less autoconfiguration (Zeroconf, RFC 3927)[2] of interfaces.
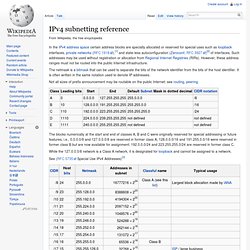
Such addresses may be used without registration or allocation from Regional Internet Registries (RIRs). However, these address ranges must not be routed into the public Internet infrastructure. The netmask is a bitmask that can be used to separate the bits of the network identifier from the bits of the host identifier. It is often written in the same notation used to denote IP addresses. Not all sizes of prefix announcement may be routable on the public Internet: see routing, peering. While the 127.0.0.0/8 network is a Class A network, it is designated for loopback and cannot be assigned to a network.
All the Best Linux Cheat Sheets. Shell Tips & Tricks (Beginner) Where learning Linux is easy. BashPitfalls - Greg's Wiki. Rubular: a Ruby regular expression editor. Last Updated Expert(s) TCP/UDP: Joe Touch; Eliot Lear, Allison Mankin, Markku Kojo, Kumiko Ono, Martin Stiemerling, Lars Eggert, Alexey Melnikov, Wes Eddy, Alexander Zimmermann, Brian Trammell, and Jana Iyengar SCTP: Allison Mankin and Michael Tuexen DCCP: Eddie Kohler and Yoshifumi Nishida Reference Note Service names and port numbers are used to distinguish between different services that run over transport protocols such as TCP, UDP, DCCP, and SCTP.

Useful commands for Windows administrators. Managing a Windows 2000 Active Directory with about 100 servers, over 1500 computers and 35 sites, the following commands often helped me answer questions or solve problems.

Most commands are "one-liners", but for some I had to make an exception and go to the right directory first. Password Exploitation Class. Password Exploitation Class This is a class we gave for the Kentuckiana ISSA on the the subject of password exploitation.
The Password Exploitation Class was put on as a charity event for the Matthew Shoemaker Memorial Fund ( ). The speakers were Dakykilla, Purehate_ and Irongeek. Lots of password finding and crack topics were covered. Default Passwords Database. MS SQL Server Password Recovery. For database admins, it is not a nightmare to handle with lost sql server password, which can be easily retrieved from application source code or just reset it in Enterprise Manager. But for a penetration tester, he should know where the passwords store, how to dump hashes, and crack them to gain more information. And it is necessary to audit the strength of sql server passwords, because weak sql passwords could cause system command execution remotely by a malicious hacker, compromising the application security. David Litchfiled has written a good paper about cracking sql server passwords in 2002. You should read it to understand the mechanism of hashes, and after that, practice the following instructions and tools. 1.
Networking Services - Medusa. JoMo-Kun / jmk "AT" foofus "DOT" net The SMBNT module tests accounts against the Microsoft netbios-ssn (TCP/139) and microsoft-ds (TCP/445) services. Besides testing normal passwords, this module allows Medusa to directly test NTLM hashes against a Windows host. LM/NTLM Challenge / Response Authentication - Foofus.Net Security Stuff.
This documentation was written for John The Ripper and is included in the available jumbo patches. Wordlist Downloads. Password Storage Locations For Popular Windows Applications. Online Hash Crack MD5 / LM / NTLM / SHA1 / MySQL - Passwords recovery - Reverse hash lookup Online - Hash Calculator. Requested MD5 Hash queue. Default Password List. Electric Alchemy: Cracking Passwords in the Cloud: Breaking PGP on EC2 with EDPR. UPDATE 15 Nov 2010: Amazon announces "Cluster GPU Instances", again radically changing the economics of using EC2 for password cracking. "Crack Me If You Can" - DEFCON 2011. Packet Storm Word Lists. Passwords - SkullSecurity. Password dictionaries. Index of /passwd/passwords.