

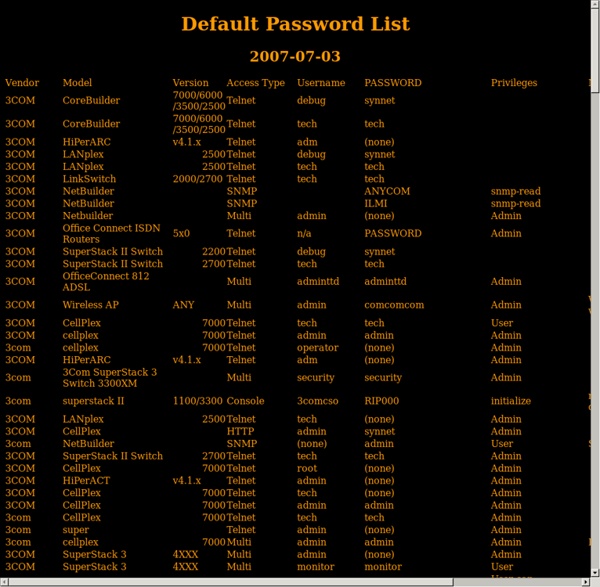
http://www.phenoelit-us.org/dpl/dpl.html
Latte Art Printing Machine – how to build one! « Oleksiy Pikalo Invents Latte Art Printing Machine – how to build one! Note: Due to the overwhelming response, I have decided to form a company OnLatte, Inc. Our new address is Note: if you are willing to register, you can help me to promote this idea on MyStarbucksIdea site Long time ago, I saw a great video about “Latte Art”, and figured that I absolutely must build a machine capable of printing the most beautiful art on top of my latte. So I bought a used x-y flatbed plotter (Philips 8155) on eBay and a great book by Matt Gilliland, titled “Inkjet Applications”.
Electric Alchemy: Cracking Passwords in the Cloud: Breaking PGP on EC2 with EDPR UPDATE 15 Nov 2010: Amazon announces "Cluster GPU Instances", again radically changing the economics of using EC2 for password cracking. We've had some questions about whether or not we are going to re-run our analysis using the EC2 GPU Instances. We may do so, but in the meantime have a look at stacksmashing.net. The have already got some numbers posted for cracking SHA1 on EC2/GPU. UPDATE 21 Dec 2009: Amazon announces "spot instances", radically changing the economics of using EC2 for password cracking. 10 OS X Pranks That'll Get You Beat Up Posted 07/14/2009 at 5:08pm | by Arvind Srinivasan If you're thinking to yourself, "Wait, it's not April." Don't worry, we know exactly what we're doing here. Everyone expects pranks in April and the days leading up. No one expects a prank in the middle of summer.
Foofus Networking Services - Medusa JoMo-Kun / jmk "AT" foofus "DOT" net The SMBNT module tests accounts against the Microsoft netbios-ssn (TCP/139) and microsoft-ds (TCP/445) services. Besides testing normal passwords, this module allows Medusa to directly test NTLM hashes against a Windows host. This may be useful for an auditor who has aquired a sam._ or pwdump file and would like to quickly determine which are valid entries. Several "-m 'METHOD:VALUE'" options can be used with this module. Arduino My older son recently started school and needed his own desk for doing homework. I wanted to make something nicer than a simple tabletop with legs, and realized that I could also build in a bit of fun for when the homework is finished. Both my boys and I still had space travel on our minds from our summer trip to Kennedy Space Center. For this desk project, I decided to go with a NASA theme. I researched the Apollo Program as well as NASA's Mission Control Center, and designed my own console roughly based on those.
LM/NTLM Challenge / Response Authentication - Foofus.Net Security Stuff This documentation was written for John The Ripper and is included in the available jumbo patches. LM/NTLM Challenge / Response Authentication JoMo-Kun (jmk at foofus dot net) ~ 2010 Microsoft Windows-based systems employ a challenge-response authentication protocol as one of the mechanisms used to validate requests for remote file access. The configured/negotiated authentication type, or level, determines how the system will perform authentication attempts on behalf of users for either incoming or outbound requests. These requests may be due to a user initiating a logon session with a remote host or, in some cases, transparently by an application they are running. In many cases, these exchanges can be replayed, manipulated or captured for offline password cracking.
Teagueduino: Learn to Make by Teague Teagueduino is an open source electronic board and interface that allows you to realize creative ideas without soldering or knowing how to code, while teaching you the ropes of programming and embedded development (like arduino). Teagueduino is designed to help you discover your inner techno-geek and embrace the awesomeness of making things in realtime — even if you’ve only ever programmed your VCR. Teagueduino makes making things really simple. Want to build a light-controlled alarm clock? A harmonic music generator or a light that changes color based on temperature?
Password Exploitation Class Password Exploitation Class This is a class we gave for the Kentuckiana ISSA on the the subject of password exploitation. The Password Exploitation Class was put on as a charity event for the Matthew Shoemaker Memorial Fund ( ). The speakers were Dakykilla, Purehate_ and Irongeek. Lots of password finding and crack topics were covered. ma connection ? NOTE: Due to excessive queries, page processing has been limited to 10 per minute. Please contact us for bulk data access or try out our API. Do not use this data as a blocklist. To lookup several IP addresses at the same time, or to just copy/paste a section of a log, use our "Color My Logs" feature. General Information Note: We update the data once an hour.
How To Become A Hacker - StumbleUpon Copyright © 2001 Eric S. Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker?". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one. A lot of hackers now consider it definitive, and I suppose that means it is. Still, I don't claim to be the exclusive authority on this topic; if you don't like what you read here, write your own.
Sinbad Security Blog: MS SQL Server Password Recovery For database admins, it is not a nightmare to handle with lost sql server password, which can be easily retrieved from application source code or just reset it in Enterprise Manager. But for a penetration tester, he should know where the passwords store, how to dump hashes, and crack them to gain more information. And it is necessary to audit the strength of sql server passwords, because weak sql passwords could cause system command execution remotely by a malicious hacker, compromising the application security.
Free Fonts How to install fonts About Icon fonts About Webfonts Submit free fonts Love our site? Tell a friend Name