

Internet Control Message Protocol. Un article de Wikipédia, l'encyclopédie libre.
Pour les articles homonymes, voir ICMP. Internet Control Message Protocol est l'un des protocoles fondamentaux constituant la Suite des protocoles Internet. Il est utilisé pour véhiculer des messages de contrôle et d'erreur pour cette suite de protocoles, par exemple lorsqu'un service ou un hôte est inaccessible. ICMP se situe au même niveau que le protocole IP bien qu'il ne fournisse pas les primitives de service habituellement associées à un protocole de couche réseau. Son utilisation est habituellement transparente du point de vue des applications et des utilisateurs présents sur le réseau. Cet article traite d'ICMP version 4 qui accompagne IPv4. Présentation[modifier | modifier le code] Prevent hacker probing: Block bad ICMP messages. The ICMP protocol facilitates the use of important administrator utilities such as ping and traceroute, but it can also be manipulated by hackers to get a snapshot of your network.
Learn what ICMP traffic to filter and what to allow. This article originally appeared in the Security Solutions e-newsletter. Although most network administrators do a fairly good job of filtering TCP and UDP traffic, many forget to filter ICMP traffic. ICMP traffic is necessary for troubleshooting TCP/IP and for managing its flow and proper function. However, ICMP is also dangerous. Like TCP and UDP, ICMP is a protocol within TCP/IP that runs over IP. Bad ICMPSome ICMP message types are necessary for network administration. ICMP packet magnification (or ICMP Smurf): An attacker sends forged ICMP echo packets to vulnerable networks' broadcast addresses. PingWhen you ping a destination network address, you're sending an ICMP packet with message type 8 (Echo) code 0 (Echo--Request) to that address. Icmp. Le Monde des Réseaux. PING - Le Tutorial Facile. Stats Nov 2010 82'909 Visiteurs 146'476 Pages196 paysStatistiques completes Aidez-nous à traduire nos tutoriaux!
Réseau Ping Dern. mise à jour: 22-09-2010 If you like our tutorials, don't hesitate to support us and visit our sponsors! Ping Tutorial: 15 Effective Ping Command Examples. As you already know, ping command is used to find out whether the peer host/gateway is reachable.
If you are thinking ping is such a simple command and why do I need 15 examples, you should read the rest of the article. Ping command provides lot more options than what you might already know. Ping Example 1. Increase or Decrease the Time Interval Between Packets By default ping waits for 1 second before sending the next packet. Increase Ping Time Interval Example: Wait for 5 seconds before sending the next packet.
Ping de la mort. Un article de Wikipédia, l'encyclopédie libre.
Cette faille a été exploitable sur différents systèmes d'exploitation, comme UNIX, Linux, Mac OS ou encore Microsoft Windows, jusque dans les années 1997-1998[1]. Articles connexes[modifier | modifier le code] Portail de la sécurité informatique. Ping Flooding. One of the oldest network attacks around.
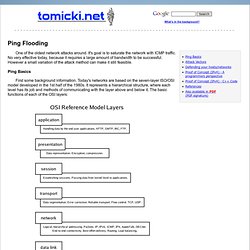
It's goal is to saturate the network with ICMP traffic. No very effective today, because it requires a large amount of bandwidth to be successful. However a small variation of the attack method can make it still feasible. Ping Basics First some background information. The mechanism that the ping utility is based on is part of the Internet Control Message Protocol (ICMP). Attack Vectors ICMP can be abused in the following scheme: the attacker sends echo request packets with spoofed source IP addresses, and ties up the victim into spending all his time on replying to non-existent senders.
The goal of the of this attack is to saturate the victims network with ICMP traffic and waste all his CPU time on replying to our spoofed packets. There is however a way to make this attack feasible even in today's environment. Defending your hosts/networks Protecting yourself from becoming a victim in the attack is a bit more complicated. Send our datagrams: Its335y13s2l06-denial-of-service-attacks. Tutorial: How to DoS Attack (Ping flooding) Introduction The effects of a ping flood attack I got all excited when I learned to ping flood (Denial of Service) someone for the first time.
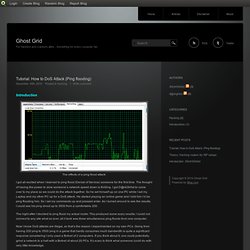
The thought of having the power to slow someone’s network speed down is thrilling. I got D@rkGh0st to come over to my place so we could do the attack together. So he set himself up on one PC while I set my Laptop and my other PC up for a DoS attack. The night after I decided to ping flood my actual router. Now I know DoS attacks are illegal, so that’s the reason I experimented on my own PCs. Moving along. What is a DoS attack? A DoS (Denial of Service) is an attempt to make a computer’s resources unavailable to its user. Usually an attacker does not use his/her own computer. Rfc2827. BCP38.