

Servers for Hackers. We use SSH to log into our servers, but it actually has a lot of neat tricks it can help us with as well!
We'll cover some of them here. Logging in Of course, we use SSH to login: $ ssh user@hostname And, if needed, we can specify a different port: $ ssh -p 2222 user@hostname Sometimes, if we have a lot of SSH keys in our ~/.ssh directory, we'll often find that SSHing into servers with the intent of using a password results in a "too many authentication attempts" error. . $ ssh -o "PubkeyAuthentication no" username@hostname If you use AWS, and in other cases, you might get a PEM file to use as an identity.
Invoker - A Process Manager. VisualOps - Ensure your app always runs as you designed. Collection of Less Commonly Used UNIX Commands. Skwp/dotfiles. How to: Deny Hosts Using Nginx. I was noticing my nginx log file fill up with requests for a site who had misconfigured their DNS.
Normally I wouldn’t worry about it, but it became quickly evident that the domain was used for an image server for a parent site. There were thousands of RPS that I really didn’t need. All I did was add the following expression to my nginx.conf file. Now if you look at the code, you may be thinking “But Jared, what is a 444 error? That is totally not valid bro.” “Furthermore, nonstandard code 444 closes the connection without sending any headers.” So basically, my expression above, in plain english, is saying. “If you are not making a request using the valid hostname of my server, then I’m just going to close the connection and return you nothing. nada. zip.” For the record, I got a lot of value out of this article over @ calomel.org, but the site seems to have issues so I copy/pasted their nginx.conf file here for historical purposes.
Communicate personally with every single customer. Blocking Image Hotlinking, Leeching and Evil Sploggers with IIS Url Rewrite. Top 20 Nginx WebServer Best Security Practices. Nginx is a lightweight, high performance web server/reverse proxy and e-mail (IMAP/POP3) proxy.
It runs on UNIX, GNU/Linux, BSD variants, Mac OS X, Solaris, and Microsoft Windows. According to Netcraft, 6% of all domains on the Internet use nginx webserver. Nginx is one of a handful of servers written to address the C10K problem. Unlike traditional servers, Nginx doesn't rely on threads to handle requests. Instead it uses a much more scalable event-driven (asynchronous) architecture.
Optimizing Nginx for High Traffic Loads. I have previously talked about some of the most common nginx questions; not surprisingly, one such question is how to optimize nginx for high performance.

This is not really overly surprising since most of new nginx users are migrating over from Apache and thus are used to having to tune settings and perform voodoo magic to ensure that their servers perform as best as possible. Well I’ve got some bad news for you, you can’t really optimize nginx very much. There’s no magic settings that will reduce your load by half or make PHP run twice as fast. Thankfully, the good news is that nginx doesn’t require any tuning because it is already optimized out of the box. Utrace - IP-Adressen und Domainnamen lokalisieren. Solution for remote control, remote access, home office and TeamViewer features.
Easy Drag & Drop Project Tracking. Taking Some Pain Out Of Python Logging — Hynek Schlawack. Even the best of us hate logging in Python sometimes.

And while a lot of its problems are actually just bad docs and terrible defaults in the past, there is some pain that can be avoided. One of the big problems with logging in general is that every class and function reek of NIH in the name of cross-platform. And to make it even more fun, there are several ways to do it: standard library, Twisted, Logbook… For example to get useful log rotation by day (whoever came up with rotating by size may be a good idea‽), you'd go for TimedRotatingFileHandler in stdlib, but in Twisted everything works slightly differently.
Introducing Chronos: A Replacement for Cron. By Florian Leibert, Harry Shoff, & Andy Kramolisch Chronos is our replacement for cron.
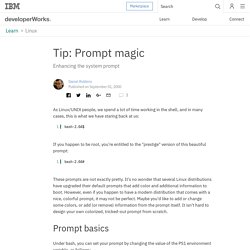
It is a distributed and fault-tolerant scheduler which runs on top of Mesos. It’s a framework and supports custom mesos executors as well as the default command executor. Thus by default, Chronos executes SH (on most systems BASH) scripts. Chronos can be used to interact with systems such as Hadoop (incl. M/Monit screens. Tip: Prompt magic. Enhancing the system prompt As Linux/UNIX people, we spend a lot of time working in the shell, and in many cases, this is what we have staring back at us: If you happen to be root, you're entitled to the "prestige" version of this beautiful prompt: These prompts are not exactly pretty.
Todd Werth » Bashmarks – Bookmarking for the command-line. Bashmarks is a simple set of bash functions that allows you to bookmark folders in the command-line.
Install Get bashmarks.sh here: github repositoryPlace bashmarks.sh somewhere such as ~/binSource it in your .bashrc file (or other bash startup file):source ~/bin/bashmarks.sh Use To bookmark a folder, simply go to that folder, then bookmark it like so: Xip.io: wildcard DNS for everyone. Google Launches “Help For Hacked Sites” To Teach Site Owners How To Recover Their Hacked Sites. How to SSH without password. This simple tutorial explains how to SSH to a remote machine without typing your password.
You can use this technique if you find yourself logging in to the same machine frequently and find typing your password tedious.