

IOS Application Security Part 25 - Secure Coding Practices for IOS Development. In this article, we will look at some of the best practices an IOS developer should follow in order to make sure that their application is not easily exploitable by hackers.
Local Data Storage It is extremely important for developers to know what kind of data they should be storing locally in their application. Frankly speaking, no data is secure when stored locally in the application. In part 20 of this series, we have looked at Local Data Storage in great detail. Important data like Passwords, Session ID’s etc should never be stored locally on the device. Transport Layer Security Do not allow self signed certificates to be used when releasing the application. Use Encryption Encrypt important files before saving them locally. Add checks to prevent Runtime Analysis Remember that with a copy of your application binary, a hacker is in complete control. Some other minor things Want to learn more?? IOS Application Security Part 21 - ARM and GDB Basics. All the IOS devices released uptil now are based on the ARM architecture.
All the Objective-C code that we write while developing IOS applications is first converted into ARM assembly before being converted to machine code (1s and 0s). With good understanding of the ARM assembly language and with good knowledge of debugging using GDB, it is possible for a hacker to decipher the Objective-C code during runtime and even modify it.
For this article, we will be using a sample application GDB-Demo from my github account. Make sure to install and run it on your IOS device. If you don’t have a registered developer account to run this on your device, you can follow the instructions mentioned here. Now let’s SSH into the device. Now lets start GDB and ask GDB to hook into our application as soon as it is started. IOS Application Security Part 22 - Runtime Analysis and Manipulation using GDB. In this article, we will look at how we can use GDB to perform runtime analysis of IOS applications.
In the previous articles, we have looked at how we can use Cycript to analyze and manipulate the runtime behaviour of IOS applications. We have learnt how we can perform method swizzling and have our own methods being called instead of the original implementations. So why we do need GDB ? Well, what Cycript doesn’t allow us to do yet is set breakpoints and alter the values of variables and registers after a particular instruction.
With GDB, we can dive deep into the application, observe the low level assembly instructions, manipulate the values in the registers and hence change the application flow completely. For this demo, you can download the sample application GDB-Demo from my github account. Once the application is installed on your device, ssh into it. Then start the GDB-Demo application on your device. Now, lets enter any username/password combination and press Login. IOS Application Security Part 23 - Defending against runtime analysis and manipulation. In the previous articles, we have looked at how we can use debuggers and tools like Cycript to do runtime analysis and manipulation of IOS Applications.
We have looked at how we can modify the actual implementation of a method during runtime by changing the values in the registers using GDB, and also looked at how we can completely swizzle method implementations using tools like Cycript. With tools like Cycript and GDB in his arsenal and with a copy of your application’s binary, the attacker is is complete control. However, there are certain techniques a developer can use to make the job of the hacker much more difficult. IOS Application Security Part 16 - Runtime Analysis of IOS Applications using iNalyzer.
In the previous article, we looked at how we can perform static analysis of IOS Applications using iNalyzer.
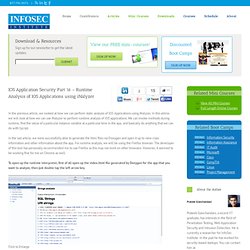
In this article, we will look at how we can use iNalyzer to perform runtime analysis of IOS applications. We can invoke methods during runtime, find the value of a particular instance variable at a particular time in the app, and basically do anything that we can do with Cycript. In the last article, we were successfully able to generate the html files via Doxygen and open it up to view class information and other information about the app. IOS Application Security Part 17 - Black-box assessment of IOS Applications using Introspy. In this article, we will look at how we can use Introspy for Black-box assessment of IOS applications.
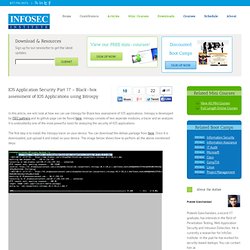
Introspy is developed by ISEC partners and its github page can be found here. Introspy consists of two seperate modules, a tracer and an analyzer. It is undoubtedly one of the most powerful tools for analyzing the security of IOS applications. IOS Application Security Part 18 - Detecting custom signatures with Introspy. In the previous article, we looked at how we can use Introspy for Black-box assessment of IOS applications.
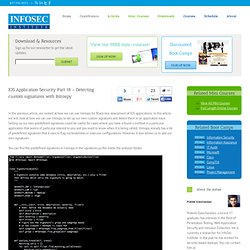
In this article, we will look at how we can use Introspy to set up our own custom signatures and detect them in an application trace. Setting up our own predefined signatures could be useful for cases where you have a found a method in a particular application that seems of particular interest to you and you want to know when it is being called. Introspy already has a list of predefined signatures that it uses to flag vulnerabilities or insecure configurations.
However, it also allows us to add our own signatures. IOS Application Security Part 19 - Programmatical Usage of Introspy. In this article, we will look at how we can Introspy as a python module in our scripts.
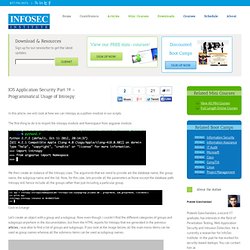
The first thing to do is to import the introspy module and Namespace from argparse module. We then create an instance of the Introspy class. The arguments that we need to provide are the database name, the group name, the subgroup name and the list. Now, for this case, lets provide all the parameters as None except the database path. Introspy will hence include all the groups rather than just including a particular group. IOS Application Security Part 20 - Local Data Storage (NSUserDefaults, CoreData, Sqlite, Plist files) In this article, we will look at the different ways in which applicatons can store data locally on the device and look at how secure these methods are.
We will be performing some of these demonstrations in a sample app that you can download from my github account. For the CoreData example, you can download the sample app from here. IOS Application Security Part 11 - Analyzing Network Traffic over HTTP/HTTPS. In the previous article, we looked at IOS filesystem and forensics.
In this article, we will be looking at how we can analyze the network traffic flowing across an IOS device. Analyzing the network traffic for an application could be helpful in many ways. IOS Application Security Part 12 - Dumping Keychain Data. In the previous article, we looked at the different ways in which we could analyze the network traffic and the api calls being made through an IOS application. In this article, we will look at how we can dump the contents of the Keychain from an IOS device. Keychain Basics According to Apple, a Keychain in an IOS device is a secure storage container that can be used to store sensitive infromation like usernames, passwords,network passwords, authentication tokens for different applications.
Apple itself uses the Keychain to store Wi-fi network passwords, VPN credentials etc. It’s a sqlite database file located at /private/var/Keychains/keychain-2.db and all the data stored in it is encrypted. It is also possible to share keychain data between applications through keychain access groups. KeychainItemWrapper *wrapper = [[KeychainItemWrapper alloc] initWithIdentifier:@”Password” accessGroup:nil]; IOS Application Security Part 13 - Booting a custom Ramdisk using Sogeti Data Protection tools. In the previous article, we looked at how we can use Keychain-Dumper and Snoop-it to analyze and dump the contents of the Keychain from an IOS device. In this article, we will look at how we can boot a non-jailbroken device using a custom ramdisk and analyze the contents of the device. So what is the need of booting a device using a custom ramdisk ? Imagine a scenario where you only have temporary access to a device and you can’t jailbreak it.
You just have access to the device for say like 30 minutes. In that time, you can boot the device using a custom ramdisk, brute force the passcode, and dump all the information for later analysis. IOS Application Security Part 14 - Gathering information using Sogeti Data Protection tools. In the previous article, we looked at how we can boot a device using a custom ramdisk using Sogeti Data protection tools. In this article, we will look at how we can use some of their tools to gather information from the device like fetching the keychain information, dumping the entire filesystem or even bruteforcing the passcode. Until the previous article, we had successfully set up a connection to the device using usbmux, ssh’ed into the device and had mounted the partitions.
Here is what these partitions contain. Now we are free to navigate inside these partitions and do whatever we want. IOS Application Security Part 15 - Static Analysis of IOS Applications using iNalyzer. In the previous article, we looked at how we can use Sogeti Data protection tools to boot an iDevice using a custom ramdisk with the help of a bootrom exploit. In this article, we will look at a tool named iNalyzer than we can use for black box assessment of IOS applications. iNalyzer allows us to view the class information, perform runtime analysis and many other things.
Basically it automates the efforts of decrypting the application, dumping class information and presents it in a much more presentable way. We can also hook into a running process just like Cycript and invoke methods during runtime. iNalyzer is developed and maintained by AppSec Labs and its offical page can be found here. iNalyzer is also made available open source and its github page can be found here. iNalyzer require some dependencies to be installed before use.
Please make sure to install Graphviz and Doxygen as iNalyzer won’t function without these. Then go to Search and search for iNalyzer. Run . Conclusion. IOS Application Security Part 6 - New Security Features in IOS 7. As we all know, Apple recently introducted its new version of IOS at WWDC 2013 with a completely redesinged User Interface.
If you haven’t seen it yet, check out this video from WWDC 2013. This article will be a small deviation from the other parts in this series. In this articles, we will discuss about the latest security features introduced in IOS 7. Getting IOS 7. To get IOS 7 beta, you have to be a registered apple developer. Here are some of the new security features introduced with IOS 7. Activation Lock Previously, if some user had lost their iPhone, they could use the “Find my Iphone” app to track down their phone using GPS. To Check this feature Go To Settings, then General, then scroll to the bottom and you will see a Reset button. If you tap on this button and then tap on Erase All Contents and Settings, you will see a popup which asks for your Apple Id password.
This is a very handy feature and prevents the thief from resetting your iPhone’s settings and data. IOS Application Security Part 7 - Installing and Running Custom Applications on Device without a registered developer account. Usually, to test apps on a device, you need to be a registered developer which costs about $99/year. For people who want to learn IOS Application security, it is very important that they should be able to run applications on device so that they can perfom tests on them.
For some people who do not want to publish any apps on the app store, it may not be worth it to pay the $99/year fees. IOS Application Security Part 8 - Method Swizzling using Cycript. IOS Application Security Part 9 - Analyzing Security of IOS Applications using Snoop-it. IOS Application Security Part 10 - IOS Filesystem and Forensics. IOS Application security Part 1 - Setting up a mobile pentesting platform. Introduction. IOS Application security Part 2 - Getting class information of IOS apps. Introduction Have you ever checked out an IOS app and thought it was cool, and wondered if you could find some information about the source code of the app, the third-party libraries it uses, or how the code is designed internally?
Have you ever wondered if it was possible to dump all the images, plist files used in any app either preinstalled on your device or downloaded from the App store? If the answer is Yes, then you have come to the right place. In this article, we will look at how we can analyze any preinstalled app on your device or any other app downloaded from App store and discover things about the source code of the app like the classes that it uses, the names of the view controllers it uses, the internal libraries, and even intricate details like the variables and methods names used in any particular class or view controller. IOS Application security Part 3 - Understanding the Objective-C Runtime. Introduction. iOS Application Security Part 4 – Runtime Analysis Using Cycript (Yahoo Weather App) Introduction. IOS Application security Part 5 - Advanced Runtime analysis and manipulation using Cycript (Yahoo Weather App)
Introduction In the previous article, we learnt how to setup Cycript on your idevice, hook into a running process and obtain information about its properties in runtime.