

Get Detailed Information About Particular IP address Connections Using netstat Command. Netstat command and shell pipe feature can be used to dig out more information about particular IP address connection.
You can find out total established connections, closing connection, SYN and FIN bits and much more. Fritzing, the Hot New Electronics Designer for Real People. Fritzing is the sophisticated new electronics application with the funny name.
It is a powerful tool for making schematics, prototyping circuits, and designing printed circuit boards. This is the best time to get into electronics because we have an abundance of high-quality hardware for cheap and great software for free. Arduino, Beagleboard, and Raspberry Pi give us hundreds of inexpensive hardware components to play with. On the software side check out the new Fritzing project. Creating an Android Project. An Android project contains all the files that comprise the source code for your Android app.
This lesson shows how to create a new project either using Android Studio or using the SDK tools from a command line. Note: You should already have the Android SDK installed, and if you're using Android Studio, you should also have Android Studio installed. If you don't have these, follow the guide to Installing the Android SDK before you start this lesson. Browse like Bond: Use any computer without leaving a trace with Tails. If James Bond logs on to a computer, he doesn't want to leave a bunch of files, cookies, or his IP address out there for someone to find.
It might seem extreme, but sometimes it's a good idea to take the same precautions yourself. In this post, we'll walk through how to use a USB stick or DVD to anonymize, encrypt and hide everything you do on a computer no matter where you are. When we say "browse without leaving a trace", we truly mean it. Using the Linux-based, live-boot operating system Tails (The Amnesiac Incognito Live System), you can use any computer anywhere without anyone knowing you were ever on it. Tails is a portable operating system with all the security bells and whistles you'll ever need already installed on it. The Software Packed Directly into TailsOnce you create your Tails boot disc, you'll be ready to reboot your computer into an encrypted and private operating system preloaded with all the software you'll need to browse the Web, email, IM, and edit documents. SSH Tunneling. What is SSH ?
SSH stands for “Secure Shell”, It used to create a secure connection between two computers. SSH supplies a command line interface for remote administration/management of Linux based systems or even CISCO routers, It allows us to securely perform various maintenance tasks and more…basically we can think of it as “secured telnet”. SSH communication consists of a SSH Server and a SSH Client. Exploits Database by Offensive Security.
Index of /article/book. Wi-Fi Home Networking - Wireless LAN WLAN Technology. Learn how to set up and maintain wireless home networks (or local area business networks) using standard "Wi-Fi" networking technology and products like wireless access points, routers, and adapters.
How to Build a Wi-Fi Home Network TutorialThis in-depth article teaches you how to build a wireless home network (WLAN). Learn the terminology and technology basics, design a layout that meets your needs, choose the appropriate gear, then finally install and configure the pieces. Gallery of Home Networking DiagramsThis collection of home network diagrams covers both wireless, Ethernet and hybrid layouts. Network layouts including routers, access points, printers and entertainment consoles are described. How to Build Your Own Wireless Home Network. Welcome to Wireless Home Network Basics - the guide to setting up a basic Wireless LAN at home plus some security to keep it in place...

This guide is meant for the intermediate computer user and therefore kept to a bare minimum in terms of complicated jargon/lingo; and is meant to be easily understood and straight to the point. Here is the table of contents: Introduction A Wireless Network, or Wireless LAN, or WLAN for short, is basically a computer network which links computers in an area. Normally, people use cables to connect computers together, however after wireless technology became popular, WLANs now use radio waves to transmit data between computers. You Have Downloaded - We show what you downloaded. Untitled. [EPIC]Using brute force (password cracker) to hack world of warcraft account guide! Hacking Facebook accounts on LAN – Part 2 « hackhaven. Hey!
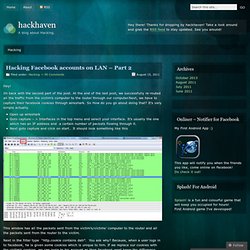
Im back with the second part of the post. At the end of the last post, we successfully re-routed all the traffic from the victim’s computer to the router through our computer.Next, we have to capture their facebook cookies through wireshark. So How do you go about doing that? It’s very simple actually. Top 15 Security/Hacking Tools and Utilities. Eeemo.net. Create Your Own Smartphone App With Infinite Monkeys – No Coding Knowledge Required. It would be great if we all had the time, skills, and patience to learn computer coding, especially since technology pervades so many areas of our life.
But thankfully, there are applications and web developers out there who provide ways for the rest of us to produce apps with little or no coding skills. Back in June, I reviewed one such web application called Buzztouch, which is designed to allow anyone to create their own smartphone application. Now a similar program has just been released called Infinite Monkeys, a web-based tool geared toward niche communities who want to share content on the iPhone and Android platforms.
Infinite Monkeys is not as polished theme wise as Buzztouch, but unlike the latter, Infinite Monkeys, says the developers, “Is completely web-based, and works on any computer or tablet device. How Computers Boot Up. The previous post described motherboards and the memory map in Intel computers to set the scene for the initial phases of boot.

Booting is an involved, hacky, multi-stage affair – fun stuff. Here’s an outline of the process: Q: How do I encrypt file transfers with dd and netcat? A: This question came to us in response to the article Backup Files and Partitions with dd and netcat. Encrypting these files transfers is quite simple. As in the previous article, we will setup the server to listen on port 9999 and redirect output to “backup.file” Make Gnome Shell Look Like Android 4.0 With Ice Cream Shell Theme [Linux] Ever since the release of Gnome Shell for Linux, there has been quite a handful of different themes that have been coming out for this new desktop environment. However, I haven’t gone over any of them recently, which is a pity considering how pretty some of them really are.
Today, we’ll be covering a very nice theme that should easily find a special place in the heart of Androidlovers. Information Security Blog » Tutorials. PenTest Security Tools Tutorials Code Publish rss feed. Hardware USB - OpenTom. USB in general. World Lecture Hall. How to Crack a Wi-Fi Network's WPA Password with Reaver. The 5 Best Websites To Learn Python Programming. Over the past decade, the Python programming language has exploded in popularity amongst programmers in all areas of coding.
From web developers to video game designers to in-house tool creators, many people have fallen in love with the language. Why? Because it’s easy to learn, easy to use, and very powerful. Try Python: 1. Python Tutorial Part 1. Index of defcon-15-video - Good.net. Fake Name Generator. #3038363. How to gain access to system account the most powerful account in Windows. « Alien Eyes. There is an account in Microsoft Windows that is more powerful than the Administrator account in Windows Operating Systems. Index of / The Evil Access Point! Batch virus maker tool to create your own viruses. Batch virus maker tool is the one which can create batch viruses.The properties and behaviour of the virus can be set by yourself.Batch programs are essentially sequences of DOS commands that 'type themselves' when the batch file is run.Batch files consist of control elements, internal DOS commands and external commands or programs. The Open Organisation Of Lockpickers.
Know the Trade – Your IT Security Information Portal CISSP/CEH/CISA/Hacker and Penetration Testing Specialist. How to hide files in JPEG pictures. Hacking the Xbox. Hands-On UNIX System Administration — Spring 2011. Porting Android to x86. A history of hacking. A Website Dedicated to Computer Professionals. 5 Fun things To Do on School Computers - Pahgawks Animations - StumbleUpon. November 26th, 2010. Live USB Install Puts Linux On Your Thumb Drive With Ease. Boot one of over a hundred Linux distros from a USB disk. With Live USB, software you can run on both Windows and Linux computers, it only takes a couple of clicks to make your USB disk a bootable Linux disk.
12 Easy Exploits to Raise Thief Skills in Skyrim « Null Byte - StumbleUpon. UNetbootin - Homepage and Downloads. Project Euler. 2 Websites & 2 Applications That Can Help When Learning Java Programming. The Rubik's Cube Solution. The Best System Tweaker for Linux.