

7 lines of code, 3 minutes: Implement a programming language. A small (yet Turing-equivalent) language The easiest programming language to implement is a minimalist, higher-order functional programming language known as the lambda calculus.

The lambda calculus actually lives at the core of all the major functional languages--Haskell, Scheme and ML--but it also lives inside JavaScript, Python and Ruby. It's even hiding inside Java, if you know where to find it. A brief history Alonzo Church developed the lambda calculus in 1929. Back then, it wasn't called a programming language because there were no computers; there wasn't anything to "program. " It was really just a mathematical notation for reasoning about functions. Fortunately, Alonzo Church had a Ph.D. student named Alan Turing. Alan Turing defined the Turing machine, which became the first accepted definition of a general-purpose computer. How Computers Boot Up. The previous post described motherboards and the memory map in Intel computers to set the scene for the initial phases of boot.

Booting is an involved, hacky, multi-stage affair – fun stuff. Server Hardening Checklists - Windows 2003 Server Hardening Checklist. The hardening checklists are based on the comprehensive checklists produced by CIS.
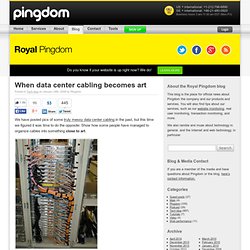
The Information Security Office has distilled the CIS lists down to the most critical steps for your systems, with a particular focus on configuration issues that are unique to the computing environment at The University of Texas at Austin. How to use the checklist Print the checklist and check off each item you complete to ensure that you cover the critical steps for securing your server. The Information Security Office uses this checklist during risk assessments as part of the process to verify that servers are secure. When data center cabling becomes art. Posted in Tech blog on January 24th, 2008 by Pingdom We have posted pics of some truly messy data center cabling in the past, but this time we figured it was time to do the opposite: Show how some people have managed to organize cables into something close to art.
Courtesy of Digital:Slurp. Programming Interview Questions. So you want to know what they are going to ask?
Or maybe you are looking for questions to ask? Here are some programming questions or puzzles often asked in programming interviews. There are usually more than one answer to these questions. Some of them are open ended questions to test how you think and communicate a technical point. Popular topics are: A Beginner’s Guide to Design Patterns. Ever wondered what design patterns are?
In this article, I'll explain why design patterns are important, and will provide some examples, in PHP, of when and why they should be used. Fyels - The worlds simplest file sharing site. BOINC Combined Statistics: BOINC. Creating Music Components in Java. ResizeMyBrowser. Protect Your Privacy When Downloading - Lifehacker. Langton's Ant. A 4-state two-dimensional Turing machine invented in the 1980s.
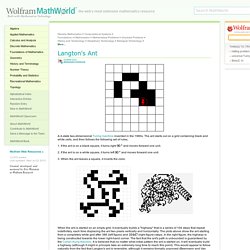
The ant starts out on a grid containing black and white cells, and then follows the following set of rules. Windows CMD Commands - CMD Network Commands. These document is under the: GNU Free Documentation License Windows CMD (Command prompt) DOS The Windows Command line interface can be accessed by running the CMD.exe that is located in the "system32" folder in you Windows folder.The most common way to access this interface is to type "cmd" in the run dialoge box, then click the ok button.The most common basic & advanced commands in alphabetical order are: * These commands are built into the CMD Shell, all others are seperate exe files that are cmd based apps that can be run from other software other than CMD.

IT Security Best Practices (How-To) Metasploit Unleashed By Offensive Security. Pwnat - NAT to NAT client-server communication. Home page (more sweet code) || follow my twitter || blog || email me || samy kamkar pwnat, pronounced "poe-nat", is a tool that allows any number of clients behind NATs to communicate with a server behind a separate NAT with *no* port forwarding and *no* DMZ setup on any routers in order to directly communicate with each other.

The server does not need to know anything about the clients trying to connect. Simply put, this is a proxy server that works behind a NAT, even when the client is behind a NAT, without any 3rd party. Read the paper, "Autonomous NAT Traversal", joint work with Christian Grothoff, Nathan S. Evans, and Andreas Müller published by IEEE at the IEEE P2P'10 Conference (bib, pdf) There is no middle man, no proxy, no 3rd party, no UPnP/STUN/ICE required, no spoofing, and no DNS tricks. Pwnat will work on most *nix operating systems, and potentially Windows via cygwin. Usage: . Adding Custom Google Maps to Your Website. Maps are often placed on a company website to help customers find their way there.

For that, Google Maps is excellent. But wouldn’t it be nice to add your company logo, parking lots, train stations, etc. to the map, to help the customer even more? It is very simple, and in this article I am going to show you how. I Hear U (IHU) Project Homepage.