

Making Use of the Trancend WiFi SD Card. Advanced Transcend WiFiSD hacking - Dmitry Grinberg. A few people have already writen about the Transcend WiFiSD card and its hackability.

I wanted to play around with one, so I ordered one online and spent the last few days playing with it. As it had been pointed out, the card is rather insecure, and the scripts in it can be exploited. That is not the route I took. Transcend has a "GPL release package" for the card on their support website.
They are not even close to complying with the GPL. The bootloader (u-boot, whose sources Transcend did NOT provide) reads the ramdisk into RAM, reads the kernel into ram, and jumps to it. We need a way to flash this thing safely and effectively. Unpacking the existing ramdisk is trivial, just run this command: sudo sh -c 'mkdir unpacked && cd unpacked && cat .. The root privileges are needed since otherwise cpio will not be able to create the devnodes under "dev" and when you re-pack the image, it will not work.
LED Pocketwatch v1.0. <update 12/11/10> Ok, here's the current status: Circuit design and routing for v2.0 is complete.

I've also gotten back in touch with the manufacturer of the cases I intend to use. I've got some free time coming up over christmas, so I'm hoping that I can get the new webpage up, order some boards and get a prototype assembled in the early new year. A big thank you to people who continue to send me emails asking for design files or yelling at me to get a move on etc. Your enthusiasm is noted! However, I am right in the middle of my post-doctoral appointment and spare time is rare and precious - I don't want this project to become a second job!
<update 14/7/10> Thank you all for your emails - no, this project is not dead! V2.0 is underway and will have its own page soon. If you know of a source of quality, stylish 52mm pocket watch cases, feel free to drop me a line and let me know! 1. 2. Perseids Meteor Reflection Observations with the RTL-SDR. In this video YouTube user ek6rsc shows a timelapse of meteor reflection observations during the yearly Perseids meteor shower which occurred in 2013 during August 10-15.
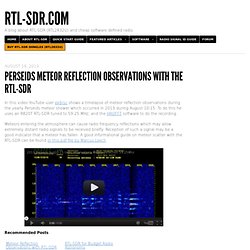
To do this he uses an R820T RTL-SDR tuned to 59.25 MHz, and the HROFFT software to do the recording. Meteors entering the atmosphere can cause radio frequency reflections which may allow extremely distant radio signals to be received briefly. MSRaynsford. Index of /download/SmartCardReader/DEKIMADO/NFC/SDK. ROFI parts list. Project Biped. Don't Try This At Home, That's What The Hackerspace is For! Imprimante 3D.
Nixie clock. Raspberry. Gadget Teardowns. Massachusetts, The people of Massachusetts have always stood up for their right to repair.
In 2012, voters passed a law that ensured residents' right to repair their car wherever they wanted. Now, it's time to do the same for electronics. With the Digital Right to Repair Bill, H.3383, we have a chance to guarantee our right to repair electronics — like smartphones, computers, and even farm equipment. We have a chance to help the environment and stand up for local repair jobs—the corner mom-and-pop repair shops that keep getting squeezed out by manufacturers. The Digital Right to Repair Bill requires manufacturers to provide owners and independent repair businesses with fair access to service information, security updates, and replacement parts.
If you agree with us, find out who represents you in the Massachusetts legislature. Copier une puce RFID avec cet émulateur. Le montage RFIDemulator, créé par l’allemand Alexander Guthman, permet de simuler n’importe quelle puce RFID à 125 kHz compatible EM4001.
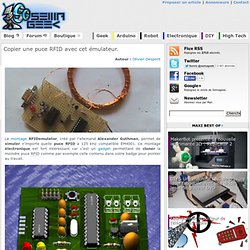
Ce montage électronique est fort intéressant car c’est un gadget permettant de cloner la moindre puce RFID comme par exemple celle contenu dans votre badge pour pointer au travail. Au niveau de la conception, pas un composant compliqué, on retrouve principalement un MAX232 avec sa batterie de condensateurs pour la liaison série et un micro-contrôleur Atmel ATmega8 gère l’ensemble. On peut d’ailleurs voir sur le schéma suivant la simplicité du montage. Avant toute chose il faut capturer l’ID 64 bits d’une puce puce RFID compatible EM4001 à l’aide d’un lecteur RFID.
Un programme (disponible sur le site de l’auteur) permet alors d’envoyer ce code via une liaison série RS232 à l’émulateur, qui va alors transmettre via la bobine de cuivre ce code ID 64 bits codé en Manchester. Vous pouvez retrouver l’ensemble du projet sur le site : alexanderguthmann.de. Parasiting the bladerunner wifli.
In December of 2011 my employer got me a Bladerunner Wifli helicopter for Christmas and I proceeded to investigate the device. Turns out it was running linux 2.6.21 and others had already started on reverse-engineering the packets used to control it . I began to dream about performing a switchroot to a flash drive and being able to record/stream video as I flew it around. *Interactive Toy Concepts is apparently releasing a ‘WiSpy’ version with video streaming in the fall of 2012*