

Crypto. Digital forensics. Online TraceRoute - SubnetOnline.com. "Your online IP subnet calculator and network tools collection...
" Traceroute is a computer network tool used to determine the route taken by packets across an IP network. The traceroute tool is available on practically all Unix-like operating systems. Variants with similar functionality are also available, such as tracepath on modern Linux installations and tracert on Microsoft Windows operating systems. Windows NT-based operating systems also provide pathping, which provides similar functionality. Source: WikiPedia.
Untitled.
Security and Analysis Tools. How mitmproxy works — mitmproxy 2.0.0 documentation. All About Skimmers. The series I’ve written about ATM skimmers, gas pump skimmers and other related fraud devices have become by far the most-read posts on this blog.

I put this gallery together to showcase the entire series, and to give others a handy place to reference all of these stories in one place. Click the headline or the image associated with each blurb for the full story. Pen-testing. Mobile security. Understanding What Constitutes Your Attack Surface. Home » Featured Articles » Understanding What Constitutes Your Attack Surface In the first article in this series, we discussed a little about Understanding Attack Surface Analytics, and in this second installment we will examine exactly what constitutes your attack surface.
Put simply, your attack surface is the sum of your security risk exposure. Put another way, it is the aggregate of all known, unknown and potential vulnerabilities and controls across all software, hardware, firmware and networks. A smaller attack surface can help make your organization less exploitable, reducing risk. A typical attack surface has complex interrelationships among three main areas of exposure: software attack surface, network attack surface and the often-overlooked human attack surface.
The Software Attack Surface. The New Personal Attack Surface.
Every trick in the book: how hackers take over your computer. By Rich Pasco Spammers will use every trick in the book to get you to click on their links to malicious web sites, or to open their malicious attachments, or to divulge personal information for identity theft.

Below are just a few examples. As P.T. Free Penetration Testing and Ethical Hacking Training Course. The control of information is something the elite always does … Information, knowledge, is power.” – Tom Clancy No longer will money have dominion over our ability to learn.

Penetration testing and ethical hacking are skill sets as in-demand as anything else in the Cyber Security industry. Previous to Cybrary, this type of training was very expensive, and now it is free. The SQL Injection Knowledge Base. Default Databases Testing Injection False means the query is invalid (MySQL errors/missing content on website) True means the query is valid (content is displayed as usual) Given the query SELECT * FROM Table WHERE id = '1';
SEED Project.
Domain specific modelling - security. Mind Maps .... Wireless Network Review v1.5 [2013 May] View Full Size -- Image Only -- Template below.

ICT%20in%20H2020%20WP2014-15_0.pdf. Perspectives_integrating-cybersecurity-into-computer-science-curricula-final31102014.pdf. BIM Security. Fundamentals of Information Security. Data management strategy. Streaming media security. SRGwiki. Cryptography. John The Ripper Hash Formats. John the Ripper is a favourite password cracking tool of many pentesters.
There is plenty of documentation about its command line options. I’ve encountered the following problems using John the Ripper. These are not problems with the tool itself, but inherent problems with pentesting and password cracking in general. 1286: Encryptic. Adobe, however, ignored these well-known principles, and instead stored over a hundred million passwords in a reversably encrypted way, using a terrible choice of encryption methods which exposes a great deal of information about the passwords, and does not involve a salt.
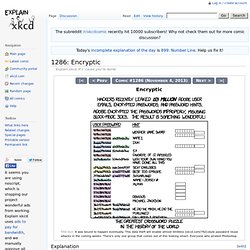
This password database was recently obtained by someone and released on the Internet. In particular, Adobe used Triple DES, an older encryption algorithm which can still be relatively secure when properly used but they used it improperly. It works on 64-bit (8 character) blocks. Assuming that the passwords are stored in plain ASCII, this means that a sequence of 8 characters in a password which starts on a character position which is a multiple of eight is always encrypted to the same result. How an epic blunder by Adobe could strengthen hand of password crackers. Four weeks ago, Adobe disclosed a sustained hack on its corporate network that threatened to spawn a wave of meaner malware attacks by giving criminals access to the raw source code for the company's widely used Acrobat and ColdFusion applications.
Now, researchers are warning the same breach could significantly strengthen the password crackers' collective hand by revealing a staggering 130 million passcodes used over the years by Adobe customers, many of them from the FBI, large corporations, and other sensitive organizations. Analyzing the Adobe leaked passwords. On October Adobe reported that some user data, including credit cards and password dumps, got stolen from their servers.
Now the passwords dump has leaked, and it’s hilarious. We (Jari Takkala and I) got hold of the files and are starting to analyze them. The files.
European Journal of Information Systems - Abstract of article: What levels of moral reasoning and values explain adherence to information security rules[quest] An empirical study. Security and Communication Networks - Early View. Keeping the UK safe in cyber space - Policies. Issue The growth of the internet has transformed our everyday lives and is an important part of our economy. The internet-related market in the UK is now estimated to be worth £82 billion a year while British businesses earn £1 in every £5 from the internet.
But with greater openness, interconnection and dependency comes greater vulnerability. The National Security Strategy categorised cyber attacks as a Tier One threat to our national security, alongside international terrorism. The threat to our national security from cyber attacks is real and growing. 93% of large corporations and 87% of small businesses reported a cyber breach in the past year. With the cost for a cyber-security breach estimated between £450,000 to £850,000 for large businesses and £35,000 to £65,000 for smaller ones, the government must look at new ways to protect businesses and make the UK more resilient to cyber attacks and crime. Actions. Drcrack - reusablesec2. Usage: drtgen <options> |Options For All Rainbow Table Types | -file <file name> (REQUIRED):The rt filename to use, not required if using -bench.