


Backtrack alternative Xiaopan OS is a small Tiny Core Linux based operating system specific for wireless penetration testing, it comes with the XFE desktop environment, a very lightweight graphical front end, the distribution can run as a live CD, from a USB thumbdrive with Unetbootin or used inside a virtual machine. Numerous wireless card controllers are supported, including Atheros and Broadcom, the most widely used chipsets. As a result of the distribution being based on Tiny Core Linux all of the .tcz precompiled packages available for Tiny Core can be installed in Xiopan using the TCL Appbrowser, non hacking utilities like games, media player, CD burner, VoIP software and Truecrypt can all be optionally added to Xiopan OS. Wifi hacking Linux distribution Xiaopan This Linux live CD is first class penetration testing tool to audit wireless access points security and replaces Beini, a very similar distribution no longer active. Xiaopan Linux WPA2 hacking Visit Xiaopan OS homepage
Essential Wireless Hacking Tools By Daniel V. Hoffman, CISSP, CWNA, CEH Anyone interested in gaining a deeper knowledge of wireless security and exploiting vulnerabilities will need a good set of base tools with which to work. Fortunately, there are an abundance of free tools available on the Internet. Finding Wireless Networks Locating a wireless network is the first step in trying to exploit it. Network Stumbler a.k.a NetStumbler – This Windows based tool easily finds wireless signals being broadcast within range – A must have. (NetStumbler Screenshot) Kismet – One of the key functional elements missing from NetStumbler is the ability to display Wireless Networks that are not broadcasting their SSID. (Kismet Screenshot) Attaching to the Found Wireless Network Once you’ve found a wireless network, the next step is to try to connect to it. Airsnort – This is a very easy to use tool that can be used to sniff and crack WEP keys. (Screenshot of Airsnort in Action) (coWPAtty Options Screenshot) (ASLeap Options Screenshot)
Backtrack 6 alias Kali Linux est là ! Backtrack 6 alias Kali Linux est là ! Avis aux amateurs de sécurité informatique, Backtrack 6 est enfin sortie !!! Alors qu'elles sont les nouveautés de cette distrib ? Et bien tout d'abord, ça ne s'appelle plus Backtrack, mais Kali Linux. Et du coup, on passe en version 1.0. Kali Linux est basée sur une Debian plutôt qu'Ubuntu comme précédemment et ses dépôts se synchronisent avec les dépôts officiels de Debian, 4 fois par jour afin que la distrib soit toujours à jour. Tous les packages inclus dans Kali sont donc supportés par n'importe quelle Debian et ça c'est plutôt une bonne nouvelle.Il est aussi possible de personnaliser sa propre distrib live directement pour disposer d'une ISO qui correspond au mieux à vos besoins. apt-get install git live-build cdebootstrapgit clone live-build-configlb configlb build Bref, de la bonne came à télécharger sur leur nouveau site tout beau, tout frais. Source Vous avez aimé cet article ?
Top Ten Linux Penetration Testing Distributions By Henry Dalziel | Cyber Security Blogger | Concise Courses Post written on November 7, 2012 Update! (January 2015) This post is very old now…. Something much more interesting – and up to date – is our list of 16 Hacker Distro’s. We list all the major Linux Pentesting/ Hacker Distro’s in one place. Also, go and check out our ‘2015 Best Linux Hacking OS Poll’ – voted on by you guys: that’s here. Thanks for stopping by. In summary, our new 2015 Linux Hacker Distro Directory contains the following: As of early 2012 BackTrack was used by over four million amateur and professional security researchers and professionals. Update January 2015: Related Post: Poll! Update May 2013: Related Post: Poll! Update February 2013: Owing to some great comments below we edited this post so it has now become the “12 Best Linux Penetration Distro List!” 1. The mamma or best known of Linux pentesting distros. BackTrack is based on the ever-popular Ubuntu. 2. 3. BackBox is getting more popular by the day. 4. 5. 6. 7.
Free Password Crackers A password cracker program, often called a password recovery tool or a password unlocker/reset tool, is a software program used to "crack" a password, either by discovering the password outright, bypassing the encryption by removing the password, or bypassing the need for a password by changing the way the program or file works. If you've lost your password to something like Windows or an encrypted file, and the normal means to change the password won't work, a password cracker program might be able to help. Fully functional, completely free password crackers do exist alongside the many premium password crackers that you might find doing a quick search. Important: Password crackers and other kinds of password recovery and finder tools are legitimate programs to help discover or reset lost passwords.
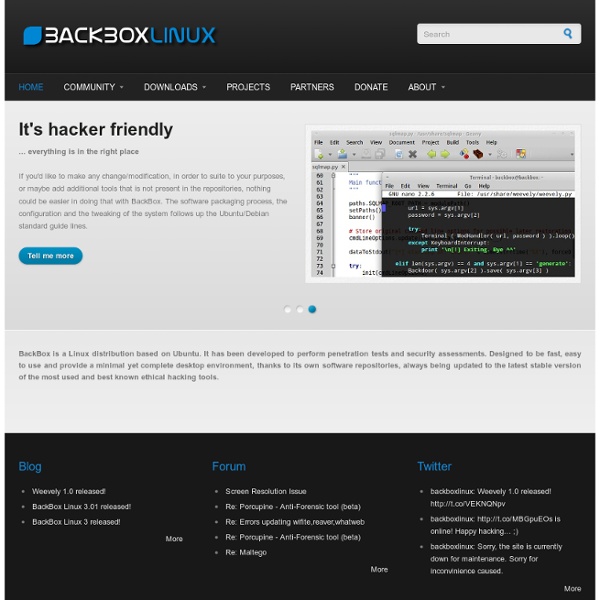
BackBox BackBox is a Linux distribution for penetration testers based on Ubuntu.It is one of the lightest and fastest Linux distros that are currently available on the Internet.It uses the Xfce component for the desktop environment and is suitable for web application analysis,network analysis,vulnerability assessments and penetration tests. The interesting part with the BackBox team is that if there is a tool that is not inside the repositories you can make a request and they will include it. Some of the features that offers are: Forensic AnalysisInformation GatheringVulnerability AssessmentExploitationPrivilege EscalationMaintaining AccessSocial EngineeringWireless AnalysisDocumentation and ReportingReverse EngineeringVoIP Analysis Tool List You can find most of the well know tools like: MetasploitNmapJohn the ripperWiresharkDradisEttercapSocial Engineering Toolkitw3af Website: Image: BackBox 2 Menu Like this: Like Loading...
Play And Convert Any Multimedia File In this post I will list some problems many people have with multimedia formats and one solution. But let's start with the problems: * I have a video file and I want to extract the audio part.* I have an AVI video and I want to put it on my web page in a format optimized for the web.* How can I transfer videos from my PC to my mobile phone that supports only 3gp format?* I have an AVI/MOV/ MP4/WMV file and I want to convert it to AVI/MOV/ MP4/WMV.* How can I save on my disk MMS and RTSP streams?* Ok, I downloaded a file from YouTube as a flv file, but how can I encode it in a format that can be viewed in any player? There's only one answer to these frustrations and many others: SUPER. SUPER is a free program that lets you view and convert almost any multimedia format you've ever heard. Let's see how easy is to save a YouTube video as an AVI file. Step 1. Although SUPER has a very basic interface, it's very powerful. Update.
Top 15 Open Source/Free Security/Hacking Tools 1. Nmap Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. 2. Wireshark is a network protocol analyzer. 3. Metasploit Community Edition simplifies network discovery and vulnerability verification for specific exploits, increasing the effectiveness of vulnerability scanners. 4. Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6400 potentially dangerous files/CGIs, checks for outdated versions of over 1200 servers, and version specific problems on over 270 servers. 5. John the Ripper is a fast password cracker, currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS. 6. ettercap Ettercap is a comprehensive suite for man in the middle attacks. 7. The Nexpose Community Edition is a free, single-user vulnerability management solution. 8. 9. 10. w3af w3af is a Web Application Attack and Audit Framework. 11. hping 13.