

Aaron Swartz Suicide. In the Wake of Aaron Swartz's Death, Let's Fix Draconian Computer Crime Law. Outpourings of grief and calls for change continue to flood the Internet after the suicide of Aaron Swartz, only 26 years old.
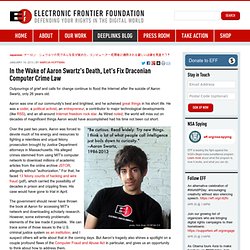
Aaron was one of our community's best and brightest, and he acheived great things in his short life. He was a coder, a political activist, an entrepreneur, a contributor to major technological developments (like RSS), and an all-around Internet freedom rock star. As Wired noted, the world will miss out on decades of magnificent things Aaron would have accomplished had his time not been cut short. Over the past two years, Aaron was forced to devote much of his energy and resources to fighting a relentless and unjust felony prosecution brought by Justice Department attorneys in Massachusetts. His alleged crimes stemmed from using MIT's computer network to download millions of academic articles from the online archive JSTOR, allegedly without "authorization. " Problem 1: Hacking laws are too broad, and too vague An infamous example is United States v.
The Upshot. Feds Charge Activist with 13 Felonies for Rogue Downloading of Academic Articles. Federal prosectors added nine new felony counts against well-known coder and activist Aaron Swartz, who was charged last year for allegedly breaching hacking laws by downloading millions of academic articles from a subscription database via an open connection at MIT.
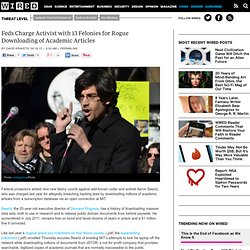
Swartz, the 25-year-old executive director of Demand Progress, has a history of downloading massive data sets, both to use in research and to release public domain documents from behind paywalls. He surrendered in July 2011, remains free on bond and faces dozens of years in prison and a $1 million fine if convicted. Like last year’s original grand jury indictment on four felony counts, (.pdf) the superseding indictment (.pdf) unveiled Thursday accuses Swartz of evading MIT’s attempts to kick his laptop off the network while downloading millions of documents from JSTOR, a not-for-profit company that provides searchable, digitized copies of academic journals that are normally inaccessible to the public.
Fourth Circuit joins courts limiting employers' use of the Computer Fraud and Abuse Act to prosecute disloyal employees. The federal Computer Fraud and Abuse Act (CFAA) allows an employer to bring a civil action against an employee who accesses the employer's computers "without authorization" or in a manner that "exceeds authorized access.
" Although the CFAA is primarily a criminal statute designed to combat hacking, employers often bring claims under the CFAA when a "disloyal employee" (typically, an employee who has accepted employment with a competitor) downloads or emails confidential information for the benefit of the employer's competitor. In WEC Carolina Energy Solutions LLC v. Miller, the U.S. Court of Appeals for the Fourth Circuit confronted such a situation.
According to the complaint, shortly before the employee resigned from his position as project director for WEC, he downloaded to his personal computer and emailed to himself or his assistant a substantial number of WEC's confidential documents. The Fourth Circuit affirmed the district court's holding. The lesson for employers is twofold. Employers beware: Fourth Circuit adopts narrow interpretation of Computer Fraud and Abuse Act. Mike Miller was an employee of WEC Carolina Energy Solutions (“WEC”).
During his employment, Miller was provided with a computer and cell phone from which he could access the company’s intranet which housed confidential, proprietary, and trade secret information. Prior to resigning in 2010, Miller allegedly downloaded a number of confidential documents, which he then proceeded to email to himself. Fourth Circuit joins courts limiting use of Computer Fraud and Abuse Act to prosecute disloyal employee. Although the Computer Fraud and Abuse Act (CFAA) is primarily a criminal statute designed to combat hacking, it allows an employer to bring a civil action against an employee who accesses the employer’s computers “without authorization” or in a manner that “exceeds authorized access.”
Employers often bring claims under the CFAA in the “disloyal employee scenario” when an employee (typically, an employee who has accepted employment with a competitor) downloads or emails to himself confidential information for the benefit of a competitor. In WEC Carolina Energy Solutions LLC v. Miller, the Fourth Circuit Court of Appeals confronted such a situation.